A Big Data Security Framework System Based on Identity Authentication
An identity authentication and framework system technology, applied in the field of big data security, can solve problems such as password attacks and system overload, and achieve the effect of improving stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
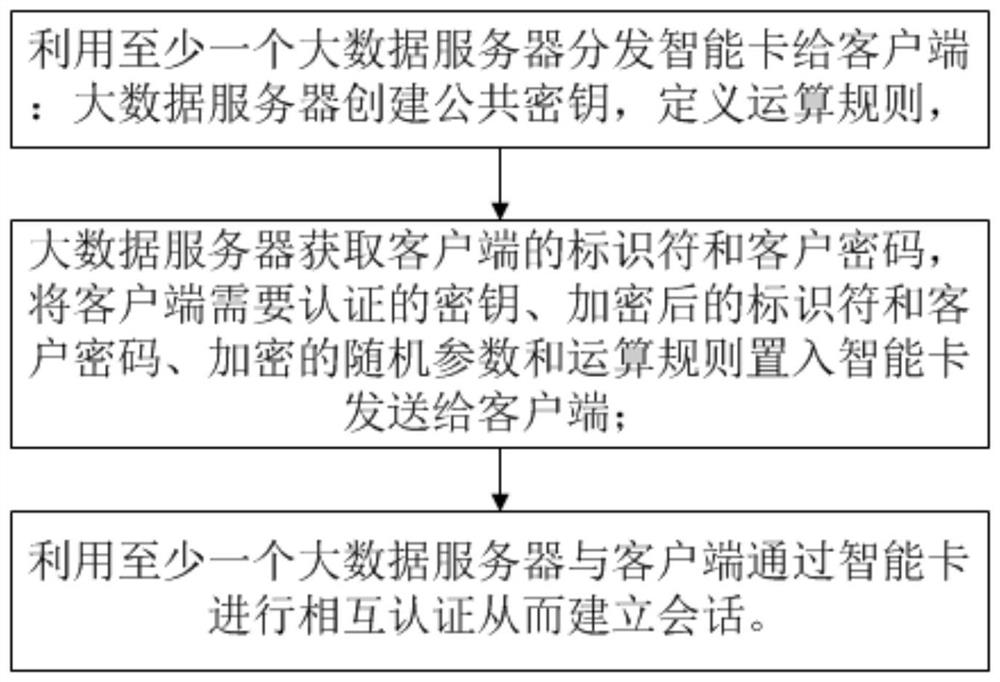
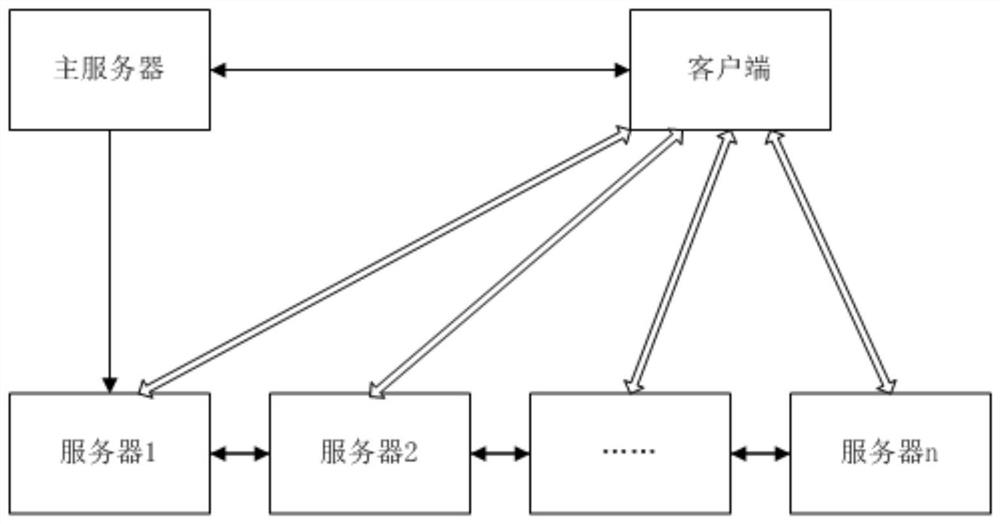
[0035] The present invention provides a big data security framework system based on identity authentication, comprising at least one big data server,
[0036] And use the big data server to distribute the smart card to the client: the big data server creates the public key, defines the operation rules,
[0037] The big data server obtains the client's identifier and client password, uses the public key and identifier to encrypt the key that the client needs to authenticate, and uses the algorithm to encrypt the identifier and client password, and encrypts random parameters at the same time. The key, encrypted identifier and client password, encrypted random parameters and operation rules are placed in the smart card and sent to the client;
[0038] And use the big data server and the client to conduct mutual authentication through the smart card to establish a session: the big data server accepts the request service from the client and the verification parameters sent by the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com