Method and device for multi-party joint training neural network for security defense
A neural network and security defense technology, applied in the field of information security, can solve problems such as time-consuming, occupation, and large computing resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
[0034] As mentioned above, in order to ensure data security, encryption technology is usually used to process data during the collaborative modeling process of multiple data holders (hereinafter referred to as data parties), resulting in a large amount of computing resources and a lot of time. The computing resources consumed in the training neural network scenario are particularly huge.
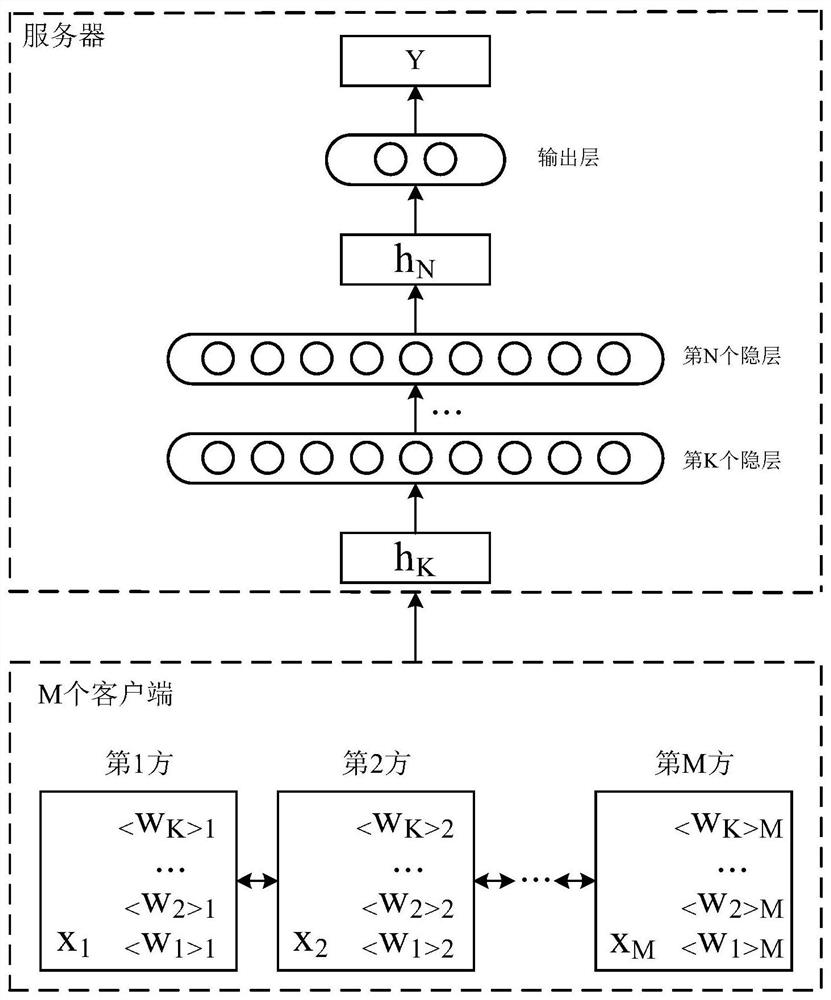
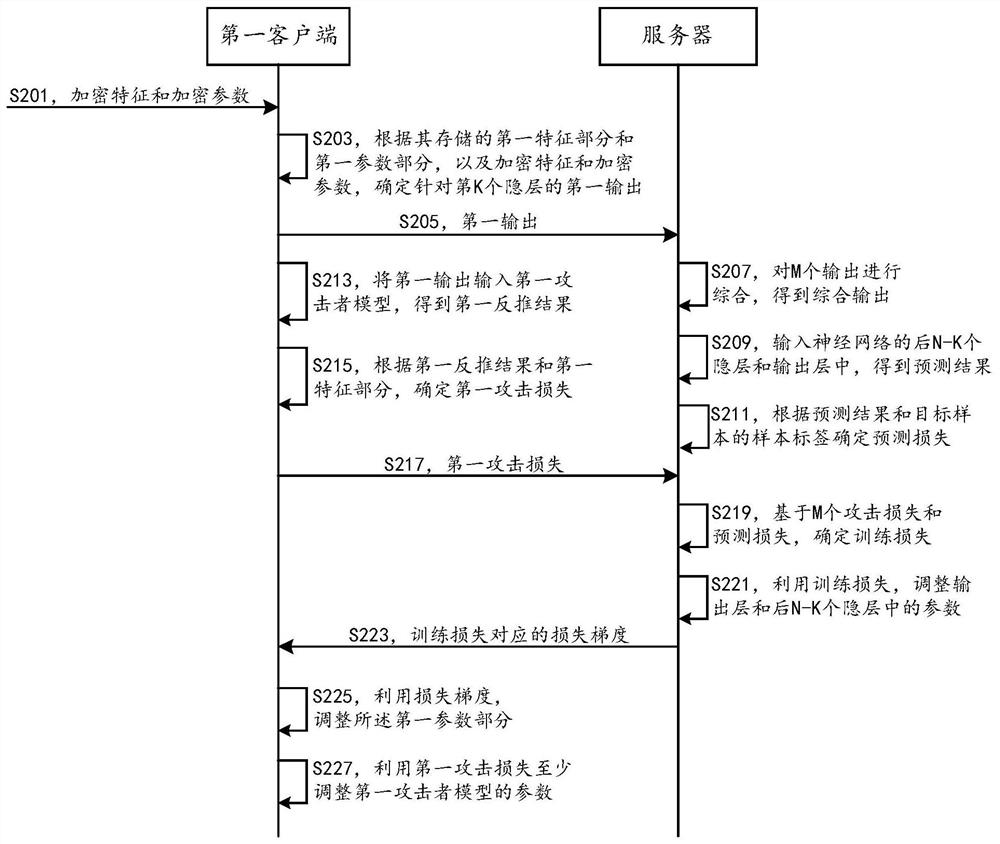
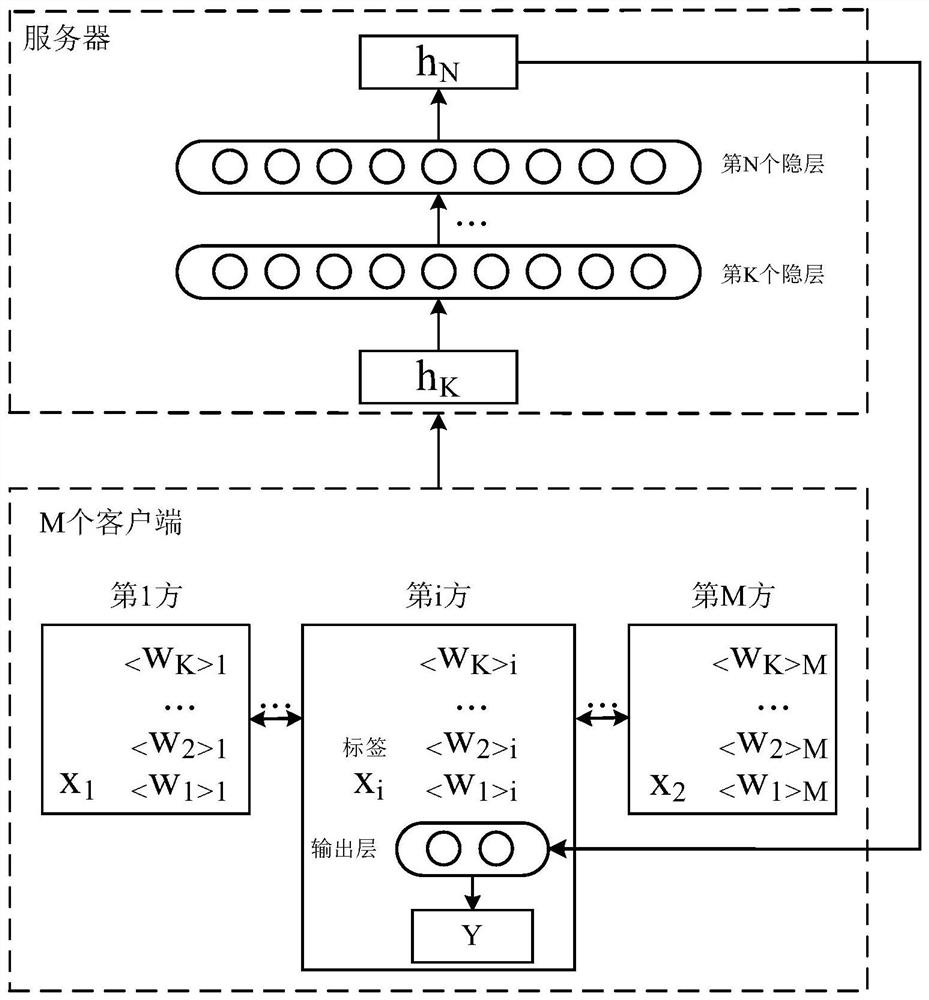
[0035] In this regard, the inventor proposes a method for joint training of neural networks by multiple parties. In this method, besides multiple data parties, the multiple parties also include neutral servers that do not individually belong to any data party. In one embodiment, figure 1 An architecture diagram of a neural network jointly deployed by multiple parties is shown, which includes M clients corresponding to M data parties, and a neutral server. Further, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com