IOT device and user binding authentication method, device and medium
A technology of user binding and authentication method, applied in the field of IOT device binding, it can solve the problem that security cannot be guaranteed, and achieve the effect of abandoning illegal control and ensuring legality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
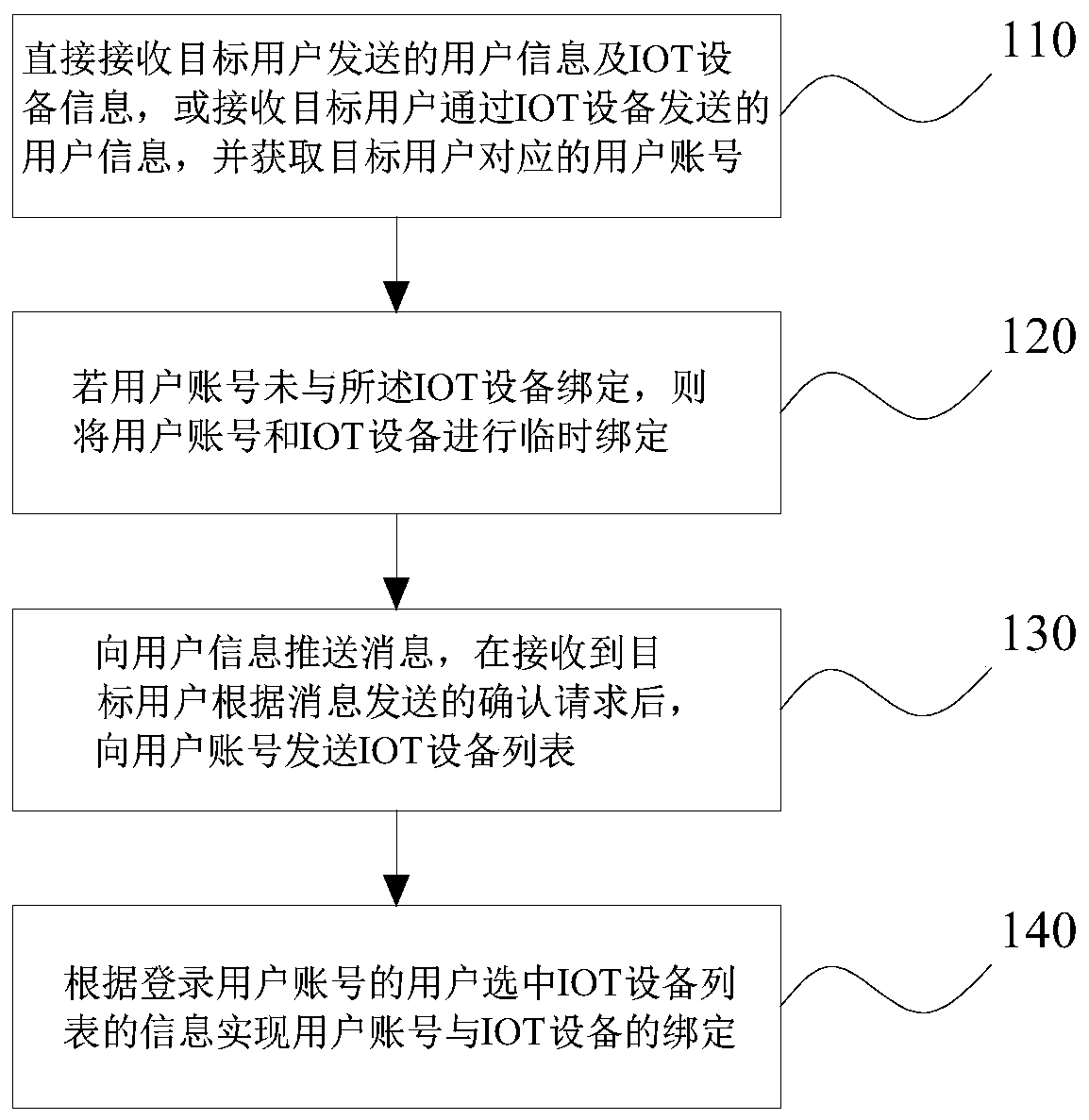
[0037] This embodiment provides an authentication method for binding an IOT device to a user, aiming at ensuring the security and legitimacy of the binding, please refer to figure 1 As shown, it includes the following steps:
[0038] 110. Directly receive user information and IOT device information sent by the target user, or receive user information sent by the target user through the IOT device, and obtain a user account corresponding to the target user.
[0039] The authentication device bound to the IOT device and the user (that is, the electronic device in Embodiment 5) may be a cloud or an entity server existing in other forms. Here, the cloud is taken as an example. The target user is the user who initiates the authentication request for the binding of the IOT device and the user, which is not necessarily the same user as the user who subsequently performs the binding operation between the IOT device and the user and the user who controls the IOT device after binding. ...
Embodiment 2
[0063] The second embodiment is the operation of configuring the IOT device network before the first embodiment. In the second embodiment, IOT device network configuration is implemented through the configuration interface of the app installed on the terminal device. The process is: the terminal device obtains the WLAN hotspot of the IOT device to connect to the wireless LAN, and then enters the ssid and password of the WAN WiFi in the configuration interface, and the IOT device receives it and completes the network configuration according to the ssid and password of the WAN WiFi.
Embodiment 3
[0065] The third embodiment is the operation of configuring the IOT device network before the first embodiment. In the third embodiment, the terminal device is connected to the AP node to obtain the configuration interface to realize the network configuration of the IOT device. Communication, user-friendly.
[0066] The process is:
[0067] The terminal device obtains the WLAN hotspot of the IOT device to connect to the wireless local area network, and obtains the IP address, Gateway address and DNS server address returned by the IOT device according to the wireless local area network connection;
[0068] The terminal device obtains and resolves IP through the Gateway address;
[0069] The terminal device sends an http request to the resolved IP to obtain the configuration interface of the IOT device;
[0070] The terminal device transmits the ssid and password for connecting to the WAN WiFi to the IOT device through the configuration interface.
[0071] The above configur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com