An Authenticated Communication Method in Smart Homes Based on HLC and Hash Collision Puzzles
A communication method and smart home technology, applied in the field of authentication communication, can solve problems such as insufficient computing power of home smart devices, and achieve the effect of satisfying high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
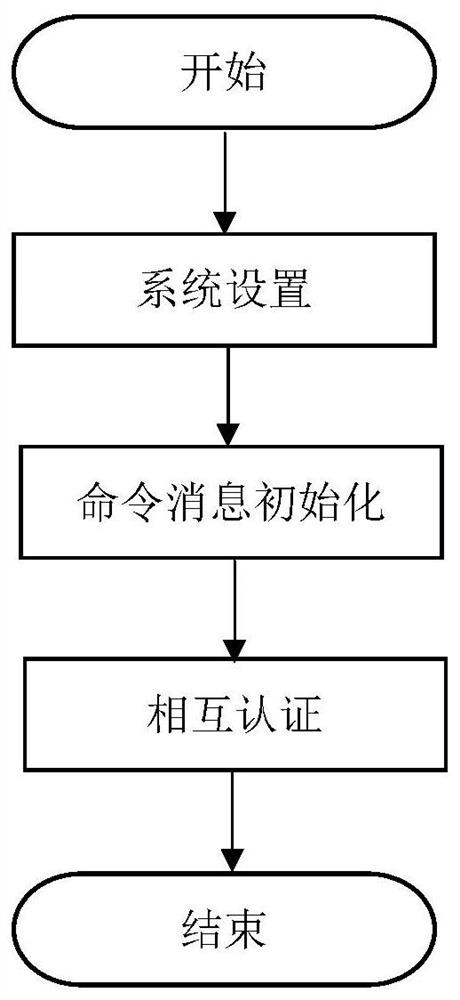
[0056] The authentication communication method in a smart home of the present invention includes the following entities: a user, a server, a home gateway, and a home smart device. Including the following steps:
[0057] (1) System settings
[0058] In the system setting stage, the trusted entity (TA) generates system parameters params, and sends them to the home gateway and home smart devices offline. The generated system parameters are used for subsequent mutual authentication between the home gateway and the home smart device. We assume that the home gateway is trusted, so we let the home gateway play the role of TA. The specific steps are as follows:
[0059] • Choose ε as the difficulty of the puzzle.
[0060] • Choose ΔT as an upper bound on the message round-trip time.
[0061] • Choose H(*) as the hash function, and the output of this function is k bits.
[0062] · Select m as the number of elements in the Nonce.
[0063] TA distributes params=(∈,ΔT,H(*),m) to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com