Efficient double-factor cross-domain authentication method based on block chain technology
An authentication method and blockchain technology, applied in the field of efficient two-factor cross-domain authentication, can solve the problems of biometric leakage, unfavorable system promotion, uneven equipment, etc., and achieve the effect of strong reliability and information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0067] An efficient two-factor cross-domain authentication method based on blockchain technology, comprising the following steps:
[0068] Step 1: Overall system architecture design;
[0069] Step 2: System workflow;
[0070] Step 21: User registration process;
[0071] Step 22: User local authentication:
[0072] Step 23: User remote cross-domain authentication.
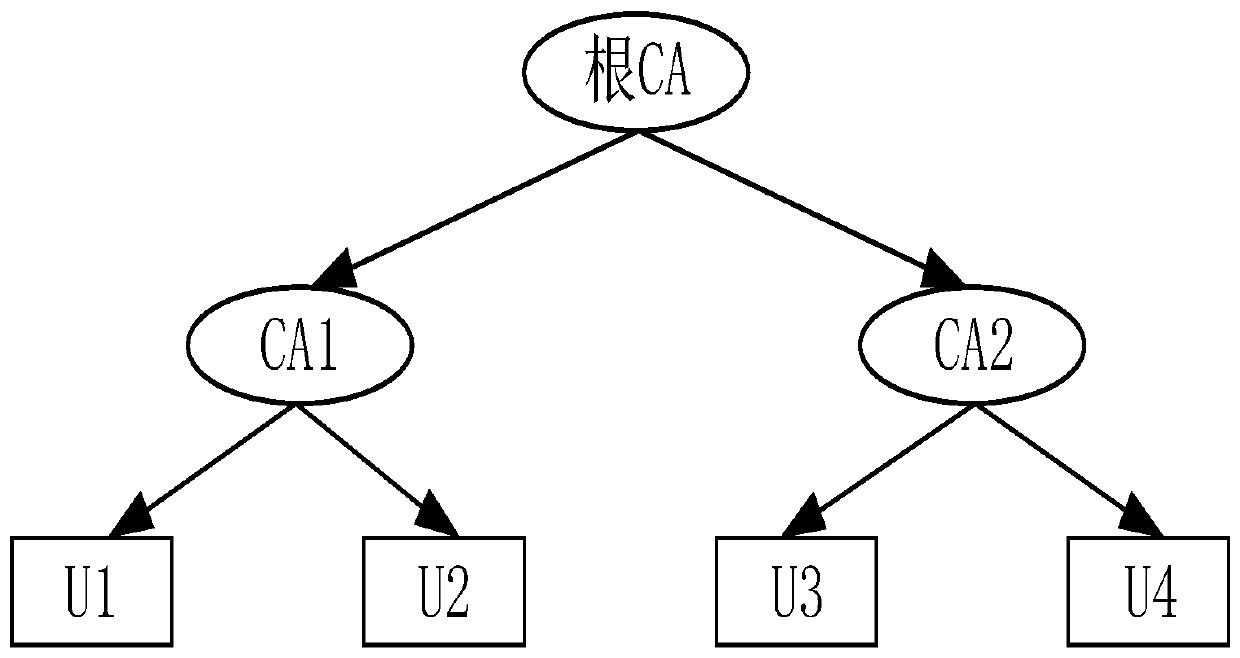
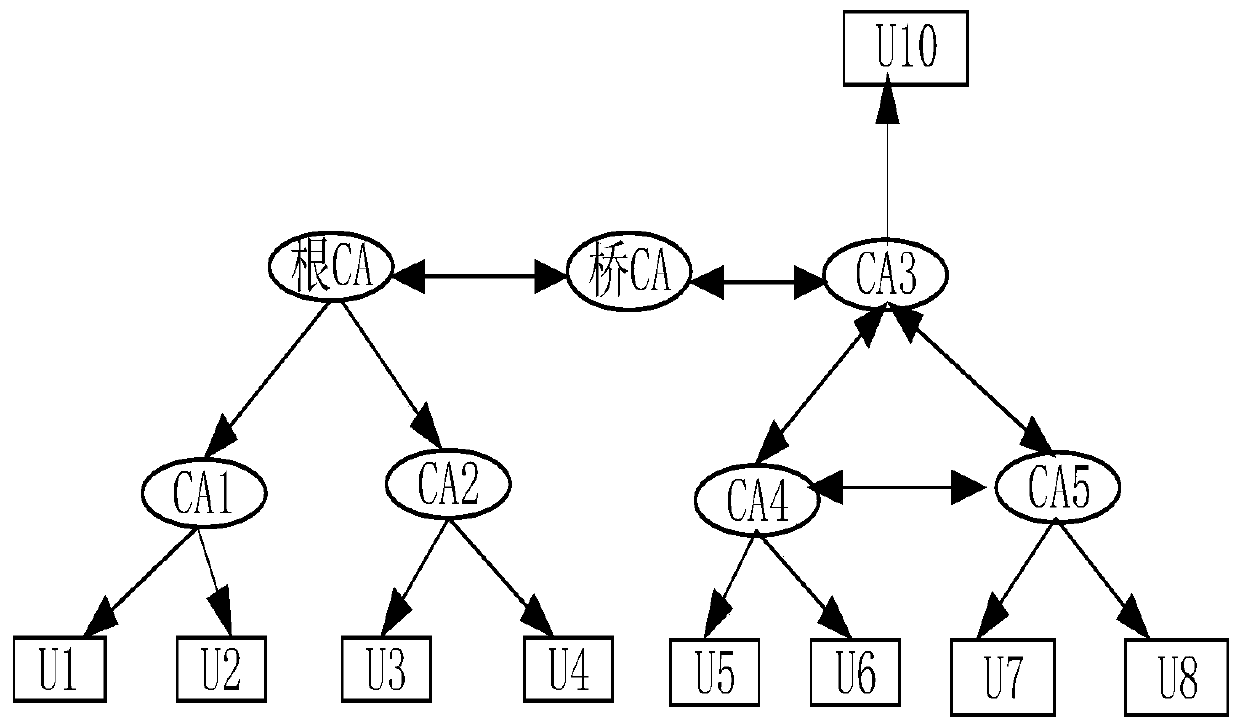
[0073] Such as figure 2 As shown, the overall architecture design of the system, according to the Diffie-Hellman algorithm A, B session key agreement mechanism steps are:
[0074] Step 11: Randomly select a large prime number n and the original root g, the two pieces of information are made public, and A and B have agreed on the two pieces of information;
[0075] Step 12: A randomly generates a number x, and calculates X=g x modn, then send X to B;
[0076] Step 13: B randomly generates a number y, and calculates Y=g y modn, then send Y to B;
[0077] Step 14: A calculates K=Y x modn;
[0078] Step 15: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com