Generation and verification method, device, device and storage medium of device password
A device password and password technology, applied in the computer field, can solve the problem of less application scenarios, and achieve the effect of enriching types and improving applicable application scenarios.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
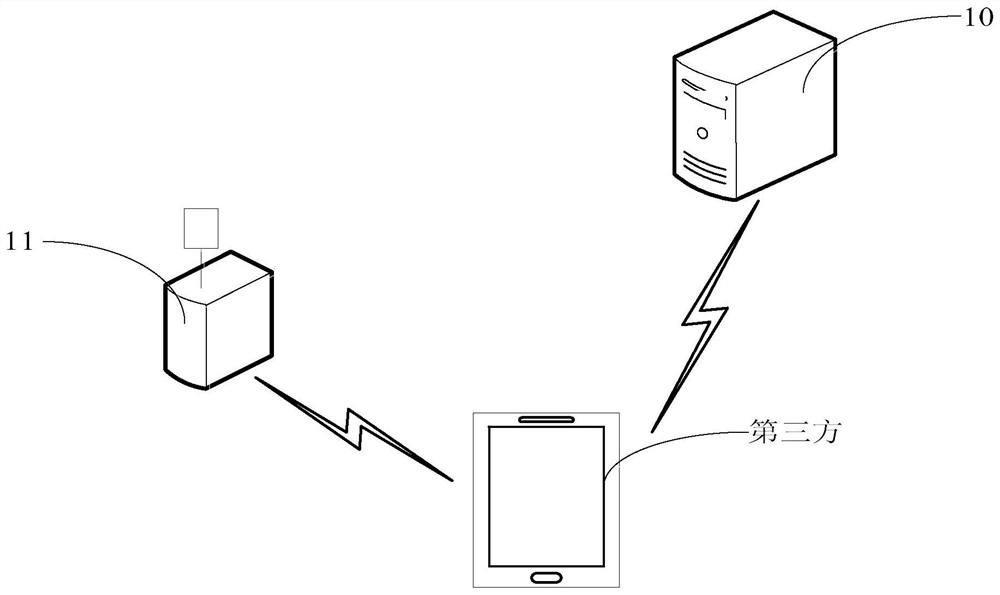
[0053] The device password generation method provided by the embodiment of this application is applied to such as figure 1 system shown. The system includes: a device password generation terminal 10 and a device password verification terminal 11 . There is no direct communication between the device password generator 10 and the device password verifier 11, and the generated device password needs to be input to the device password verifier 11 through a third party, so that the device password verifier 11 can verify the validity of the input device password. verify. Optionally, the device password generating terminal 10 may be an electronic device such as a server, a personal computer, or a wearable device, and the device password verification terminal 11 may be an electronic device requiring password verification such as a smart door lock or a smart safe. Taking the device password verification terminal 11 as an example of a smart door lock, the device password generator 10 g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com