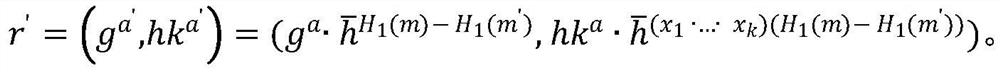Collision Calculation Method of Chameleon Hash Function and Editable Block Chain Construction Method
A hash function and calculation method technology, applied in the field of network security, can solve problems such as network re-editing, trapdoor nodes being easily attacked or maliciously exploited
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
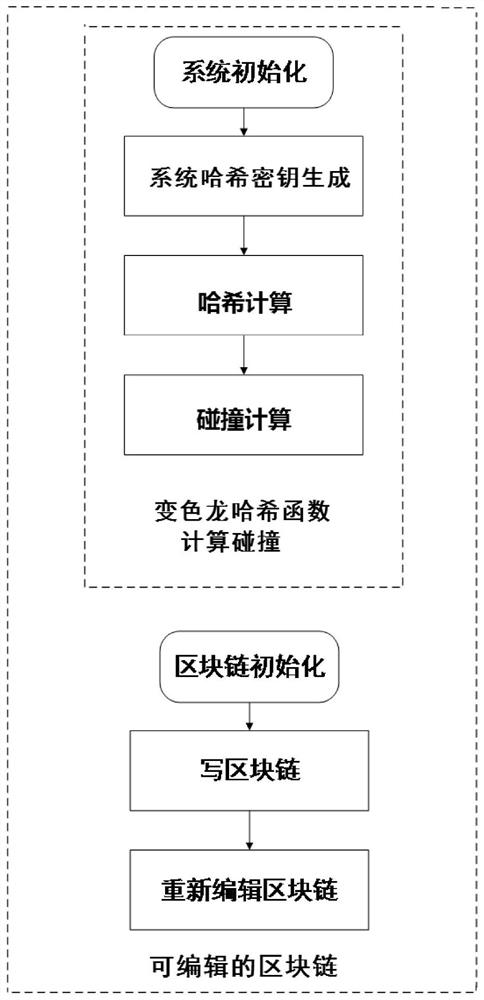
[0034] A collision calculation method of a chameleon hash function provided by a preferred embodiment of the present invention, the method is as follows:
[0035] Step a, system initialization: select the security parameter λ, and set the system public parameter param TCH . Specifically:
[0036]Choose a prime number q according to the security parameter λ, and choose a GDH group G whose order is p and whose generator is g. The GDH group here refers to such a group: on it, the Computational Diffie-Hellman (CDH) problem is difficult , but the Decisional Diffie-Hellman (DDH) problem is simple, but it can be constructed from a superbasis elliptic curve or a hyperelliptic curve on a finite field. The specific method can be found in the article "Short signature from theweil pairing" by Boneh et al . Next, select two hash functions H 0 : {0, 1} * →G * , H 1 : {0, 1} * → Z q , where Z q It is an integer group of order q, and the public parameter of the system is param TCH ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com