Electronic official document exchange encryption method based on BlockChain
An encryption method and electronic document technology, applied in the field of data security, can solve problems such as unfairness of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
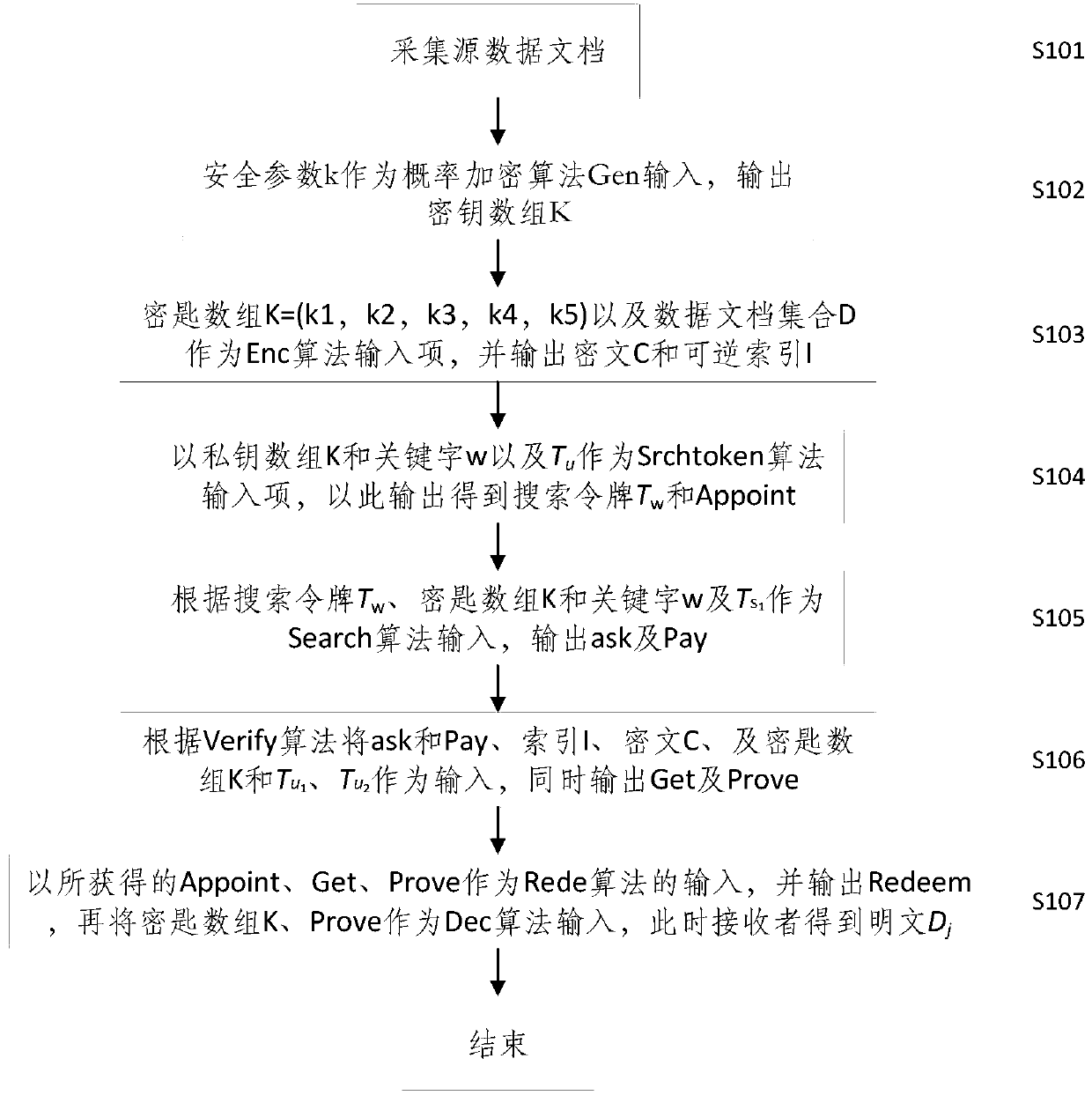
[0025] Such as figure 1 As shown, the embodiment of the present invention provides an electronic document exchange encryption method.
[0026] First, source data documents are collected in step S101, and user data comes from data warehouses and data in servers.
[0027] Secondly, in step S102, after the data owner takes the parameter k as input, the key array K=( k 1 , k 2 , k 3 , k 4 , k 5 ).
[0028] In the process of generating the ciphertext C in step S103, the ciphertext C should be calculated in the following manner using the private key and the source document.
[0029] C i =ε.Enc k1 (D i )(1 ≤ i ≤ n )
[0030] MAC ( C i )=( K 5 , C i )
[0031] C ← (( C 1 , MAC ( C 1 )), ..., ( C n , MAC ( C n )))
[0032] Generating an index first extracts keywords from the document, for each keyword w i ∈ W empty array should be set DB ( w i ), if the jth document contains keywords w i ,butDB ( w i )[ j ] to 1, otherwise, set DB ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com