Security protocol vulnerability mining method based on multiple reverse cases
A security protocol and vulnerability mining technology, applied in electrical components, transmission systems, etc., can solve the problems of state space explosion, proof, no unified and accurate method, etc., to reduce workload, improve accuracy and efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
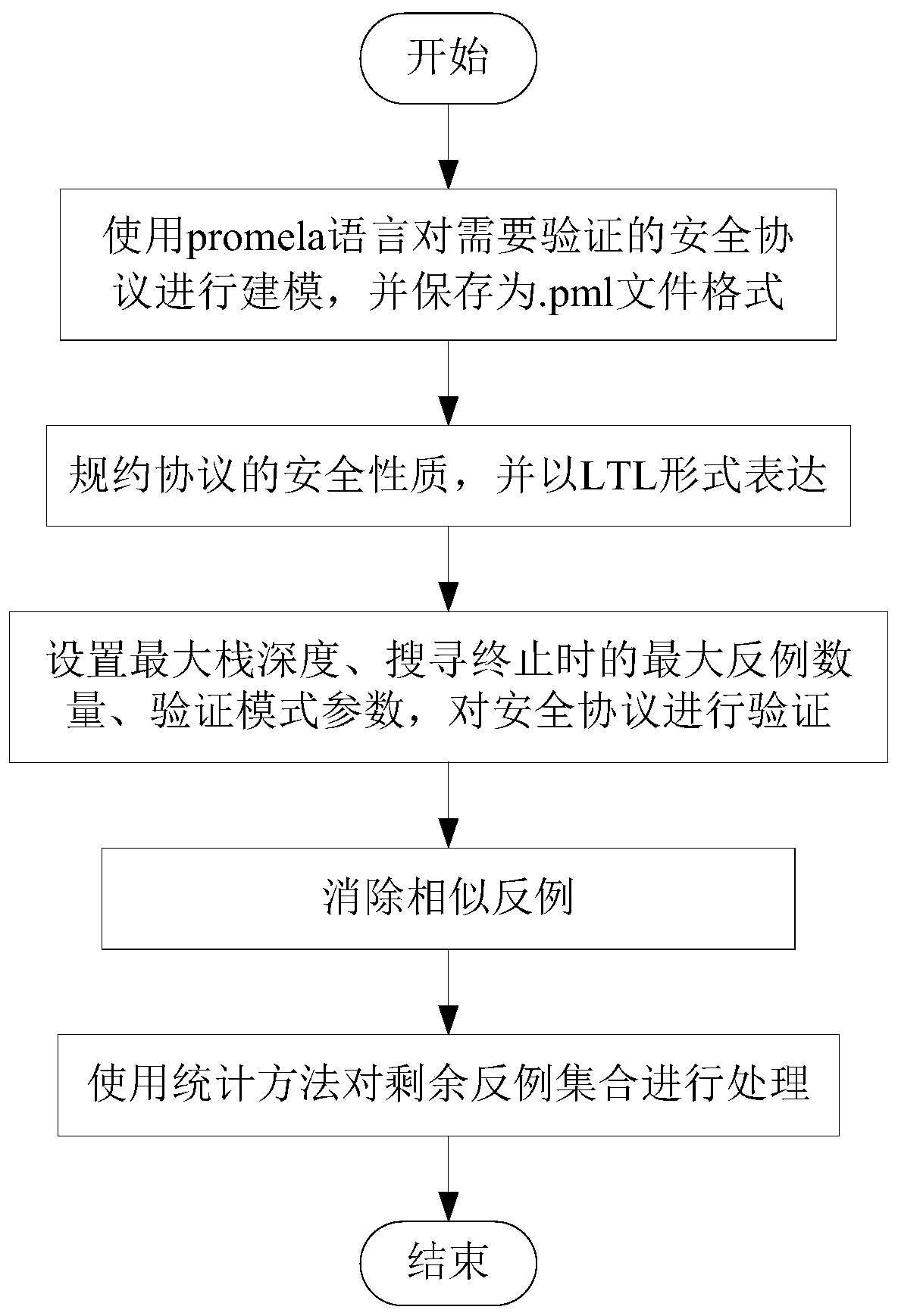
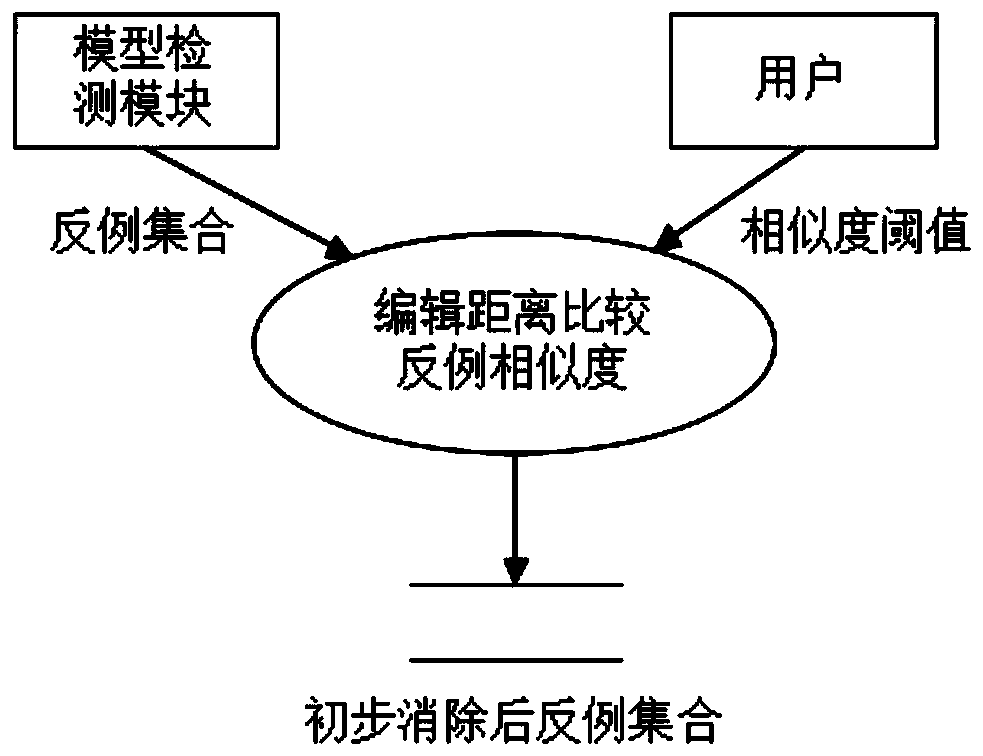
[0040] This method is extended on the basis of model detection. In the process of model detection, the concept of node weight is introduced, and the negative examples are analyzed, and the loopholes in the security protocol are discovered by synthesizing the information in multiple negative examples. The general idea is as follows: protocol modeling - model testing - eliminating similar counterexamples - analyzing numerous counterexamples and mining protocol loopholes. The specific process diagram is as follows figure 1 As shown, a detailed description is given below.
[0041] A security protocol loophole mining method based on multiple negative examples of the present invention comprises the following steps:
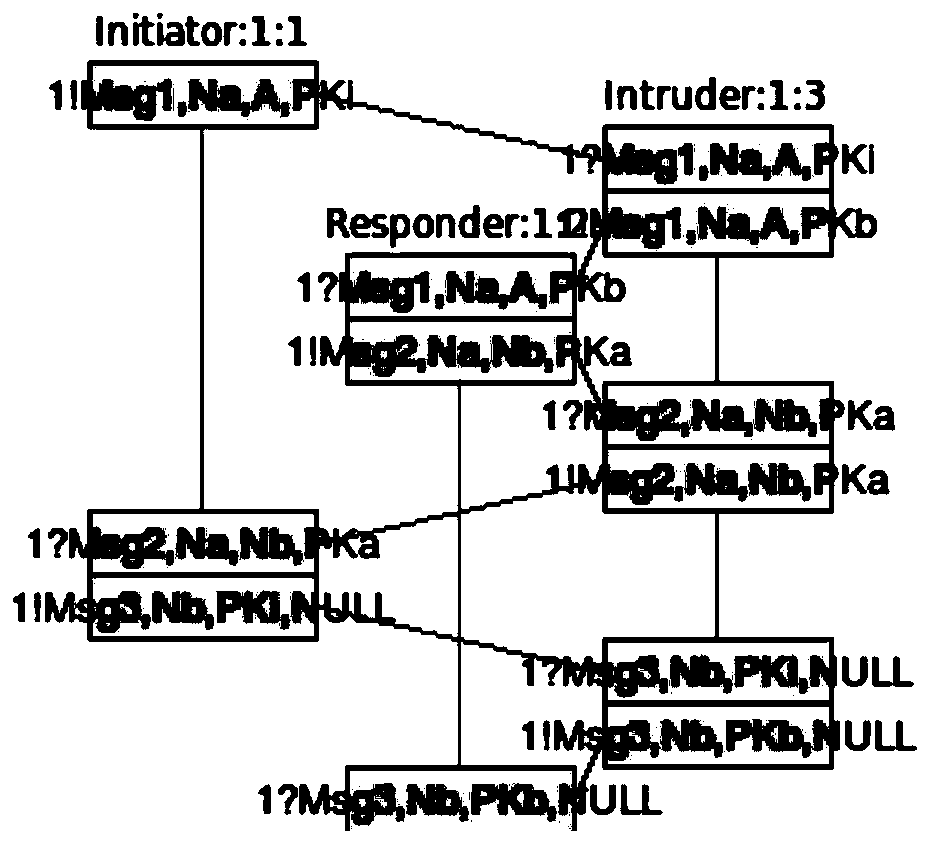
[0042] S1. Use the promela language to model the security protocol that needs to be verified, and save it as a .pml file format; in step S1, first use the promela language to model the security protocol. Here, the nspk protocol is taken as an example for illustration. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com