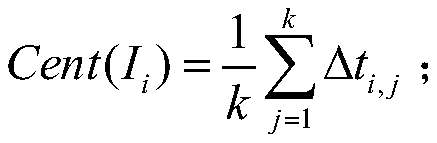Time-type network covert channel detection method based on secret sharing
A covert channel and secret sharing technology, applied in the field of network information security, can solve the problems of low detection efficiency and achieve the effect of improving robustness and high robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
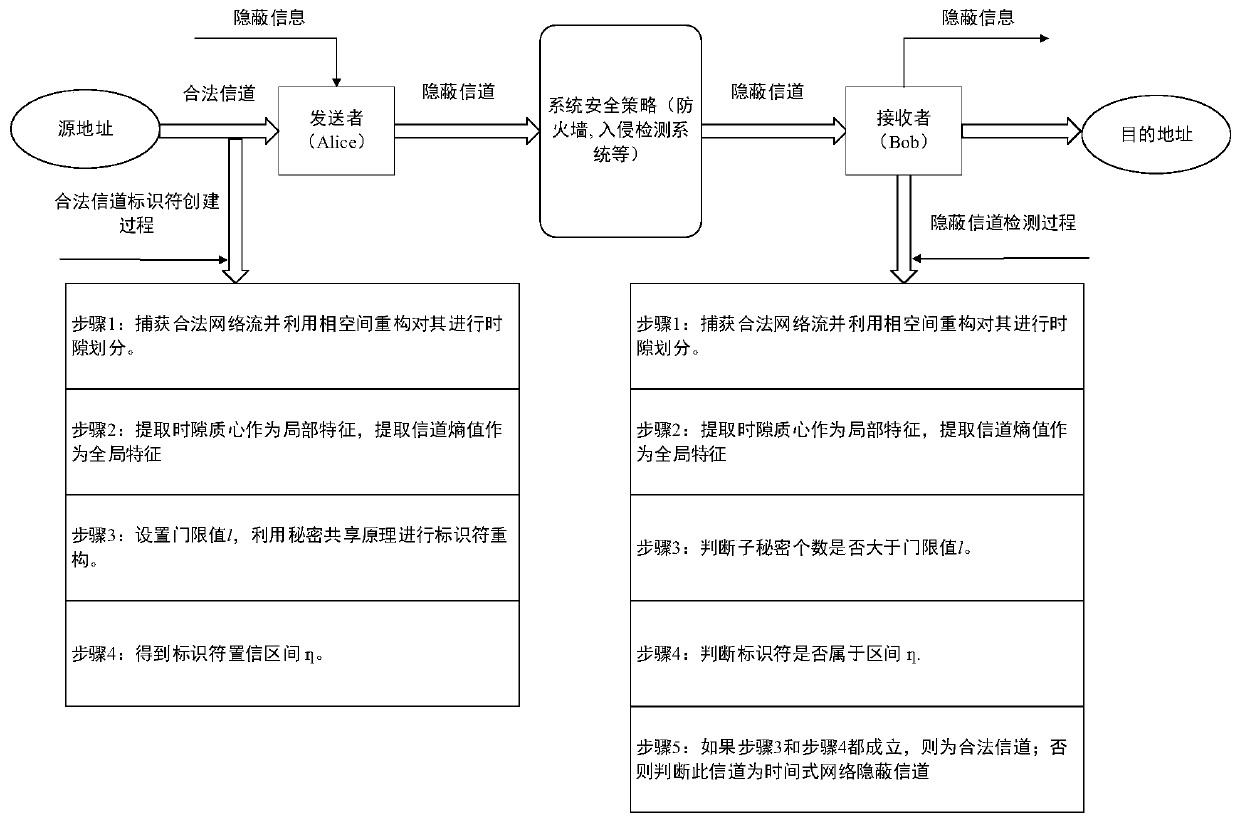
[0098] This embodiment is applicable to real network traffic transmission scenarios, and the present invention can be implemented by a time-based network covert channel detection device, which specifically includes the following steps:
[0099] Step 1: Under the Windows 10 operating system, use Pycharm and Wireshark software to build a detection platform for temporal network covert channels based on secret sharing to detect the existence of temporal network covert channels. In this example, the current network protocol that mainly occupies network data traffic—HTTP network traffic is selected as the carrier of the covert channel. In different embodiments, different network protocols may be selected as the transmission carrier of the covert channel.
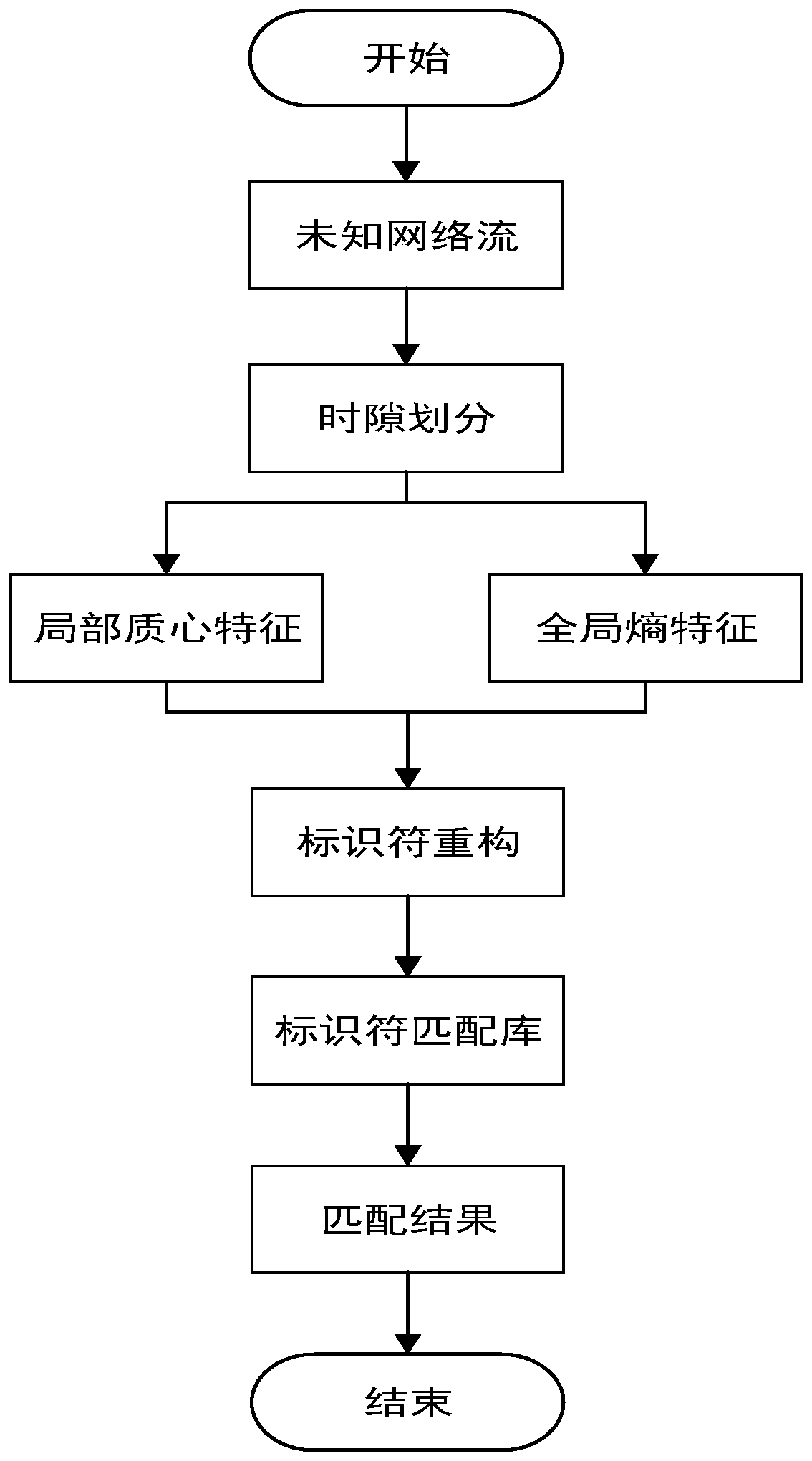
[0100] Step 2: Use Wireshark software to capture the HTTP network traffic in transmission, extract the inter-packet delay IPD through the time stamp of the network traffic, and use the phase space reconstruction method to divide t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com