Message anomaly detection method based on deep learning
An anomaly detection and deep learning technology, which is applied in unstructured text data retrieval, text database clustering/classification, special data processing applications, etc., can solve problems such as low detection efficiency and poor model detection effect, and achieve accuracy Improvement, learning and detection speed, good convergence effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
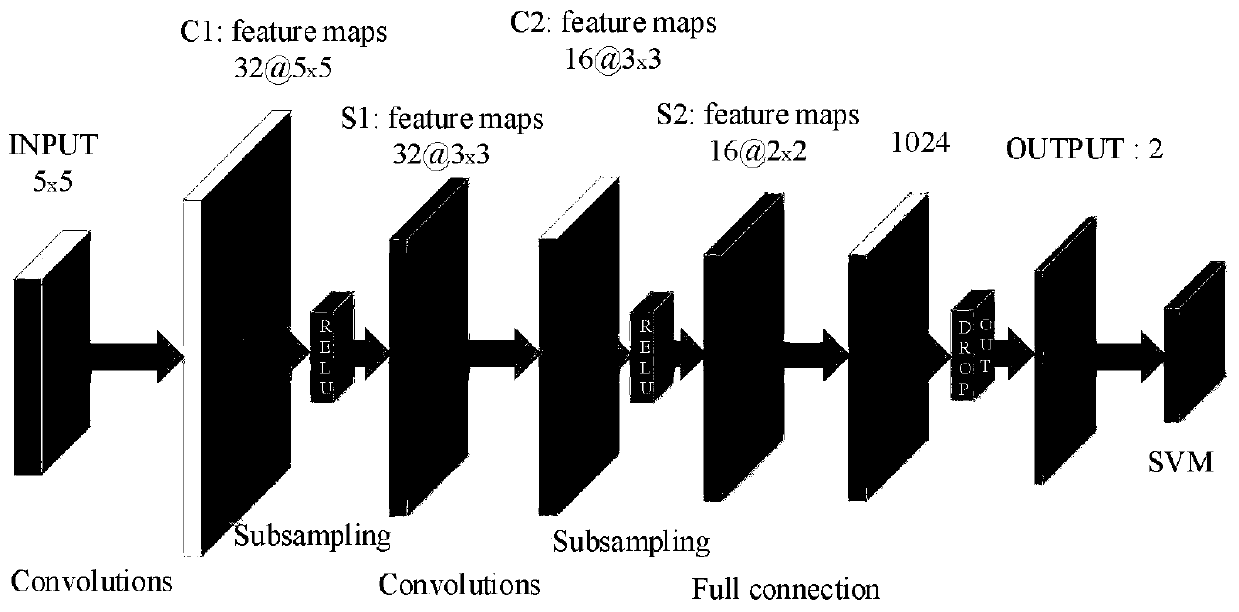
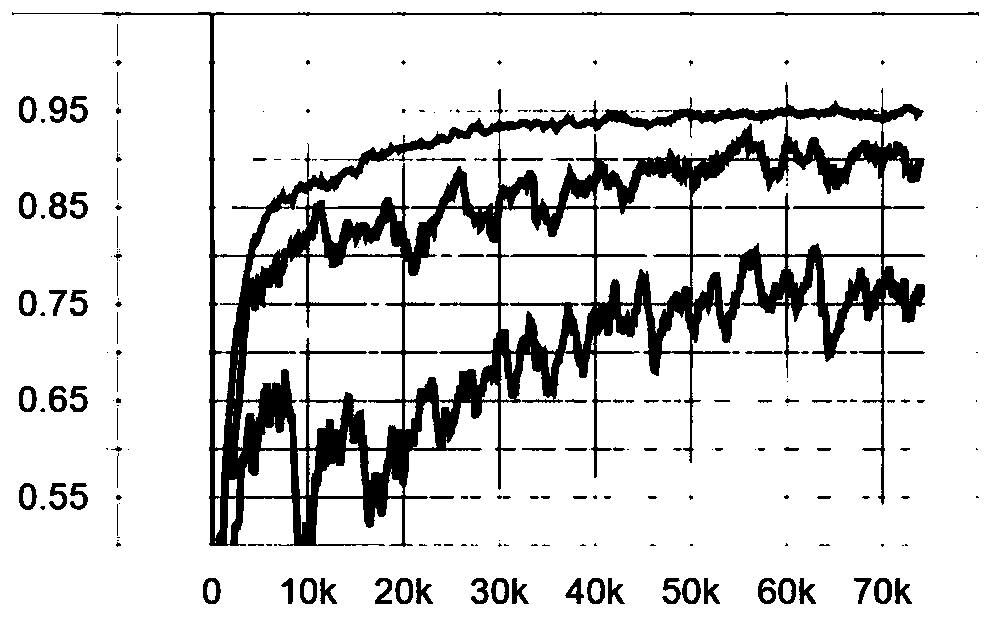
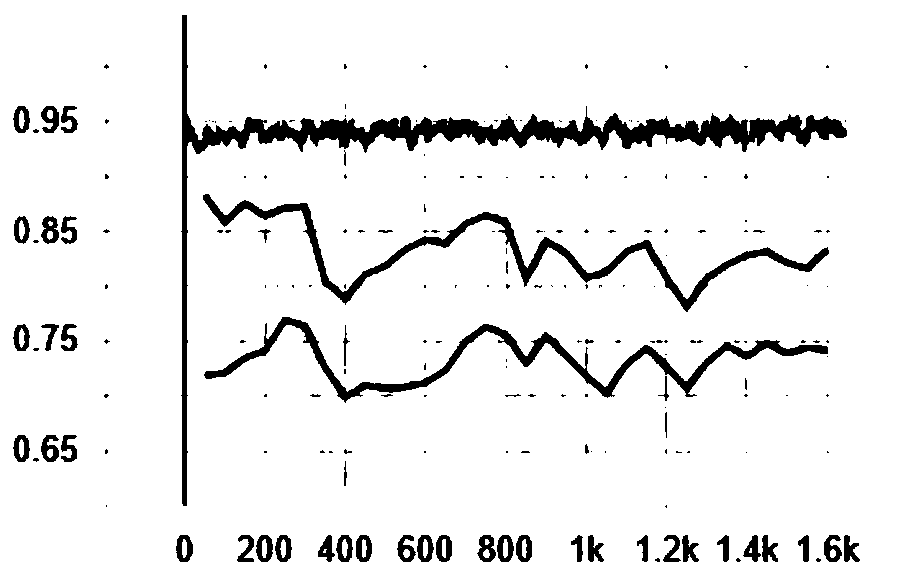
[0016] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings. figure 1 It is an overall architecture diagram of the method involved in the present invention.
[0017] Step 1, dataset preprocessing
[0018] The network traffic data of the well-known Kyoto University honeypot system is used in the implementation process of the present invention. It contains 24 statistical features, (1) 14 features from the KDD CUP data set in 1999; and (2) 10 additional features, on this basis in order to adapt to the algorithm model CNN-SVM of the present invention, the data set is processed as follows:
[0019] 1) Data processing. In order to make experimental comparison with the existing model and adapt to the algorithm model of this paper, this paper supplements the features on the basis of the original data set, but does not affect the original data set. The data is processed into a 5*5 two-dimensional matrix;
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com