Opportunity spectrum access method based on sideband observation information multi-arm tiger machine model
A spectrum access technology, applied in wireless communication, transmission monitoring, electrical components, etc., can solve the problems of low channel sensing and access process balance efficiency, poor adaptability to the actual environment, poor statistical characteristics, etc., to achieve efficient dynamic Effects of Channel Awareness and Opportunistic Access Methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
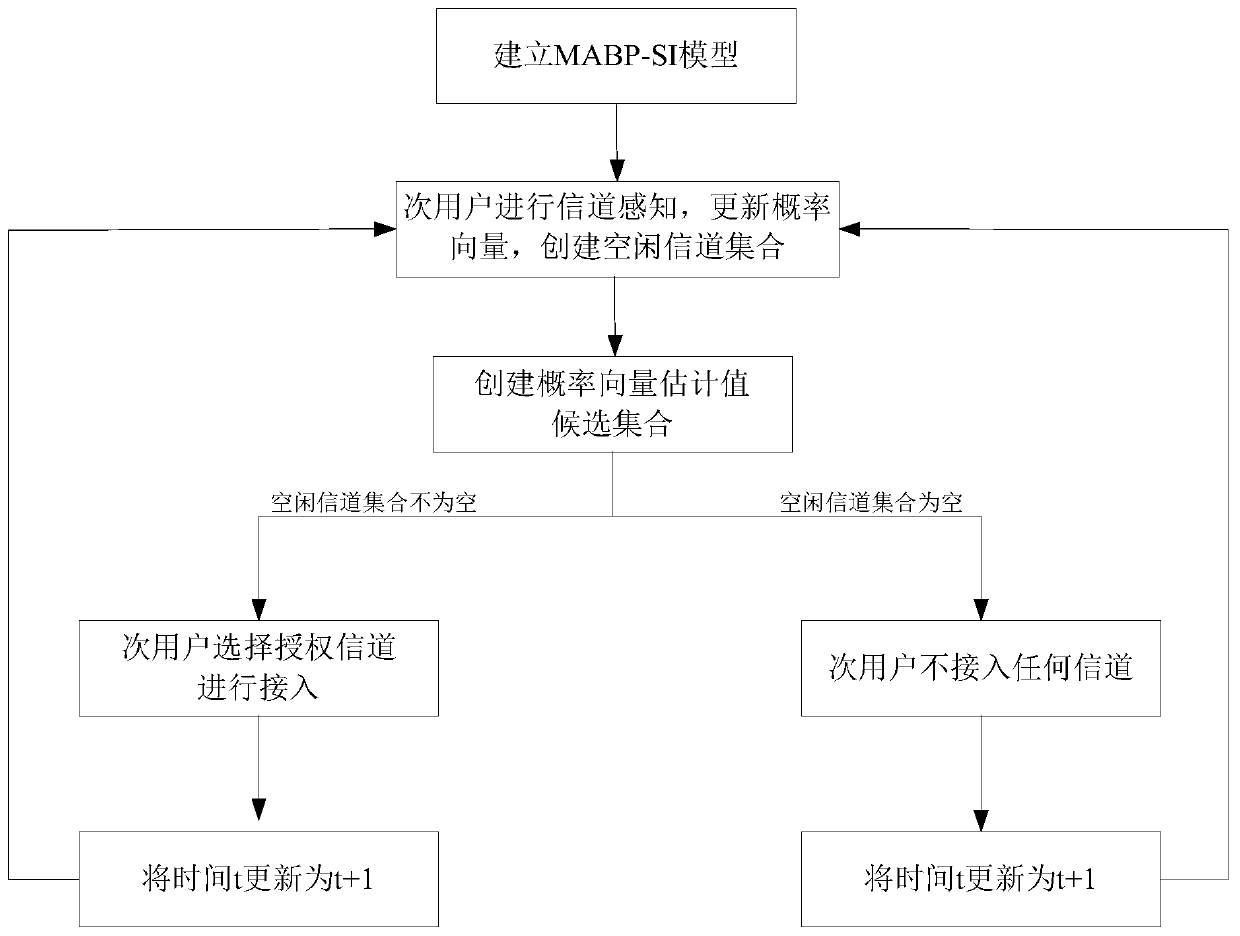
[0056] combine figure 1 , a method of opportunistic spectrum access based on a sideband observation information multi-armed bandit model in the present invention, characterized in that it comprises the following steps:
[0057] Step 1. For the secondary user access problem when the channel information of the cognitive network is unknown and the channel perception is not perfect, the detection and perception of N channels will be carried out, and the problem of selecting a channel suitable for access is modeled as the MABP-SI model. for:
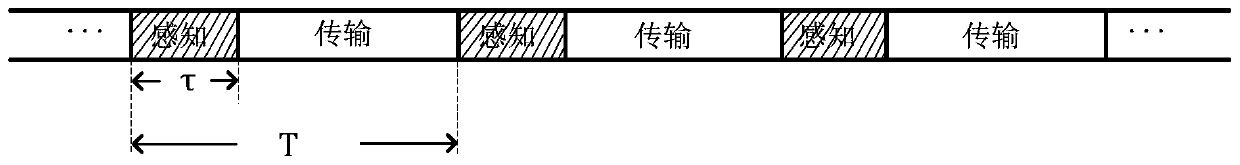
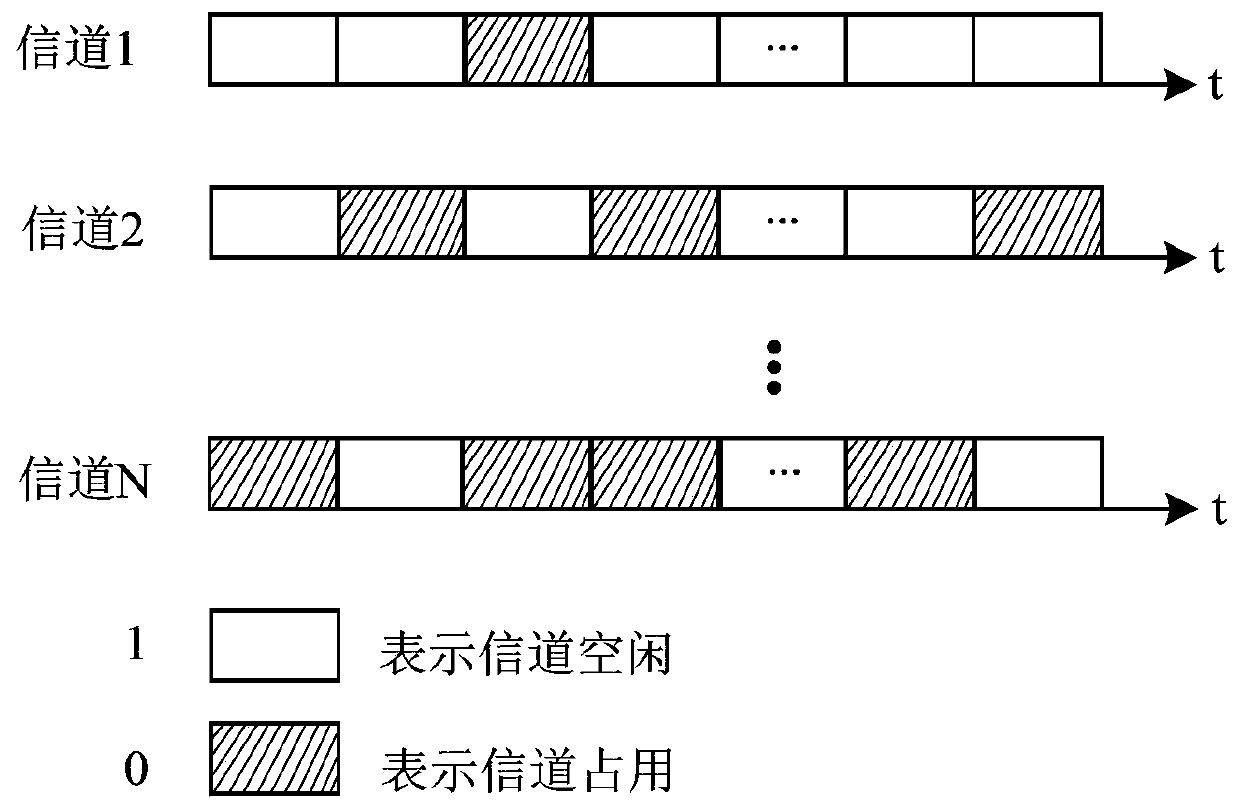
[0058] combine figure 2 , secondary users in the cognitive network perform dynamic channel access according to authorized user time slots. Within a time slot, secondary users can perceive all authorized channels in the network; the time for channel sensing access is divided into time slots, and the duration is T; the network has N authorized users, which are respectively recorded as channels 1, 2, ..., N, such as image 3 As shown, for e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com