A player configuration method under privacy protection
A privacy protection and configuration method technology, applied in digital data protection, computer security devices, data processing applications, etc., can solve problems such as technology or confidential information leakage partners, and achieve reduced time overhead, high privacy protection security, and response fast effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to facilitate those skilled in the art to understand and implement the present invention, the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the implementation examples described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention. invention.
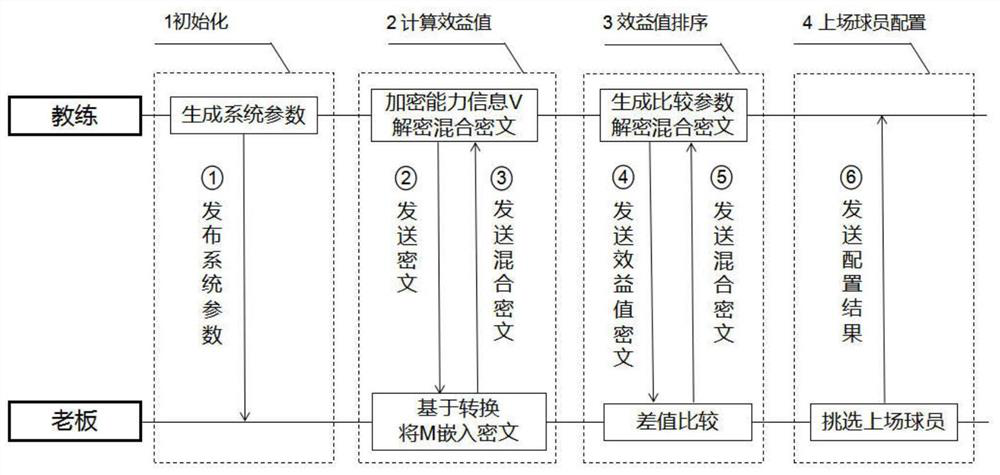
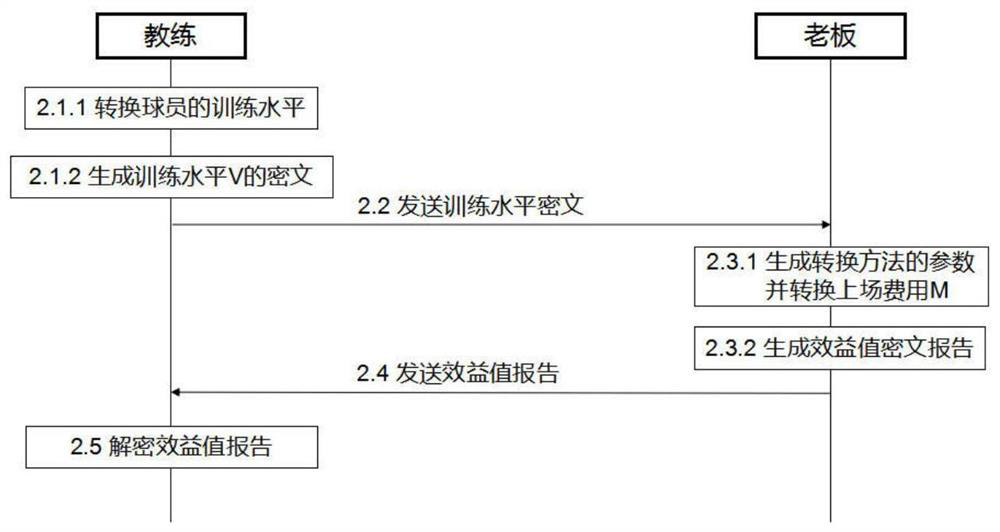
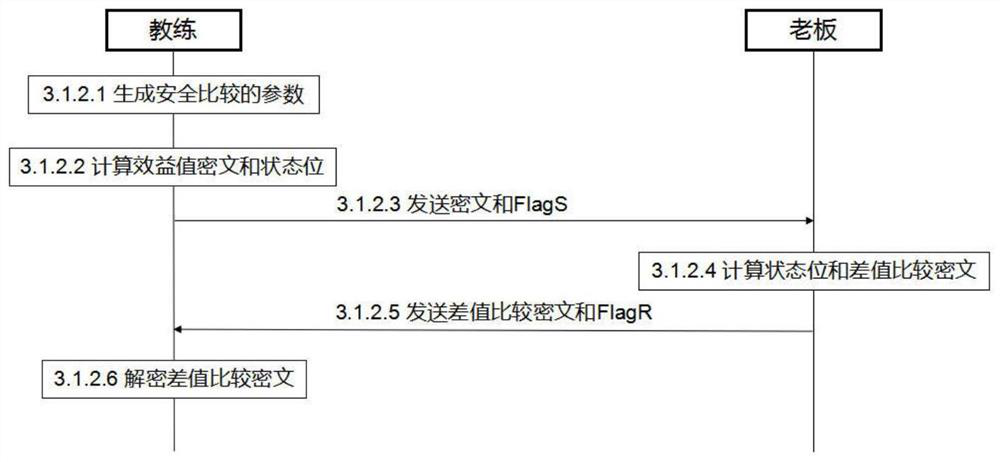
[0029] Suppose there are n players in a certain team (User 1 , User 2 ,...,User n ), the owner knows the playing costs of all players (M 1 , M 2 ,...,M n ), and has a fixed budget cost B; the coach masters the physical fitness and training data of all players, including shooting percentage, free throw percentage, physical strength, etc., and separately uses these private data of each player according to the same established rules converted to an integer (V 1 ,V 2 ,...,V n ); There is obviously a certain correlation between each player's playin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com