Negotiation method and system for secret key of secure channel
A security channel and key technology, applied in the field of data security communication, can solve the problem of low security strength and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
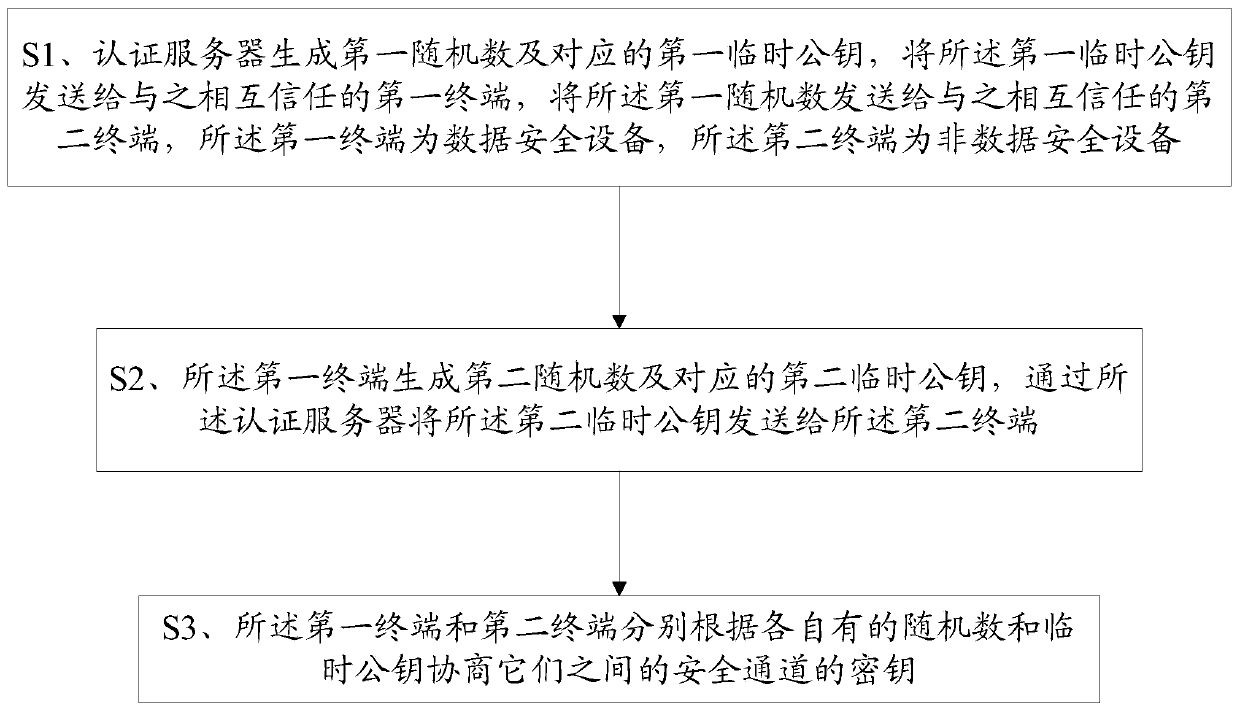
[0168] Please refer to figure 1 , a key negotiation method for a secure channel, comprising:
[0169] S1. The authentication server generates a first random number and the corresponding first temporary public key, sends the first temporary public key to the first terminal that trusts it with it, and sends the first random number to the first terminal that it trusts with it a second terminal, the first terminal is a data security device, and the second terminal is a non-data security device;
[0170] S2. The first terminal generates a second random number and a corresponding second temporary public key, and sends the second temporary public key to the second terminal through the authentication server;
[0171] S3. The first terminal and the second terminal respectively negotiate the key of the secure channel between them according to their respective random numbers and temporary public keys;
[0172] Wherein, the first terminal and the second terminal respectively establish a...
Embodiment 2
[0196]On the basis of the first embodiment, the second embodiment further explains how to realize mutual authentication between the authentication server and the first terminal and the second terminal respectively based on the shared password group, so as to solve the problem of mutual trust between the communication parties:
[0197] Before said step S1, steps are included:
[0198] S01. The first terminal and the second terminal respectively generate their current first key group and second key group according to their respective serial numbers;
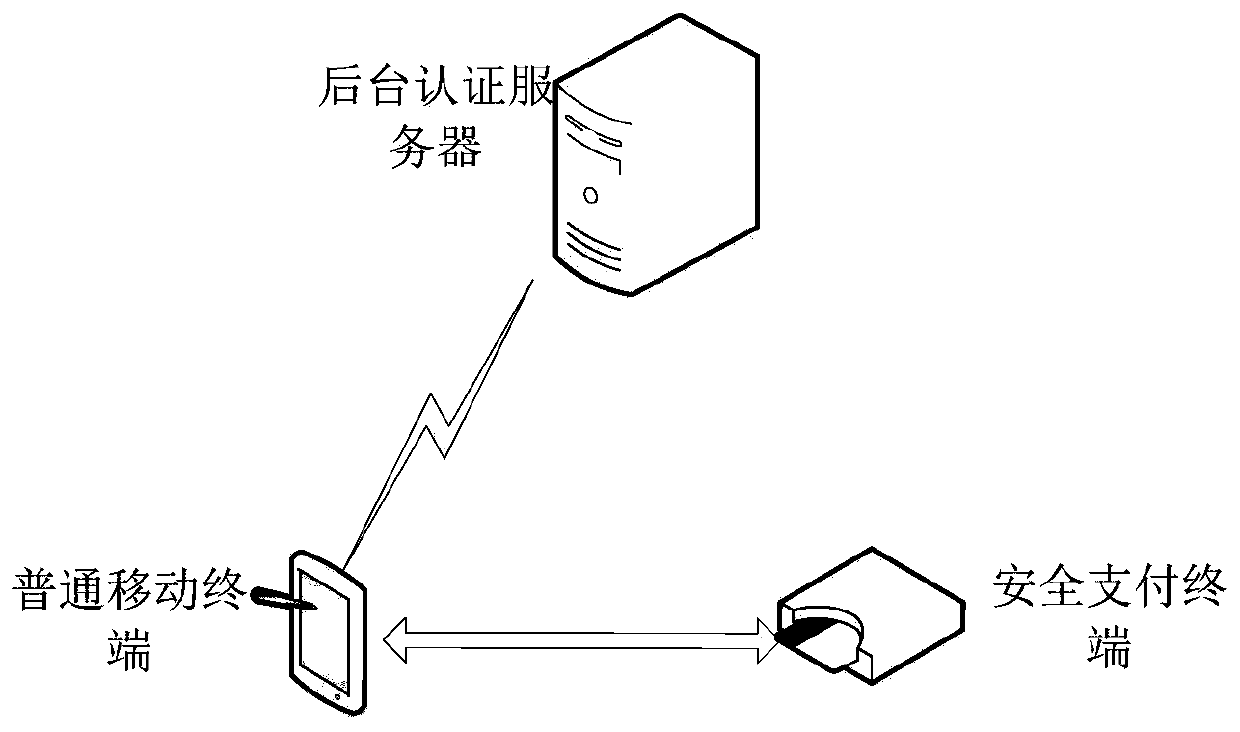
[0199] Specifically, this embodiment is described by using the interaction between the secure payment terminal SPT and the ordinary mobile terminal, plus an application scenario of a background authentication server (Backend Server) that is mutually trusted with the secure payment terminal SPT and the ordinary mobile terminal. The authentication server (Backend Server) is used to prove the identity of the payment terminal to the mo...
Embodiment 3
[0255] In this embodiment, on the basis of Embodiment 1 or Embodiment 2, after the step S3, it also includes:
[0256] The first terminal and the second terminal respectively use the KDF key derivation algorithm to generate the third data encryption key, the first terminal to the second terminal direction authentication code key and the second terminal to the first terminal direction authentication key according to the negotiated key. code key, as a third key group of the secure channel between the first terminal and the second terminal;
[0257] Specifically, based on the principle of the ECDH key agreement protocol, the temporary key abG of the secure channel between SPT and MP_APP is generated;
[0258] Then according to abG, the third key group is generated by using the KDF key derivation algorithm;
[0259] The specific settings of the KDF algorithm are as follows:
[0260] Follow the key derivation method described in to perform key derivation. Optional, the specific ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com