Cognitive security transmission method based on wireless information and power joint transmission
A technology of secure transmission and joint transmission, which is applied in the field of cognitive security transmission based on the joint transmission of wireless information and power, and can solve the problems of lack of spectrum resources for cognitive users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
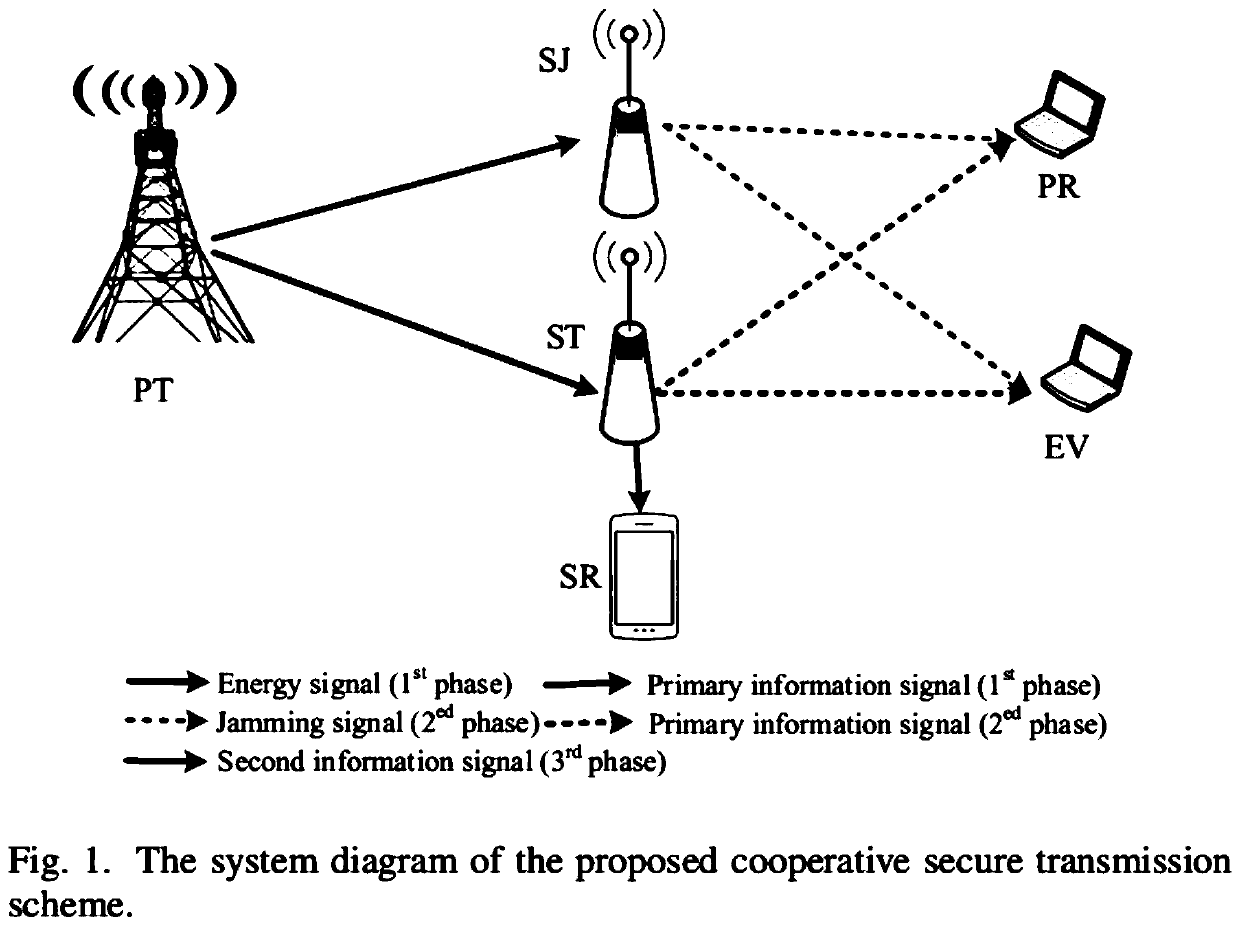
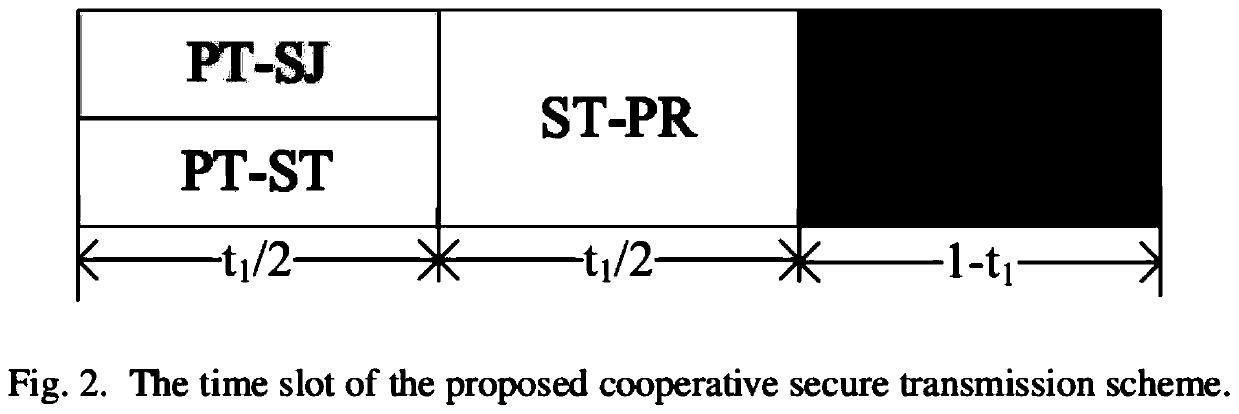
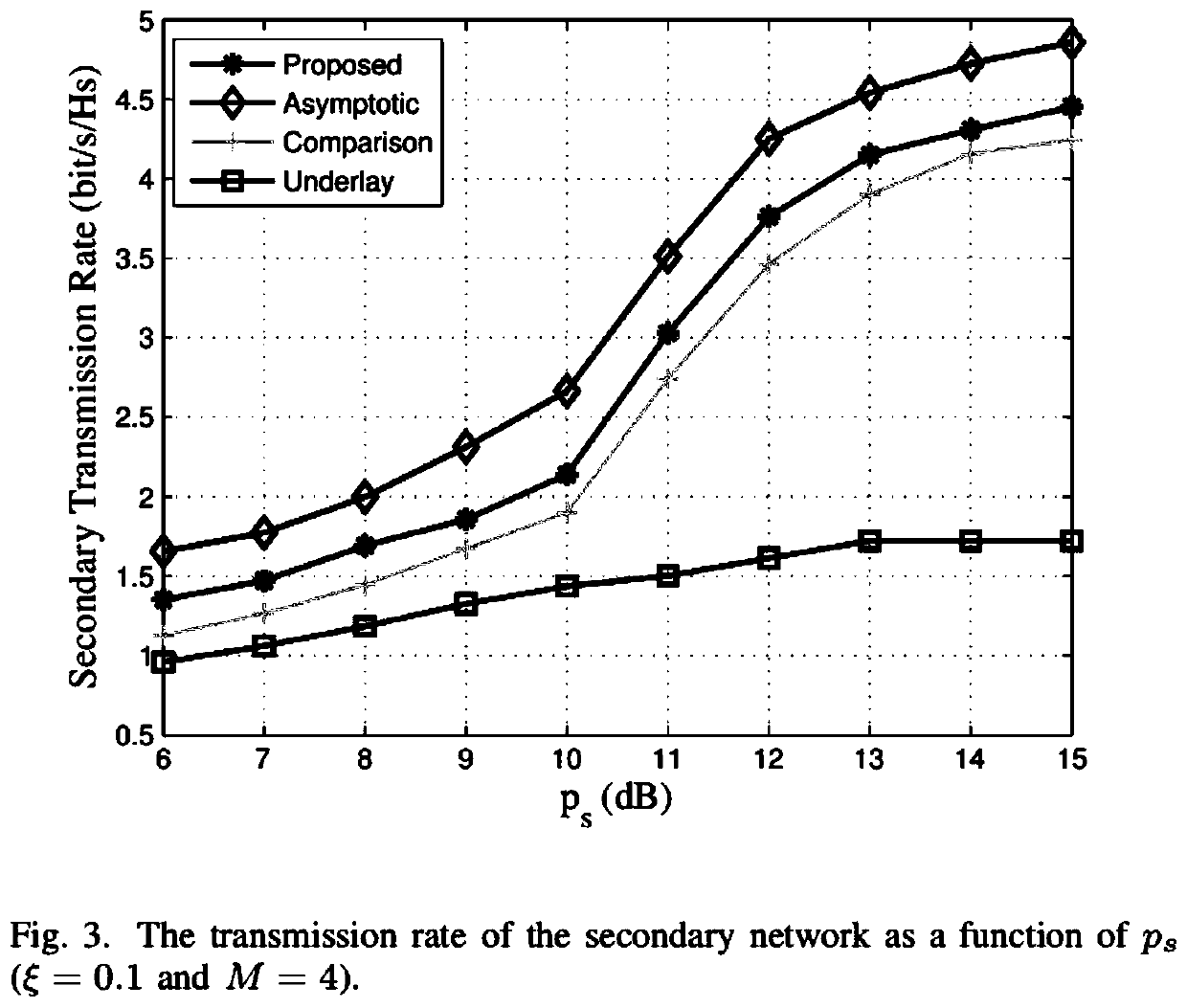
[0077] The present invention provides a cognitive security transmission method based on joint transmission of wireless information and power. Considering a five-node transmission network, the authorized user transmitting terminal PT wants to transmit information safely and reliably to the authorized user receiving terminal PT. Eve will Eavesdropping on PT's transmission data. A PT has M antennas. Cognitive user ST uses the decoding and forwarding mechanism to send authorized user private information, and cognitive user SJ uses energy harvesting mechanism to receive energy information, and then transmits cooperative interference information to protect the safe transmission of authorized user information. After the authorized user completes the transmission, the cognitive user ST uses the frequency spectrum to send cognitive user information. For this scheme, we analyze the transmission outage probability and security outage probability of the network, and optimally allocate ti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com