Android malicious software detection method and system based on RNN and CNN
A technology for malware and detection methods, applied in neural learning methods, decompilation/disassembly, program code conversion, etc., which can solve problems such as a large number of model parameters, ignoring the contextual relationship between opcode sequences, detection accuracy and training efficiency. , to achieve the effect of high recognition accuracy and easy operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0050] The invention provides a method and system for detecting Android malicious software based on RNN and CNN, which are used to identify and distinguish benign software and malicious software under the Android platform, so as to improve the security of the Android software platform.
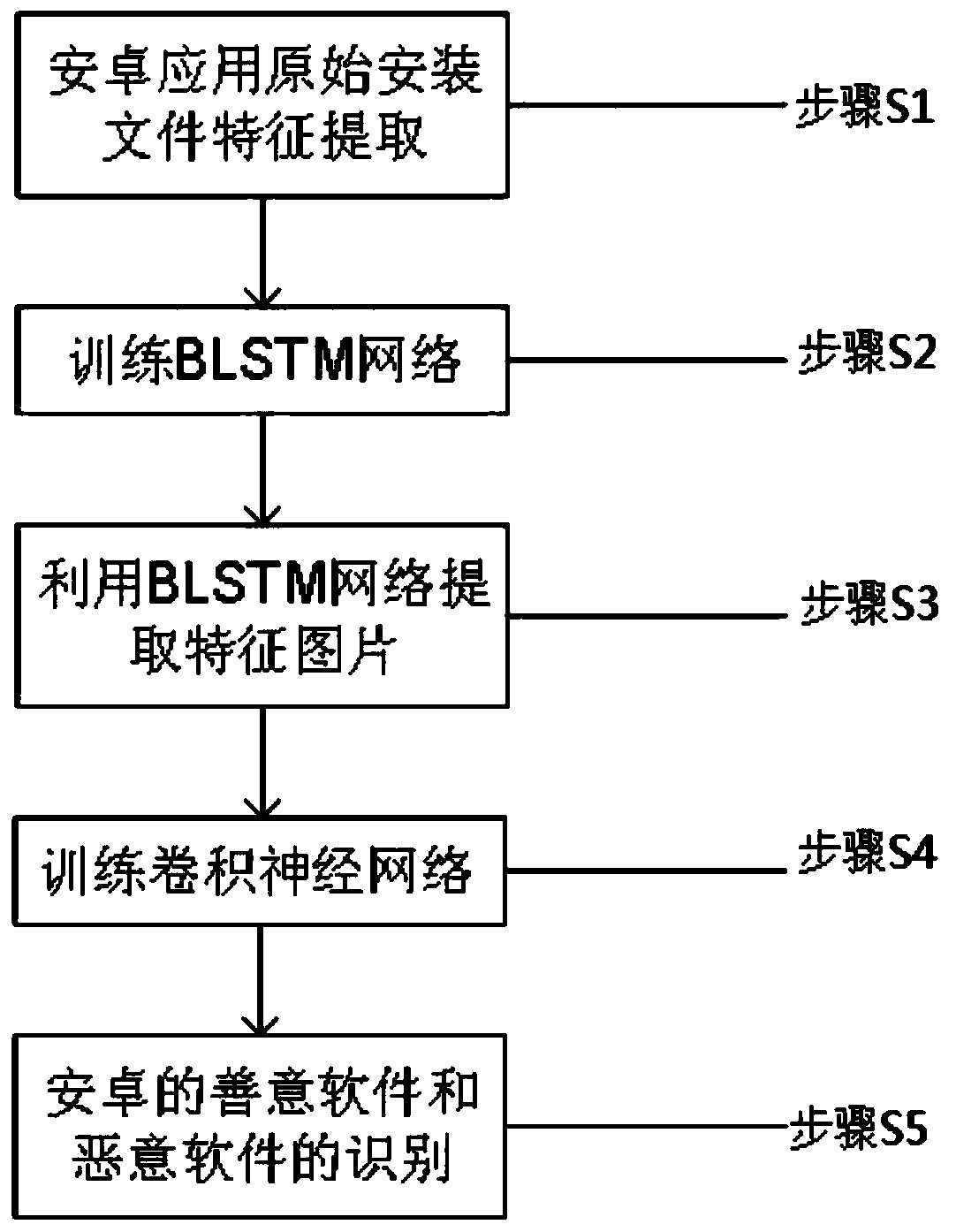
[0051] Such as figure 1 Shown, the Android malware detection method based on RNN and CNN of the present invention, comprises the following steps:
[0052] S1, performing feature extraction on the original installation file of the training sample to obtain an operation code sequence;
[0053] Step S1 specifically includes the following processing:
[0054] S1-1, use the 7-zip tool to decompress the .apk installation file of the training sample, and obtain the class.dex file contained in the .apk installation file;
[0055] S1-2, using the .apktool d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com