A method for generating a unique ID primary key through distributed software
A software generation and distributed technology, applied in the direction of software design, etc., can solve the problems of poor readability, bulky, inconvenient indexing, etc., to achieve the effect of ensuring readability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
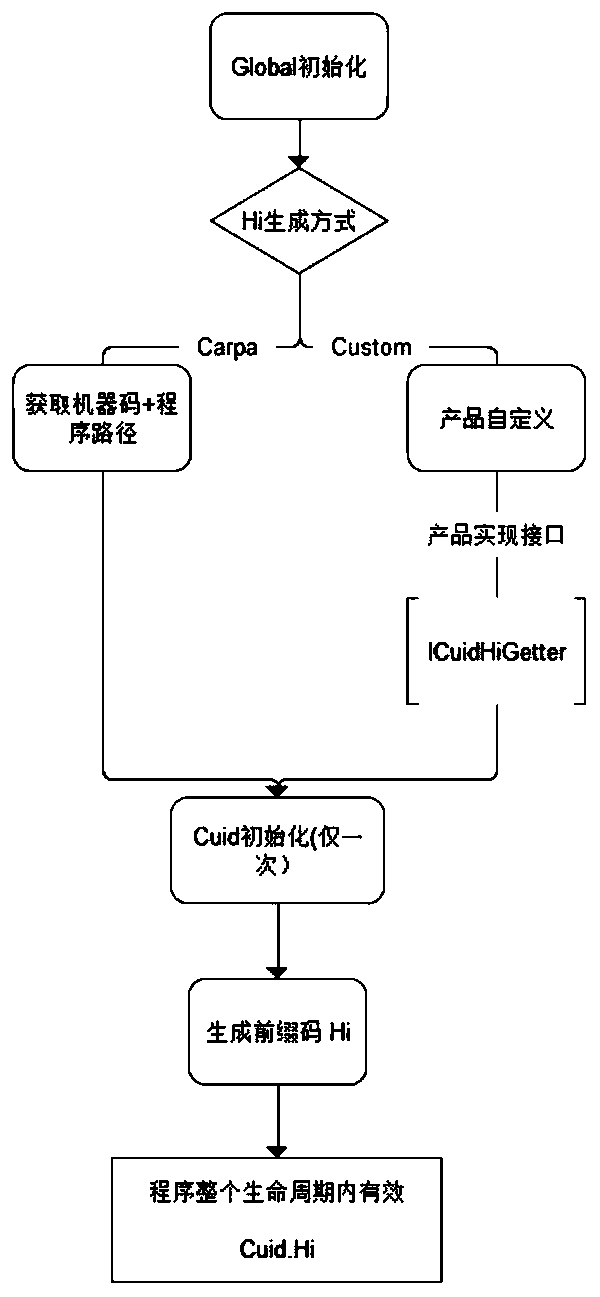
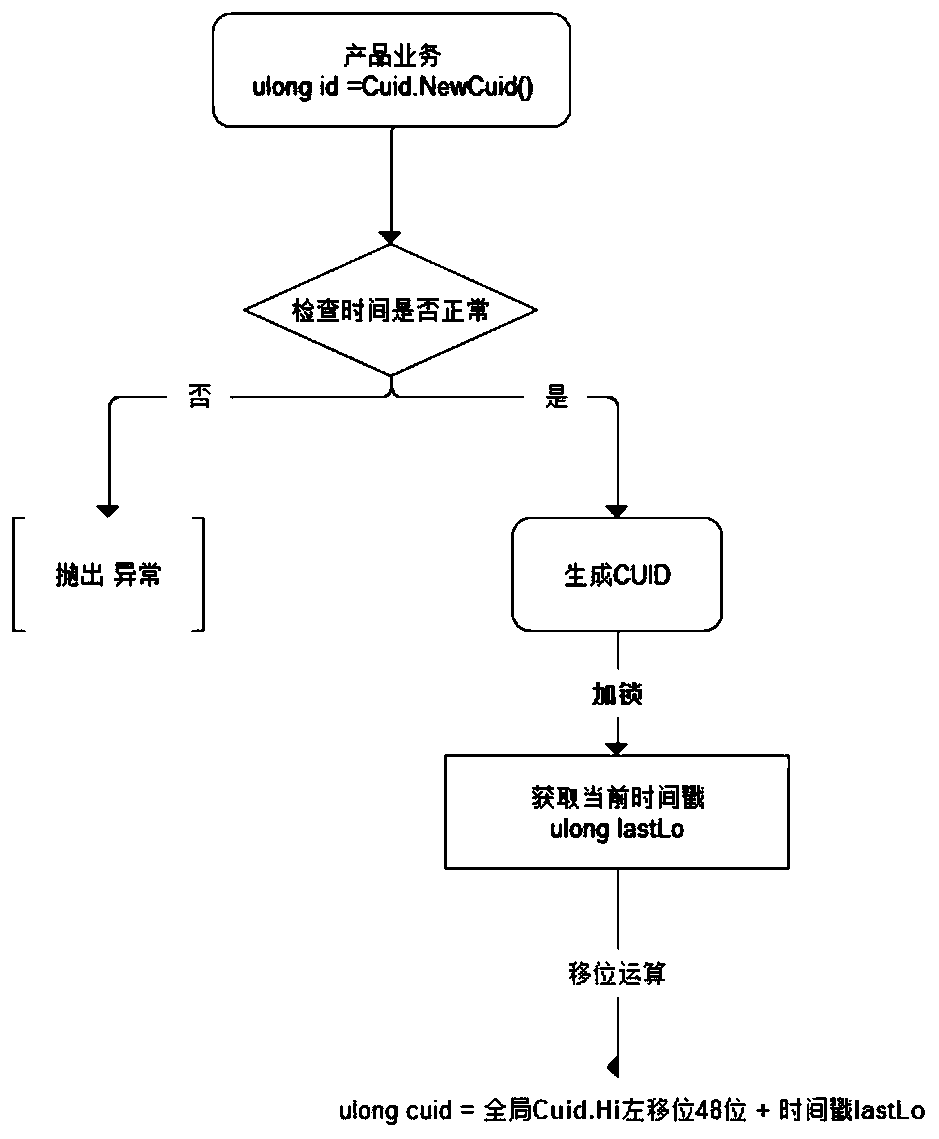
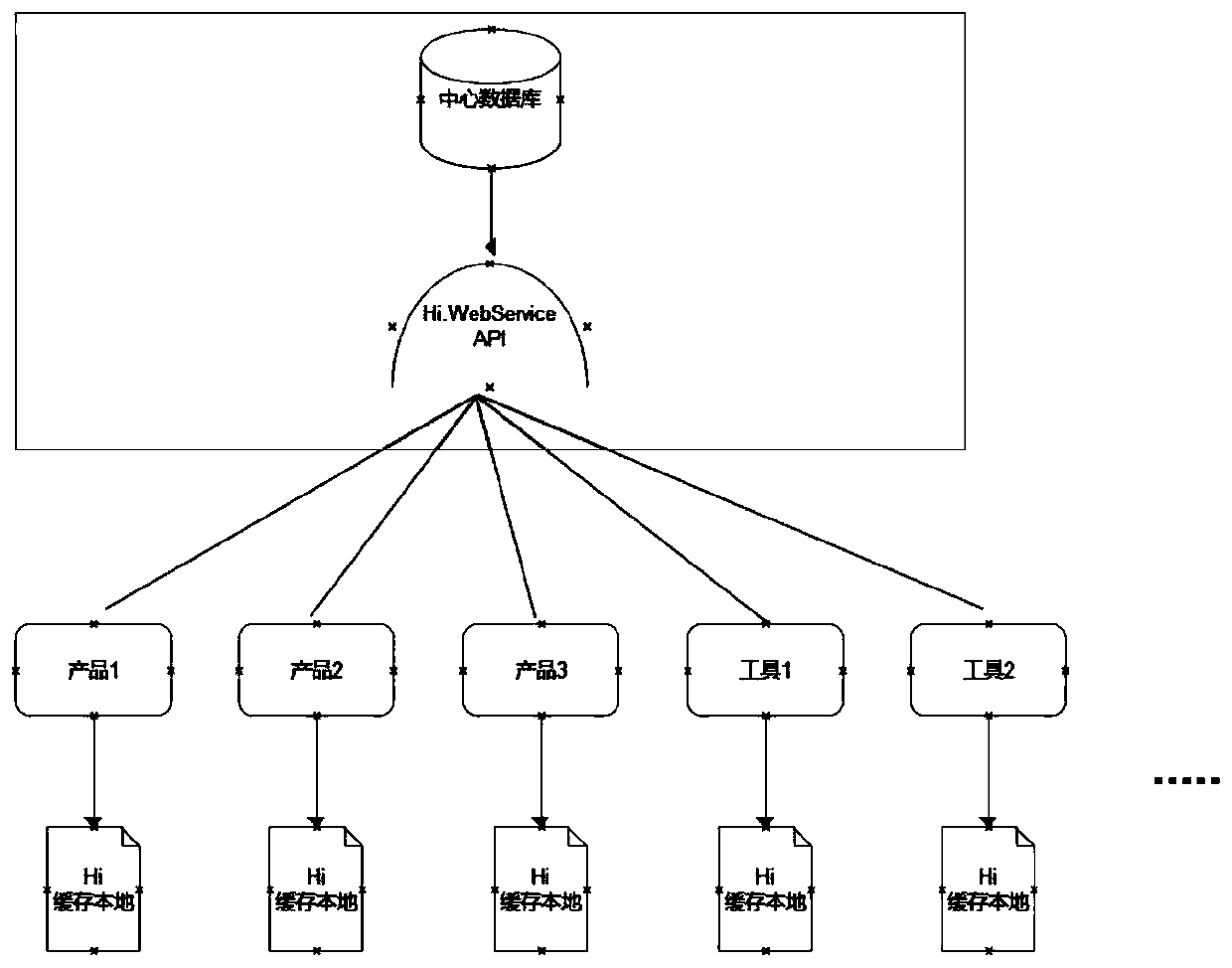
[0025] The present invention is mainly based on three development language environments of .Net, Java, and NodeJs. This embodiment is mainly introduced based on the .Net language. In addition, this embodiment is specifically introduced in detail with a 64-bit ULONG numerical type CUID, a total of 8 bytes, in order to achieve an incremental effect, the timestamp occupies 6 bytes, and the prefix code Hi occupies 2 bytes. The uniqueness between different deployments is guaranteed, and the timestamp is incremental, accurate to the subtle level, which can ensure that different timestamps are generated under the same deployment. The 2-byte prefix code space can generate theoretically 2 to the 16th power ≈ 65536 prefix codes, and each deployment only needs to allocate one Hi, and different prefix codes can determine that each machine generates a different CUID, which is enough to satisfy a single A distributed deployment environment for programs.
[0026] The specific algorithm of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com