Data review and acquisition methods, devices, systems, equipment and media
A data and data center technology, applied in the field of data processing, to achieve the effect of ensuring credibility and security, taking into account convenience, and ensuring data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
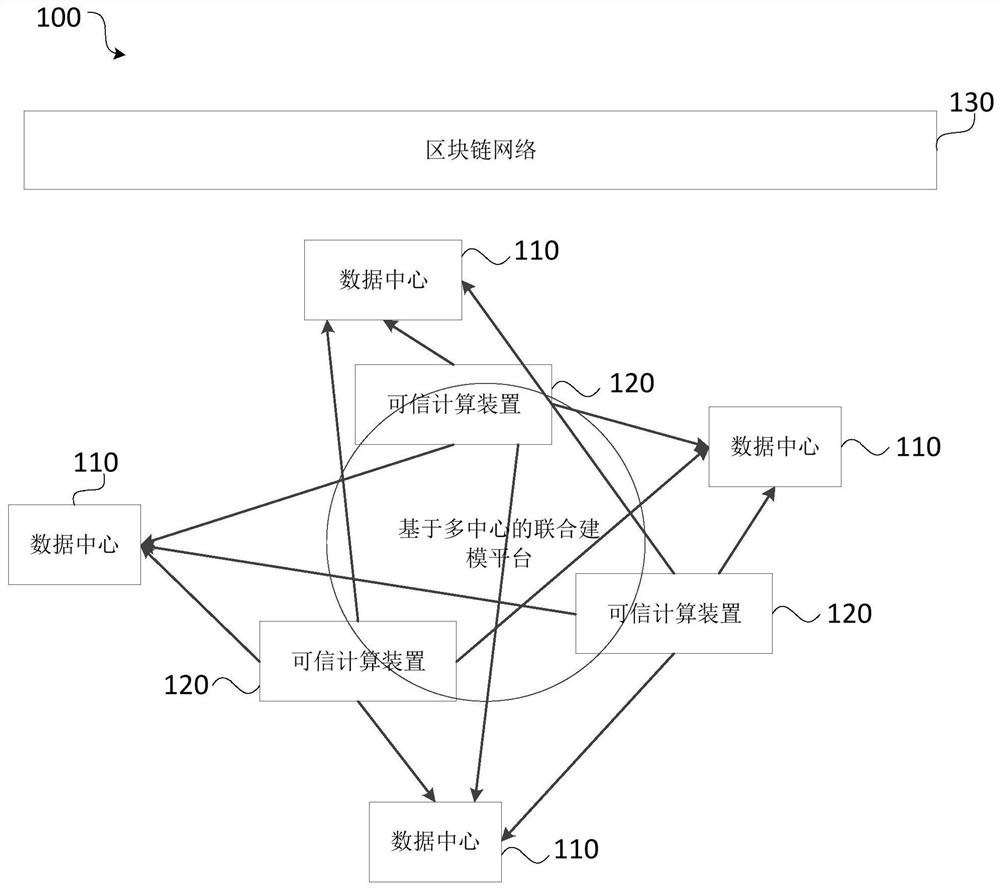
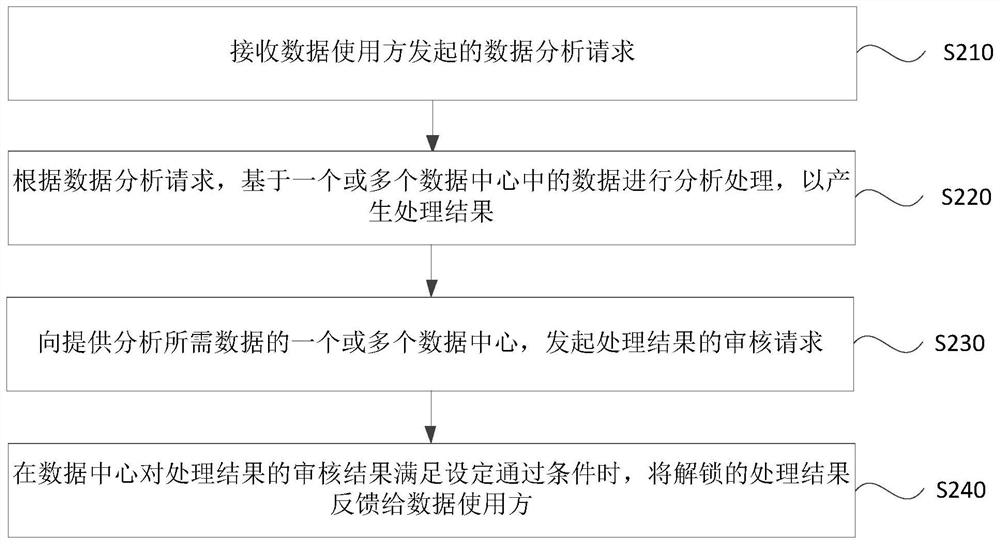
[0067] figure 2 This is a flow chart of a decentralized data auditing method provided in Embodiment 1 of the present invention. This embodiment is applicable to data processing, auditing, etc., and is especially applicable to a decentralized data processing system architecture. A scenario in which one or more trusted computing devices, multiple data centers, and data users interact to analyze and process data, and audit the processing results, so as to solve the conflicting data processing based on existing data centers. Way. The technical solutions of the embodiments of the present invention are performed by a trusted computing device, wherein the trusted computing device implements a trusted computing environment based on hardware. The method can be performed by a decentralized data auditing device, and the device can be configured in a computing device of a trusted computing device and implemented in hardware and / or software. see figure 2 , the method can specifically ...
Embodiment 2
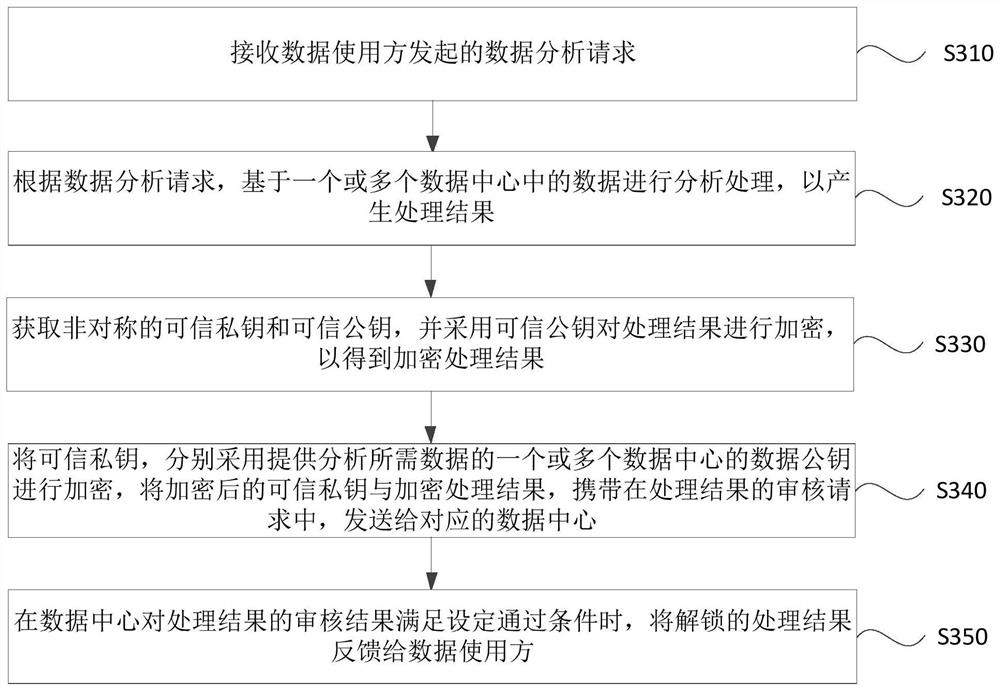
[0097] image 3 This is a flowchart of a decentralized data auditing method provided in Embodiment 2 of the present invention. This embodiment is based on the above-mentioned embodiment, and further provides one or more data centers that provide data required for analysis. Initiate an audit request for processing results to explain. see image 3 , the method can specifically include:
[0098] S310: Receive a data analysis request initiated by a data user.
[0099] S320, according to the data analysis request, perform analysis and processing based on the data in one or more data centers to generate a processing result.
[0100] S330: Obtain an asymmetric trusted private key and a trusted public key, and encrypt the processing result by using the trusted public key to obtain an encrypted processing result.
[0101] In this embodiment, the asymmetric trusted private key and trusted public key, that is, the asymmetric key pair of the trusted computing device, may be pre-genera...
Embodiment 3
[0109] Figure 4 This is a flowchart of a decentralized data auditing method provided in Embodiment 3 of the present invention. This embodiment is based on the above-mentioned embodiments, and in the case where the decentralized data processing system architecture includes a blockchain network , and further explain the request for reviewing the processing result to one or more data centers that provide the data required for the analysis. see Figure 4 , the method can specifically include:
[0110] S410: Receive a data analysis request initiated by a data user.
[0111] S420, according to the data analysis request, perform analysis and processing based on the data in one or more data centers to generate a processing result.
[0112] S430: Obtain an asymmetric trusted private key and a trusted public key, and encrypt the processing result by using the trusted public key to obtain an encrypted processing result.
[0113] S440, encrypt the trusted private key with the data pu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com