Android application hardening method
A method calling and being called technology, applied in the field of information security, can solve problems such as difficult for ordinary developers to use, unsatisfactory protection effect, low operation level, etc., to achieve the effect of expanding the scope of application, increasing the difficulty of reverse engineering, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention clearer, the technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the drawings in the embodiments of the present invention. Obviously, the described embodiments It is a part of embodiments of the present invention, but not all embodiments. The embodiments of the present invention and all other embodiments obtained by persons of ordinary skill in the art without creative efforts all belong to the protection scope of the present invention.
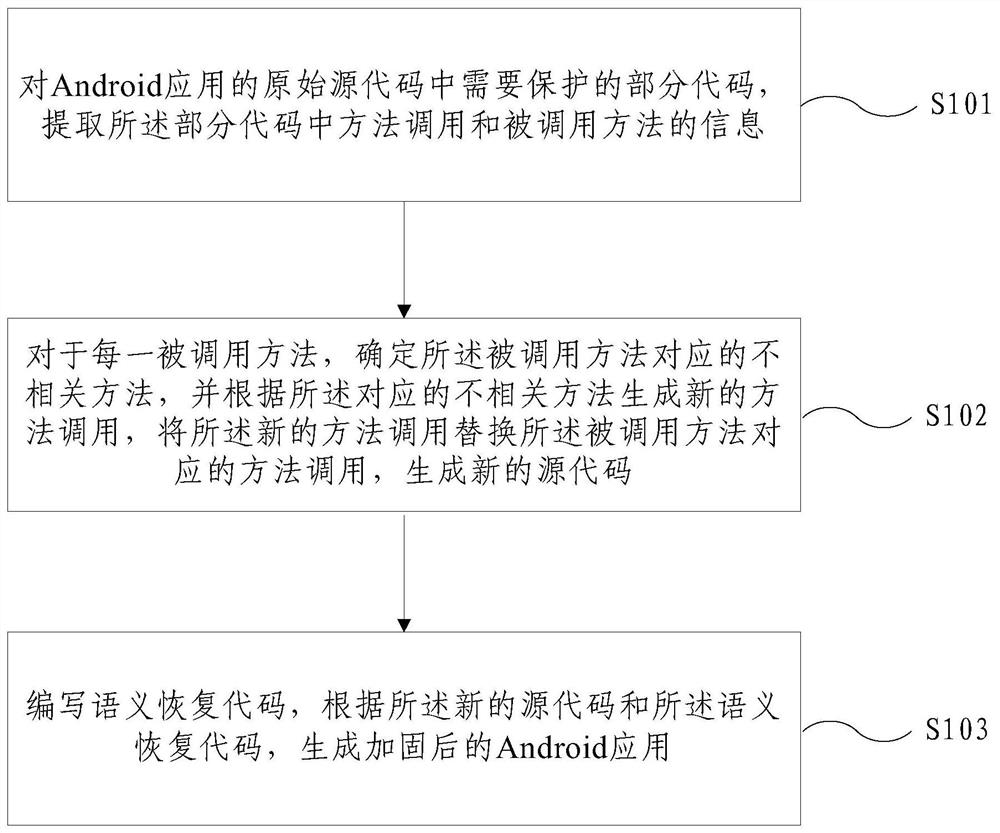
[0016] In order to overcome the above-mentioned problems in the prior art, an embodiment of the present invention provides an Android application hardening method. The inventive idea is to hide the original method by using the principle that the Android device-side compiler dynamically assigns the sequence numbers in the link list of all global Java me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com