QR code security authentication method and system based on Hamming codes
An authentication method and an authentication system technology, which are applied in the field of Hamming code-based QR code security authentication methods and systems, can solve problems such as the inability to prevent the illegal operation of a single QR code, and achieve the effects of increasing the amount of embedding and increasing concealment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
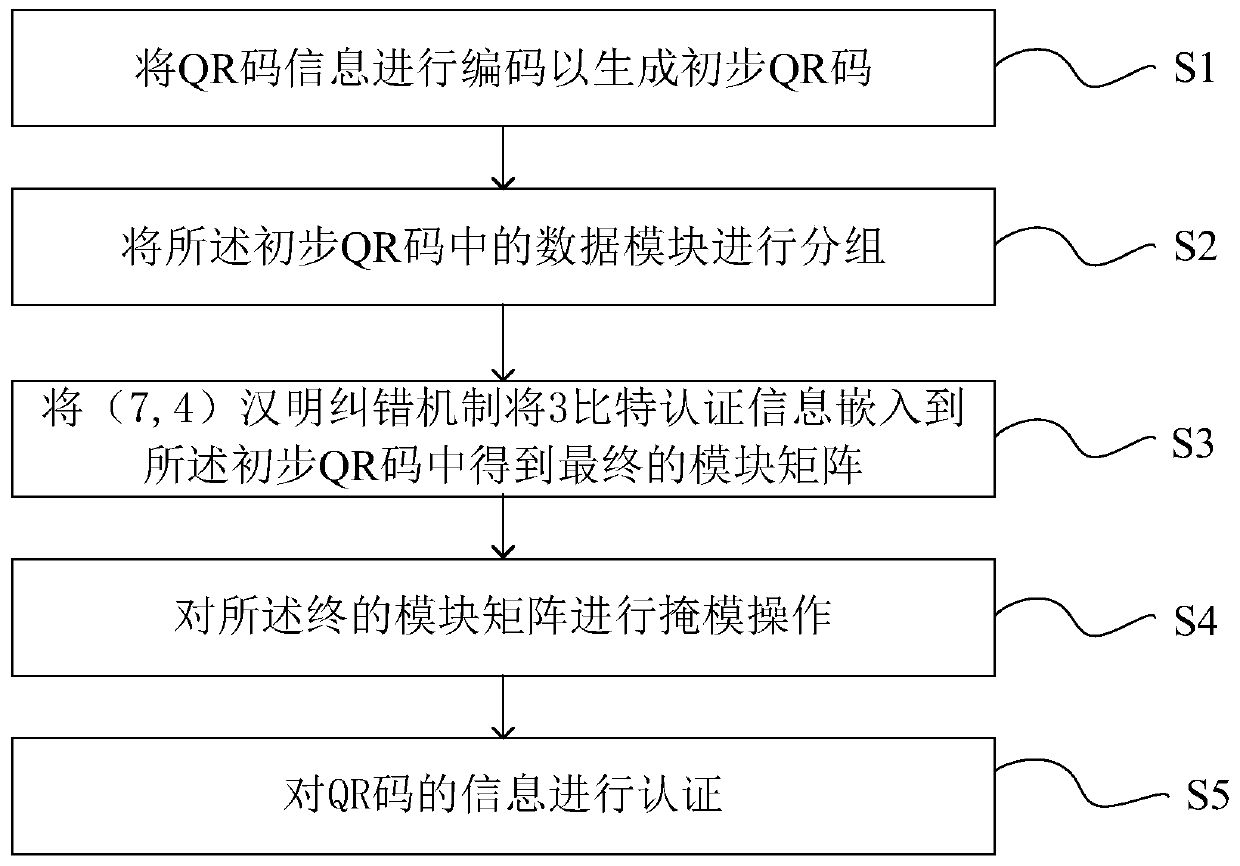
[0066] like figure 1 As shown, this embodiment proposes a Hamming code-based QR code authentication method, including:
[0067] Step S1, encode the QR code information to generate a preliminary QR code;
[0068] In the present invention, the authentication information is embedded in the preliminary QR code. Therefore, before diving into the authentication information, a preliminary QR code needs to be generated, including:
[0069] Step S1.1, data analysis: analyze the QR code information, determine the corresponding coded character type, and select an appropriate error detection and correction level;
[0070] Specifically, the QR code is provided with different versions (kinds) of 1 to 40, and each version has an inherent symbol structure (number of symbols). Symbols are the square black and white dots that make up the QR code. "Symbol structure" refers to the number of symbols in a two-dimensional code. Starting from version 1 (21 symbols x 21 symbols), it is incremente...
Embodiment 2
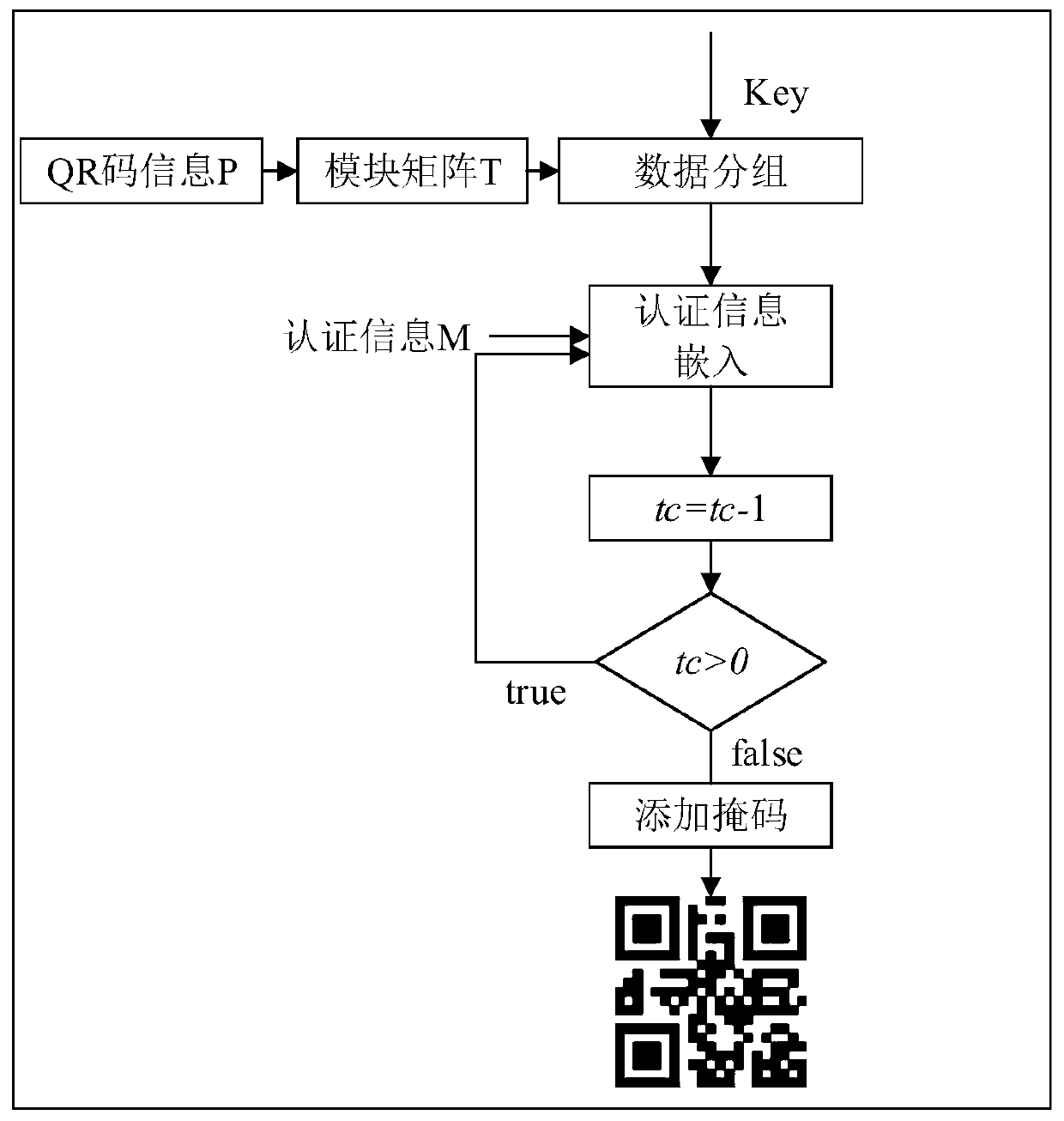
[0112] like Figure 5 As shown, this embodiment proposes a Hamming code-based QR code authentication system, including:
[0113] An encoding module for encoding the QR code information to generate a preliminary QR code;
[0114] a grouping module for grouping the data modules in the preliminary QR code;
[0115] an embedding module for embedding authentication information into the preliminary QR code to obtain a final module matrix;
[0116] a mask module for performing a mask operation on the final module matrix;
[0117] The authentication module is used to authenticate the information of the QR code.
[0118] In the present invention, the authentication information is embedded in the preliminary QR code. Therefore, before sneaking into the authentication information, a preliminary QR code needs to be generated. The encoding module specifically includes:
[0119] The data analysis module is used to analyze the QR code information, determine the corresponding coded chara...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap