A kind of intelligent unlocking method and corresponding device
An unlocking and intelligent technology, applied in the field of security identification, can solve problems such as being easily stolen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
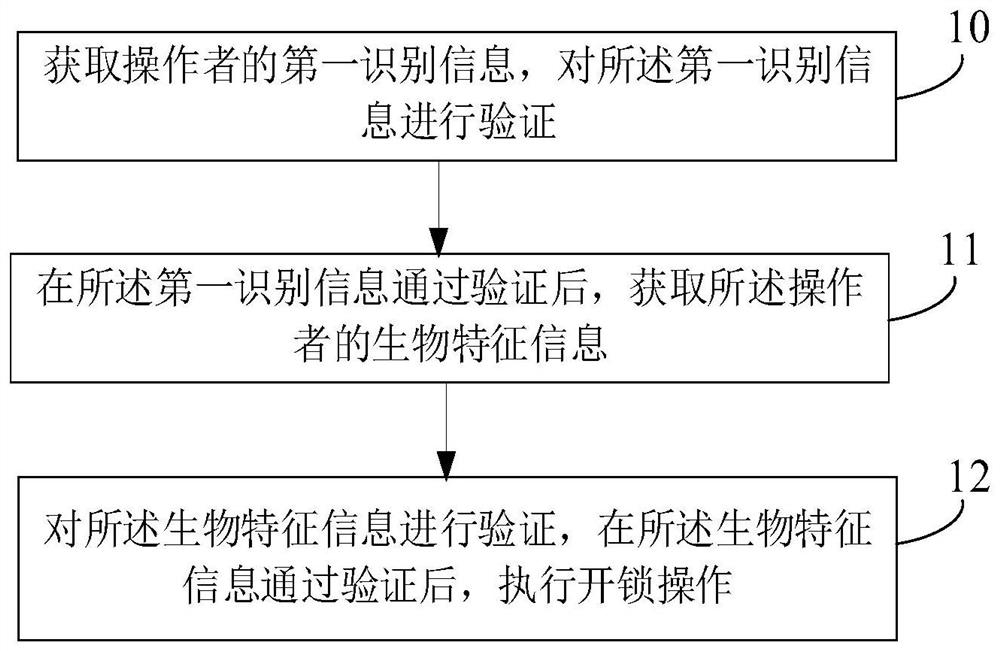
[0062] See figure 1 This embodiment provides a smart unlocking method, the intelligent unlocking method comprising the steps of:
[0063] Step 10: Get the first identification information of the operator, verify the first identification information.
[0064] In an alternative embodiment, the first identification information can be the operator's document, wherein the documents applicable to the present embodiment include, but are not limited to, ID cards, passports, Hong Kong and Macao pass, Taiwanese cards, Hong Kong and Macao to Township, Hong Kong and Macao Table resident residence permit and driver's license.
[0065] When the first identification information is a document, the verification process of the first identification information is the fault process of the certificate, and the first identification information is verified when the document is verified by the authentication.
[0066] In the actual application scenario, the operator has often occurred in the case where t...
Embodiment 2
[0127] Bonded below Figure 5 ~ 7 , Specifically, the first identification information is implemented in the implementation of the verification code.
[0128] In one embodiment, see Figure 5 with Figure 7 Step 10 includes the steps of:
[0129] Step 1021: Receive the trigger request of the operator, obtain the contact information of the user corresponding to the electronic lock, based on the trigger request.
[0130] The trigger request can be unique identification information of the electronic lock input by the operator, or a face image corresponding to the electronic lock selected by the operator.
[0131] Among them, the contact information can be a telephone, WeChat, QQ or other type of social approach.
[0132] Step 1022: Verification code corresponding to the electronic lock by the contact manner.
[0133] Step 1023: Deconed whether the verification code entered in the preset time is correct, if it is correct, the first identification information is verified.
[0134] In the ...
Embodiment 3
[0148] The foregoing embodiment mainly illustrates the process of verifying unlocking, and below Figure 8 Briefly describe a process for a user to register using an electronic lock.
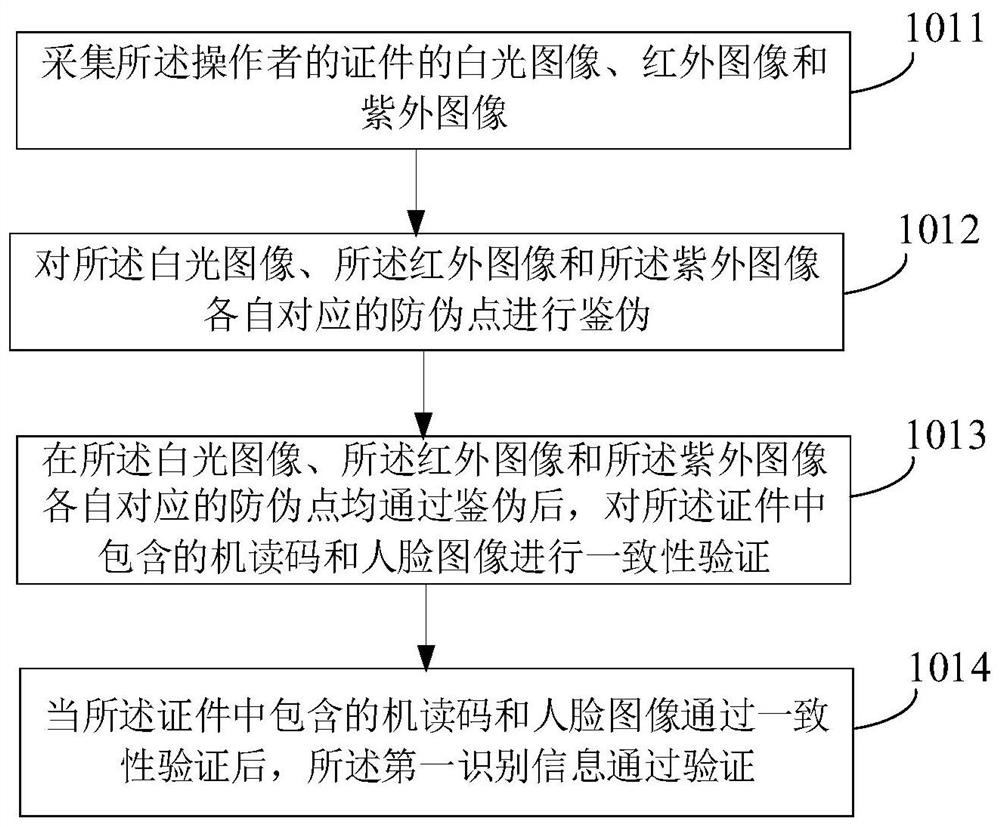
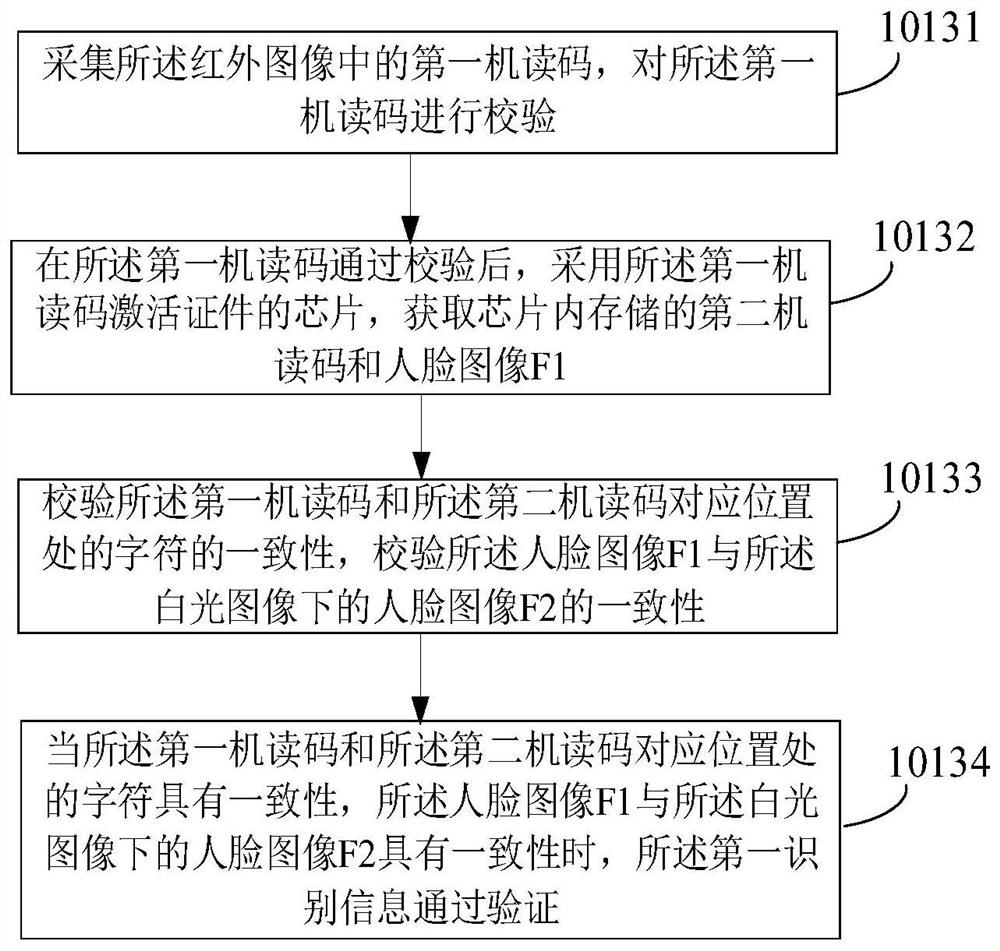
[0149] Such as Figure 8 As shown, first, according to the passage of the included in the first embodiment, the documents are authenticated and consistency, and after the operator's documents passed the fake and consistency, the operator's real-time face image is collected, and the real-time person The face image is processed to obtain a face image F3, wherein the face image F3 can be referred to in Example 1, and details are not described herein again.
[0150] The consistency between the face image F3 and the face image (F1 and F2) in the documents, when the face image F3 is consistent with the face images (F1 and F2) in the documents, receive the operator (user) The biometric information and contact information is entered, and the authorization period of the operator (user) is set. After the licens...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com