SDN network state consistency verification method in cloud environment
A technology of network status and verification method, applied in the field of virtual network security in cloud environment, can solve the problems of complex forwarding layer attack defense, large computing and communication overhead, inconsistent single-layer network status, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
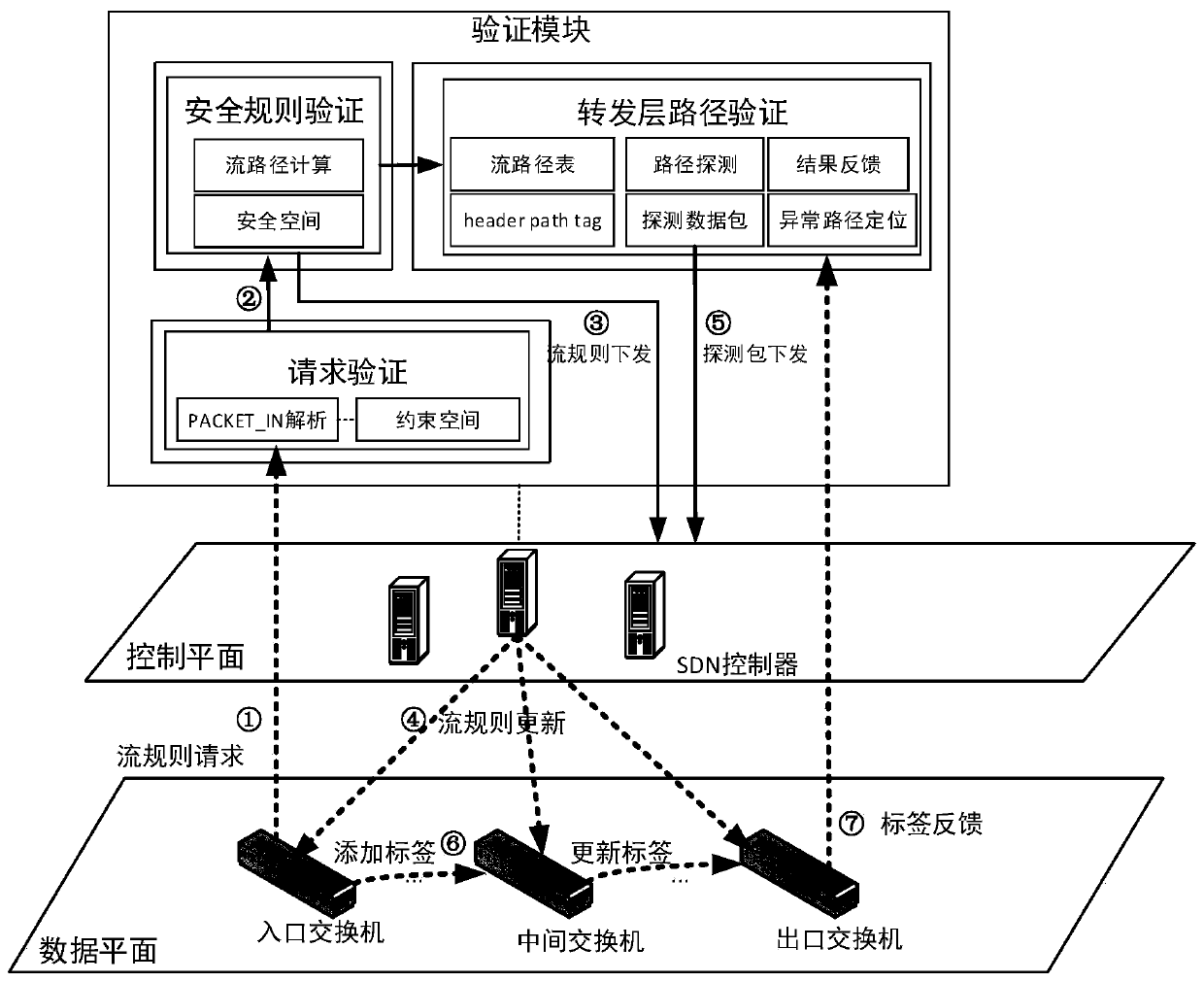
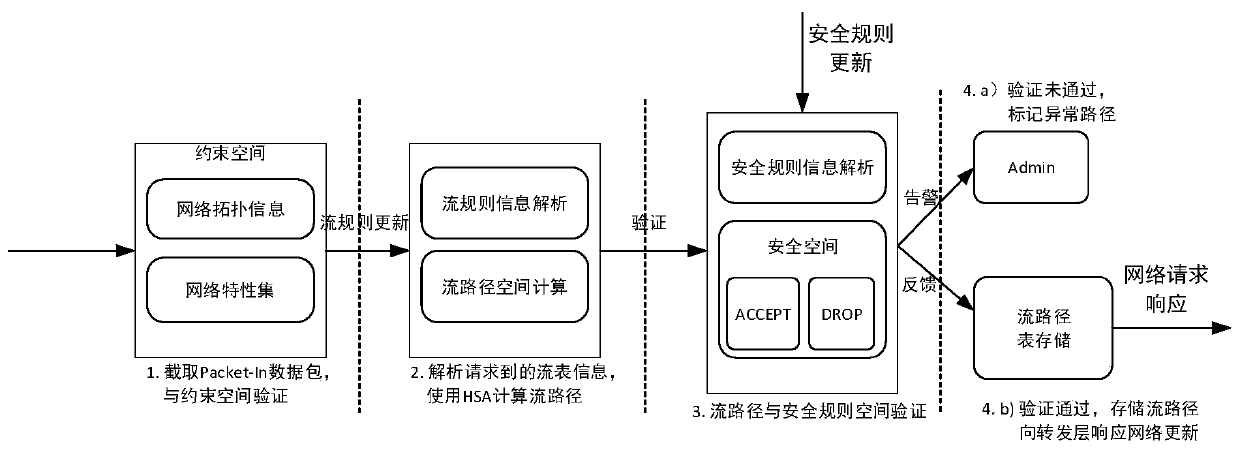
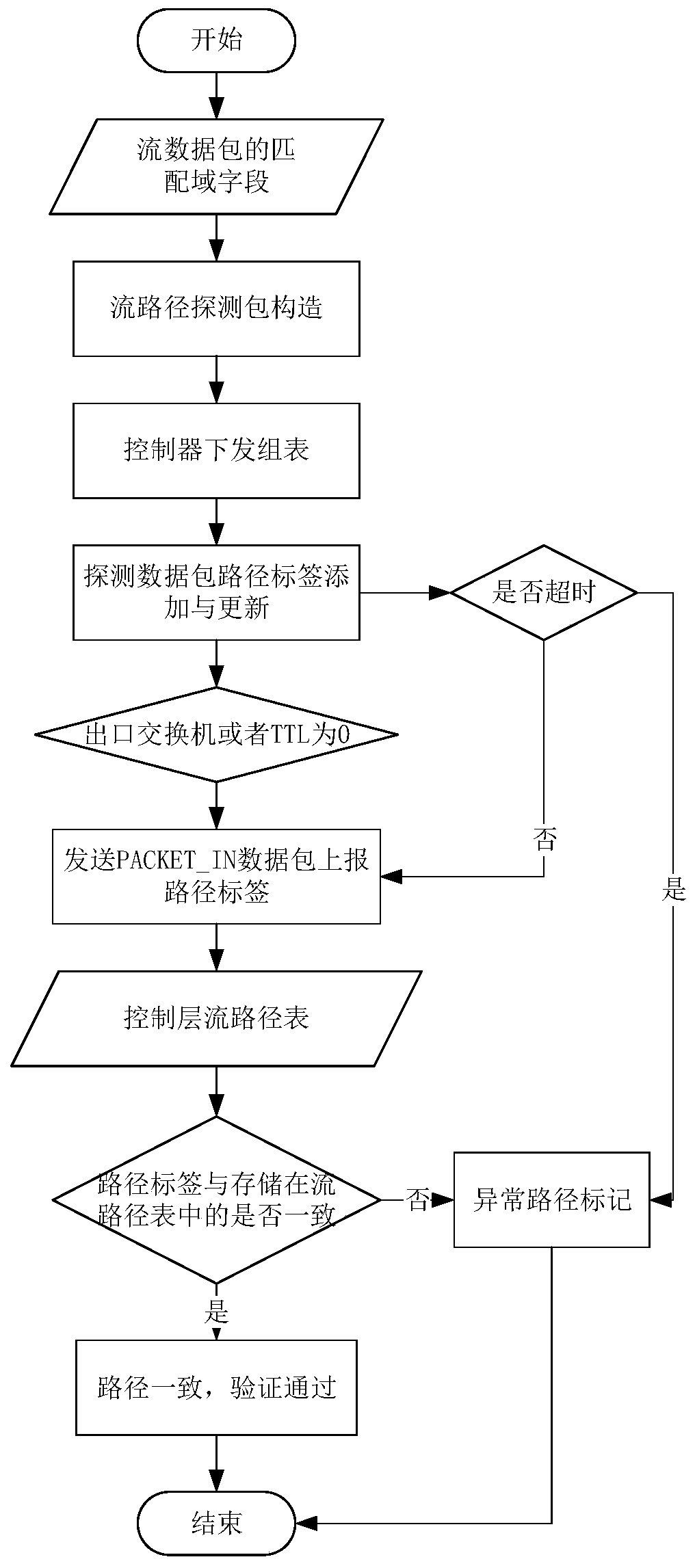
[0021] The realization principle of the present invention is: in the network update request stage, obtain the IP-MAC binding information, network topology status, switch link connection and port information, etc. of the virtual machine in the current network through the global network view of the controller, and analyze these information form a restricted space.
[0022] Call the API interface to obtain the security policy in the network, analyze and form a security space. In the cloud platform, security policies are organized in the form of chains, each chain defines a series of rules, and each rule defines a set of matching data packets and related actions of ACCEPT, DROP and calling other chains. The security chain analysis algorithm proposed by the present invention is as follows. The security chain analysis algorithm sequentially analyzes all the rules contained in a chain, and obtains the ACCEPT / DROP(S A / S D )space. Packet source information P that is matched by rul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com