Credible display architecture based on hardware isolation technology, system-on-chip and method
A hardware isolation and display method technology, applied in the direction of internal/peripheral computer component protection, platform integrity maintenance, etc., can solve problems affecting user experience, insufficient support for business scenarios, and inability to obtain display content in a trusted display environment, etc., to achieve The effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0071] A trusted display architecture based on hardware isolation technology, including common operating environment and trusted operating environment;
[0072] An ordinary operating system is deployed in the ordinary operating environment, the ordinary operating system includes ordinary display components, and the ordinary operating system runs ordinary applications;
[0073] The trusted operating environment deploys a trusted operating system, the trusted operating system includes a trusted display component, and the trusted operating system runs trusted applications;
[0074] The normal display component drives a normal display input unit and a normal display output unit, and the trusted display component drives a trusted display input unit and a trusted display output unit;
[0075] Alternatively, the ordinary display component drives the common display input unit, and the trusted display component drives the trusted display input unit and the display output unit.
[0076...
Embodiment 2
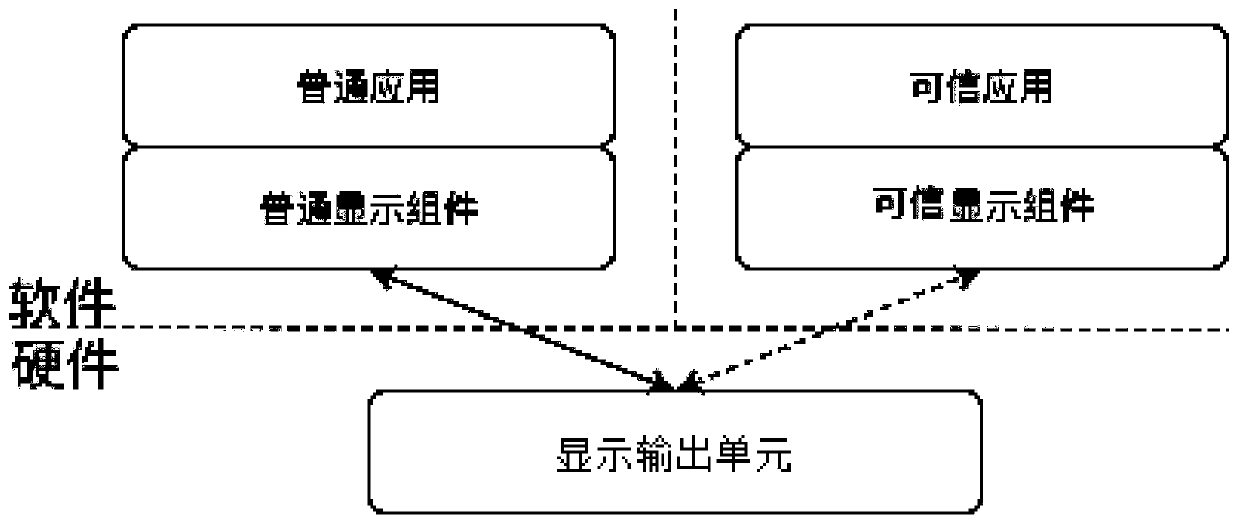
[0082] Embodiment 2 On the basis of Embodiment 1, it provides an implementation method of a completely dedicated display output unit for common display components and trusted display components, that is, each of the trusted operating system and the common operating system has a display output that can independently complete the display function. unit.
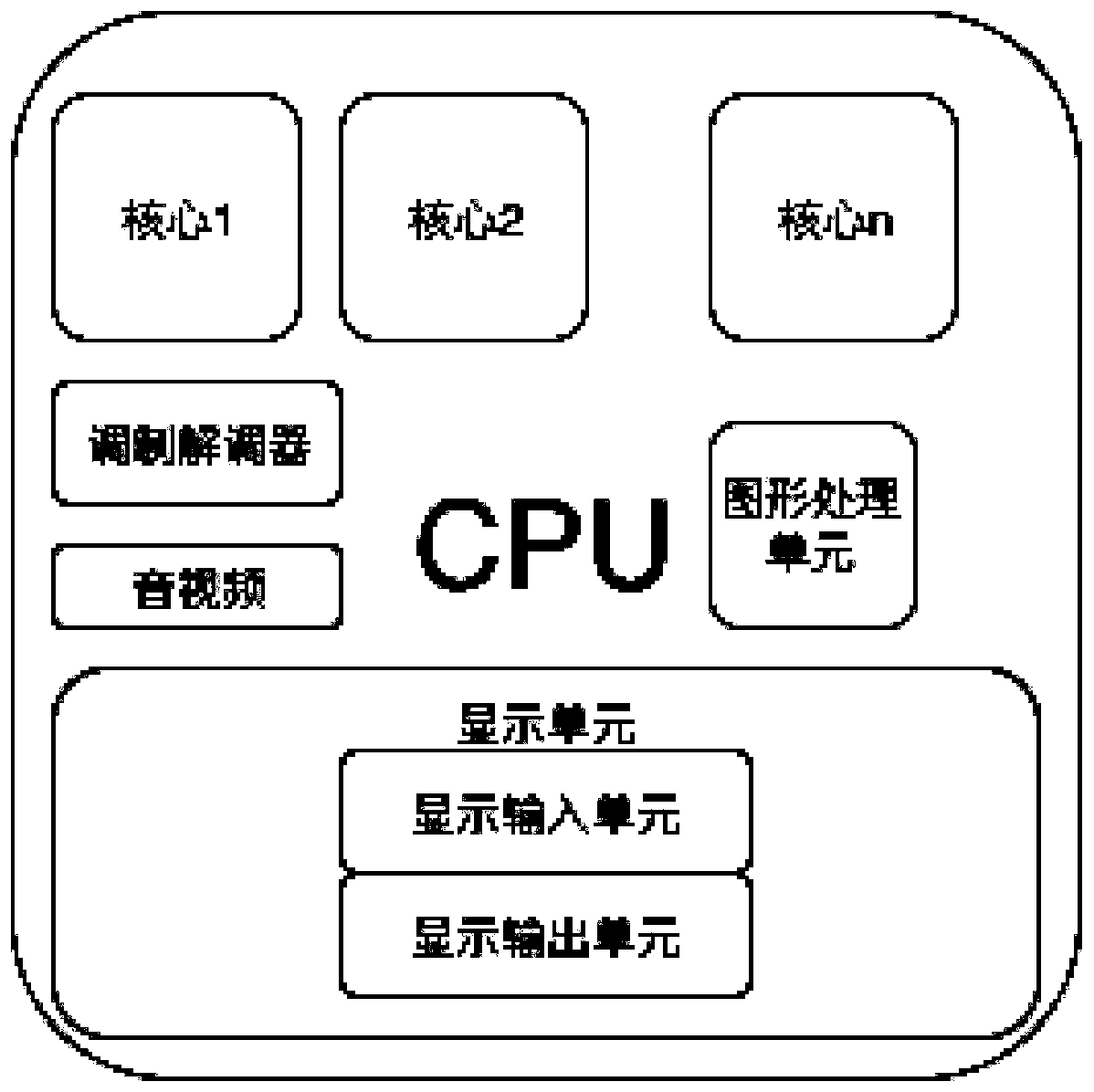
[0083] The trusted display architecture of this embodiment can be found in image 3 , the two display output units each display their corresponding data without interfering with each other. The module diagram of the system-on-chip adopting the trusted display architecture can be found in Figure 4 .
[0084] When the trusted display architecture is applied specifically, taking a mobile phone as an example, it is only necessary to add a display output unit to the mobile phone. Technically speaking, with the upgrade of mobile phone products, the CPU is upgraded to 8 cores or more, or the main frequency of a single CPU is highe...
Embodiment 3
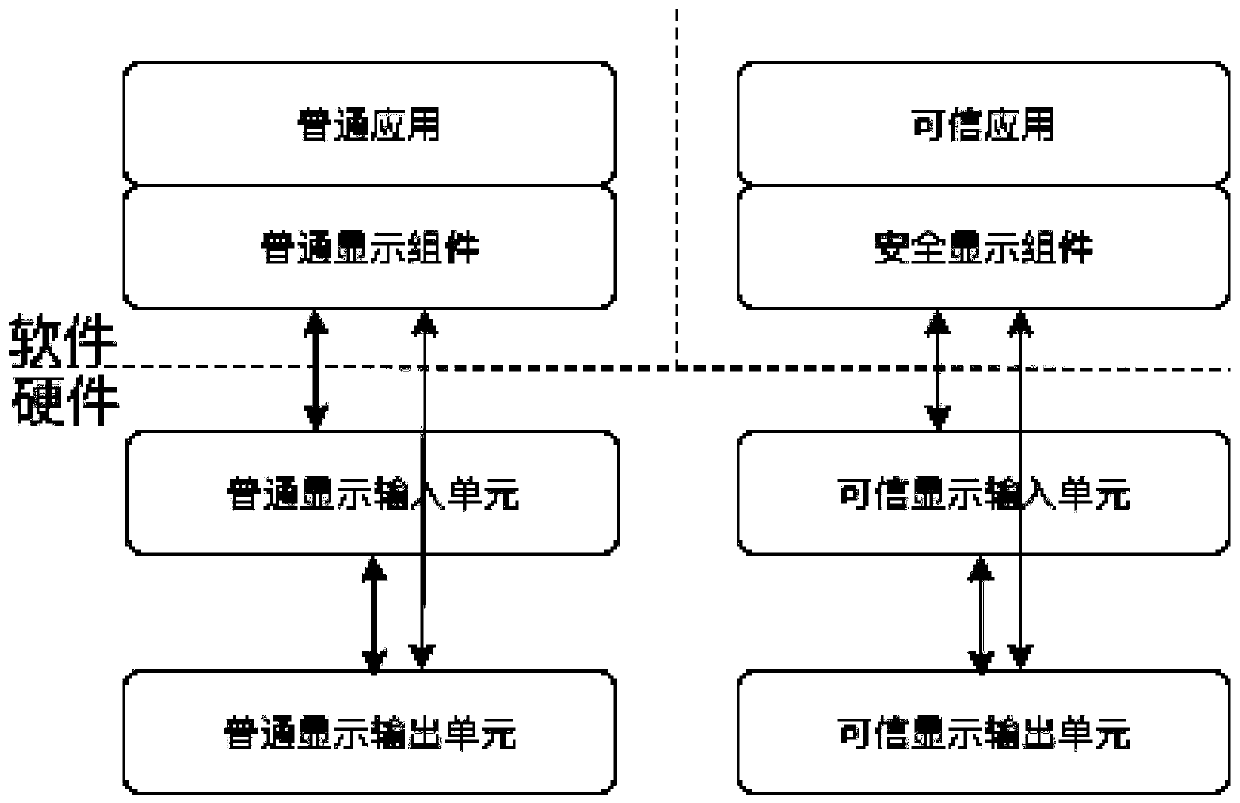
[0097] Embodiment 3 On the basis of other embodiments, it provides the implementation of some dedicated display output units of common display components and trusted display components. Then the preprocessed data is transmitted to the display output unit, and displayed in a superimposed manner.
[0098] The trusted display architecture of this embodiment can be found in Figure 5 , generally, common display input units are configured, accessed and used by common operating systems and common applications. Trusted display input units and display output units can only be configured, accessed and used by trusted operating systems and trusted applications. The module diagram of the system-on-chip adopting the trusted display architecture can be found in Figure 6 .
[0099] In addition, this embodiment also provides a trusted display method based on hardware isolation technology, which operates under the trusted display architecture described in this embodiment. When the common ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com