Threshold group signature method based on public verification of block chain
A blockchain and group signature technology, applied in the field of information security, can solve the problems that the signature scheme cannot trace the user's identity and guarantee the user's privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
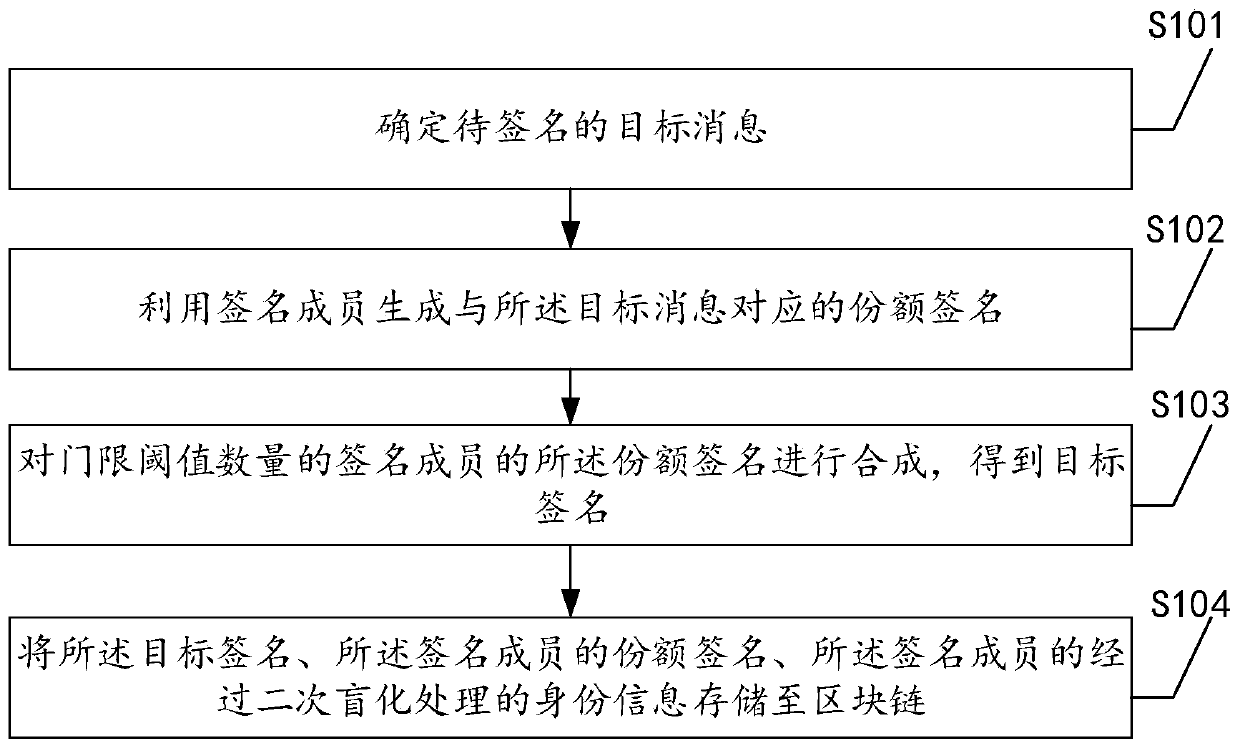
[0059] The following is an introduction to Embodiment 1 of a threshold group signature method based on blockchain public verification provided by this application, see figure 1 , embodiment one includes:
[0060] S101. Determine the target message to be signed;
[0061] When users encounter electronic transactions or set private information during business processing, they often need to perform signature authentication on the business data of electronic transactions or private information. In this embodiment, the target message mainly refers to the business data to be signed and authenticated. in the field of e-commerce.
[0062] S102. Using the signature member to generate a share signature corresponding to the target message;
[0063] For signing members, when generating a share signature, first generate a random number, solve the corresponding hash value for the target message, and then use the random number, the hash value of the target message, the private key of the si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com