Secure interaction method and device based on information transmission
An information transmission and interaction method technology, applied in the field of information transmission-based security interaction methods and devices, can solve problems such as illegal attack security risks, and achieve the goal of ensuring security protection capabilities, improving work efficiency, and ensuring data confidentiality and integrity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
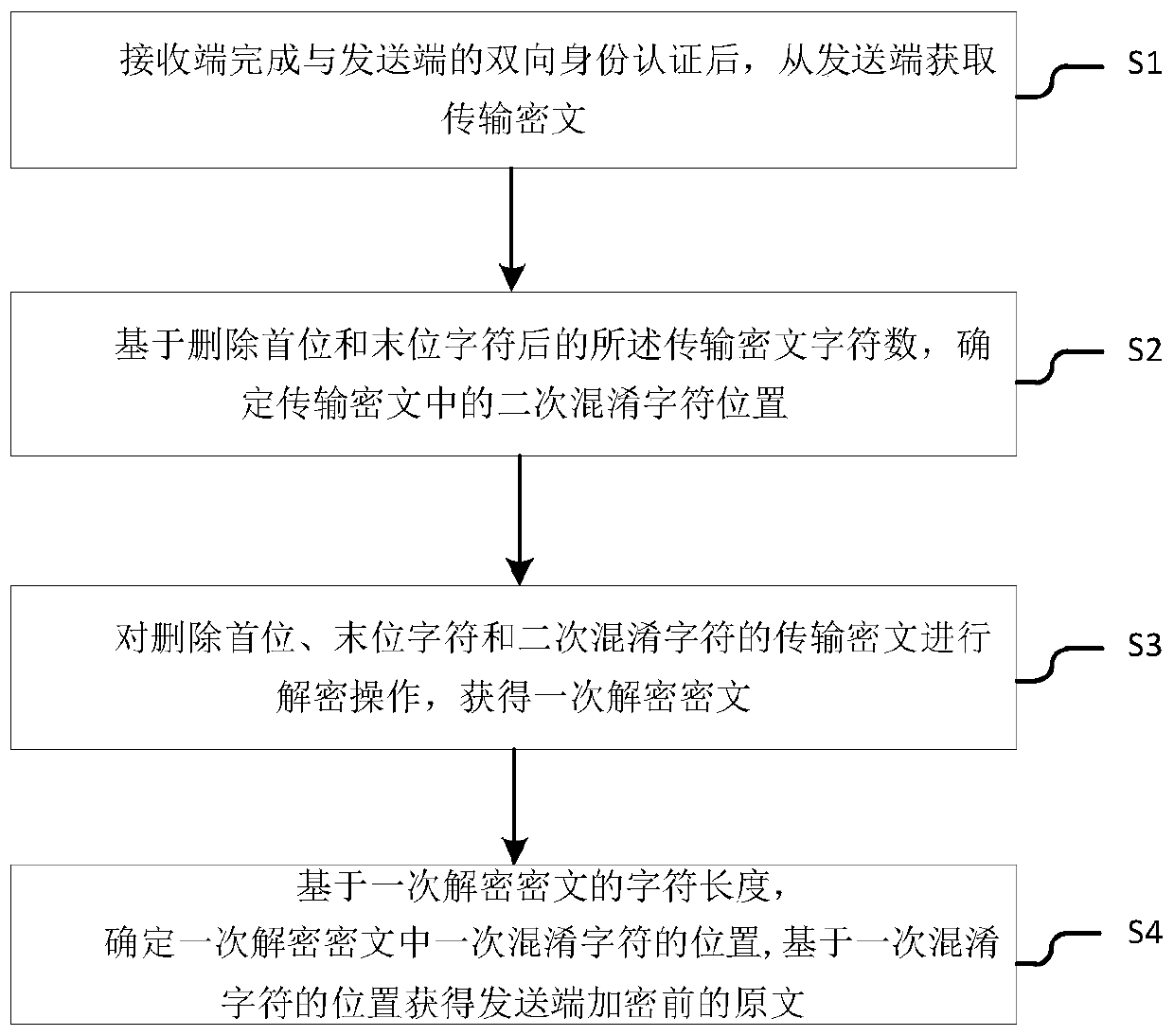
[0048] The present invention provides a safe interaction method based on information transmission, such as figure 1 shown, including:
[0049] S1 After the receiving end completes the two-way identity authentication with the sending end, it obtains the transmission ciphertext from the sending end;
[0050] S2 determines the secondary obfuscation character position in the transmission ciphertext based on the number of characters in the transmission ciphertext after deleting the first and last characters;
[0051] S3 decrypts the transmission ciphertext with the first character, the last character and the secondary obfuscated character deleted, and obtains the primary decrypted ciphertext;
[0052] S4 Determine the position of the primary obfuscation character in the primary decryption ciphertext based on the character length of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com