Attack intelligent trapping system and method based on virtualization
A virtualized and intelligent technology, applied in the field of Internet security, can solve problems such as honeypot structure adjustment, high security protection cost, and inability to dynamically change decoy scenarios
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples.
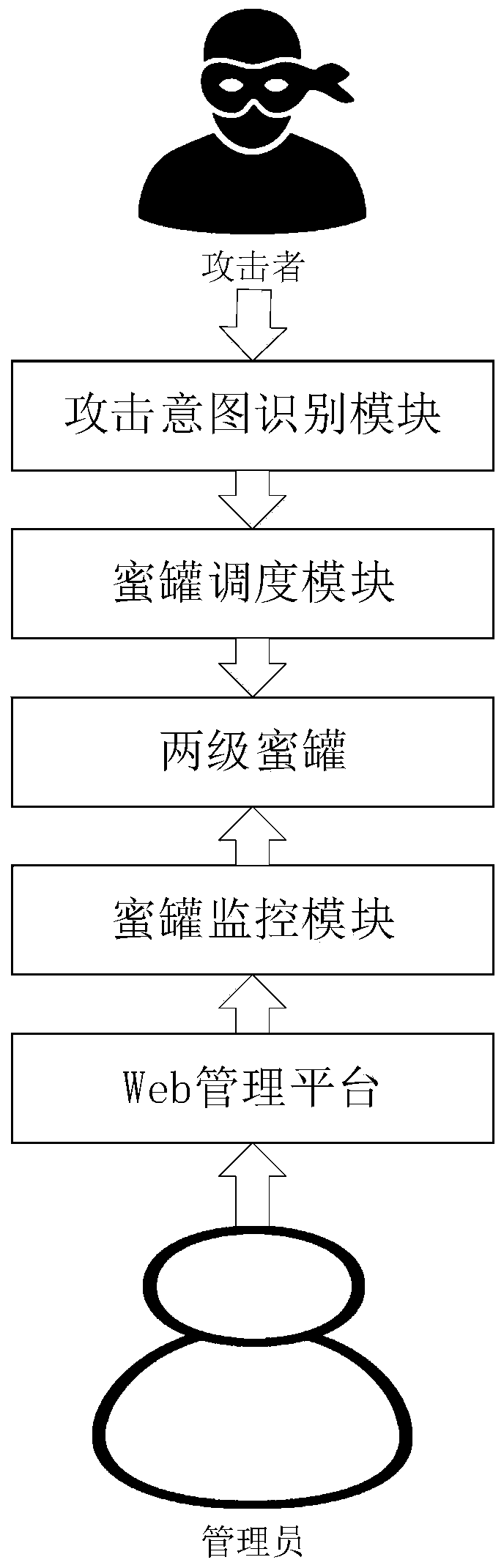
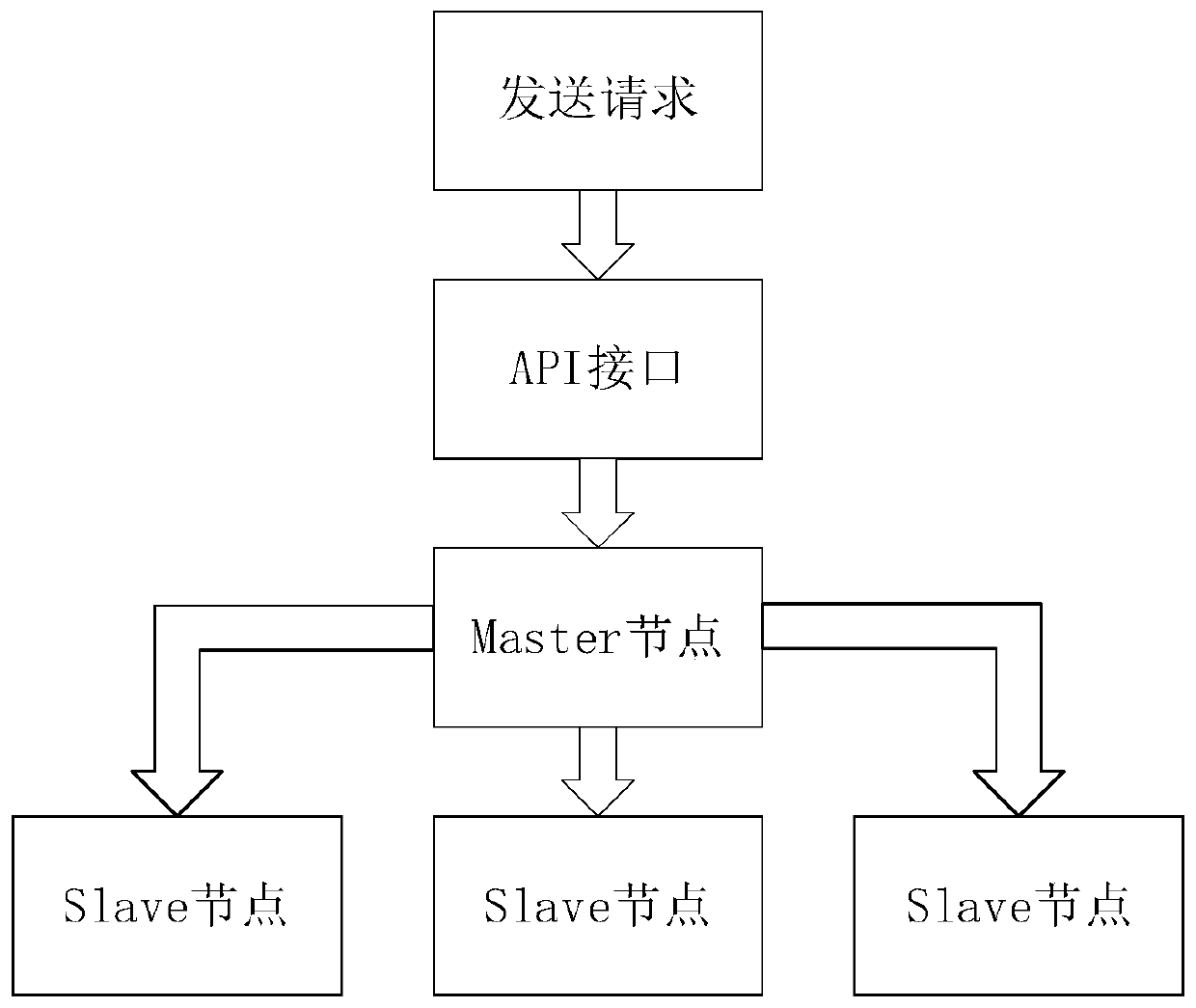
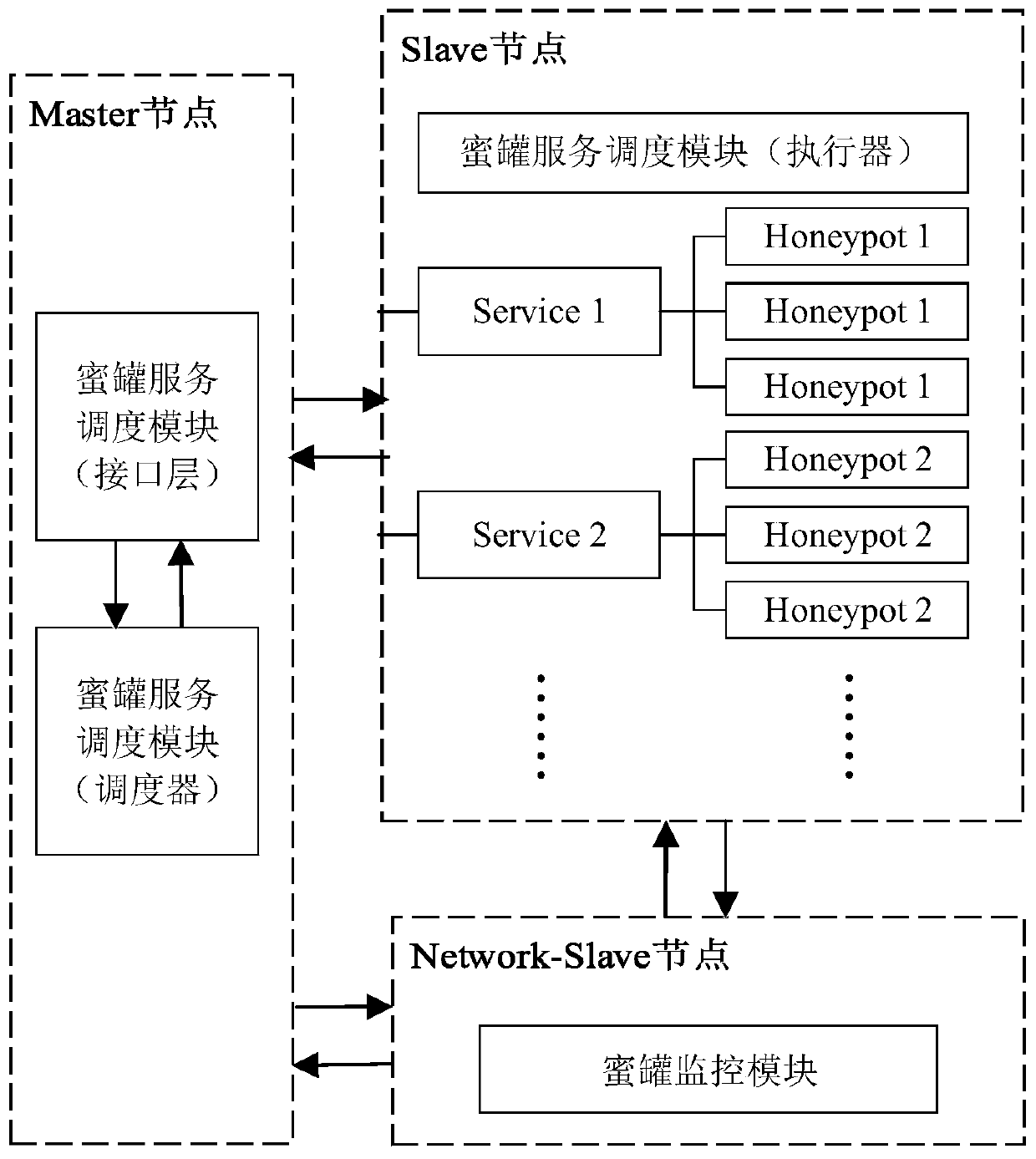
[0040] Such as figure 1As shown, the system consists of five modules, which are two-level honeypots composed of various honeypots, attack intent identification module, honeypot scheduling module, honeypot monitoring module and Web management platform. The five modules are centered on two-level honeypots, and the final operation relies on changing the state of the honeypot to achieve intelligent deception, and how to change the state of the honeypot is realized through the honeypot scheduling module, which is the core of the system. The basic functions, that is to say, the main functions of the present invention can be realized by the two-level honeypot, the attack intention identification module and the honeypot scheduling module.
[0041] specifically:
[0042] Two-level honeypots, including first-level honeypots and second-level honeypots, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com