Power secondary system information security operation and maintenance supervision platform
A power secondary system, information security technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as lack of identity verification systems, misguided, and theft of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
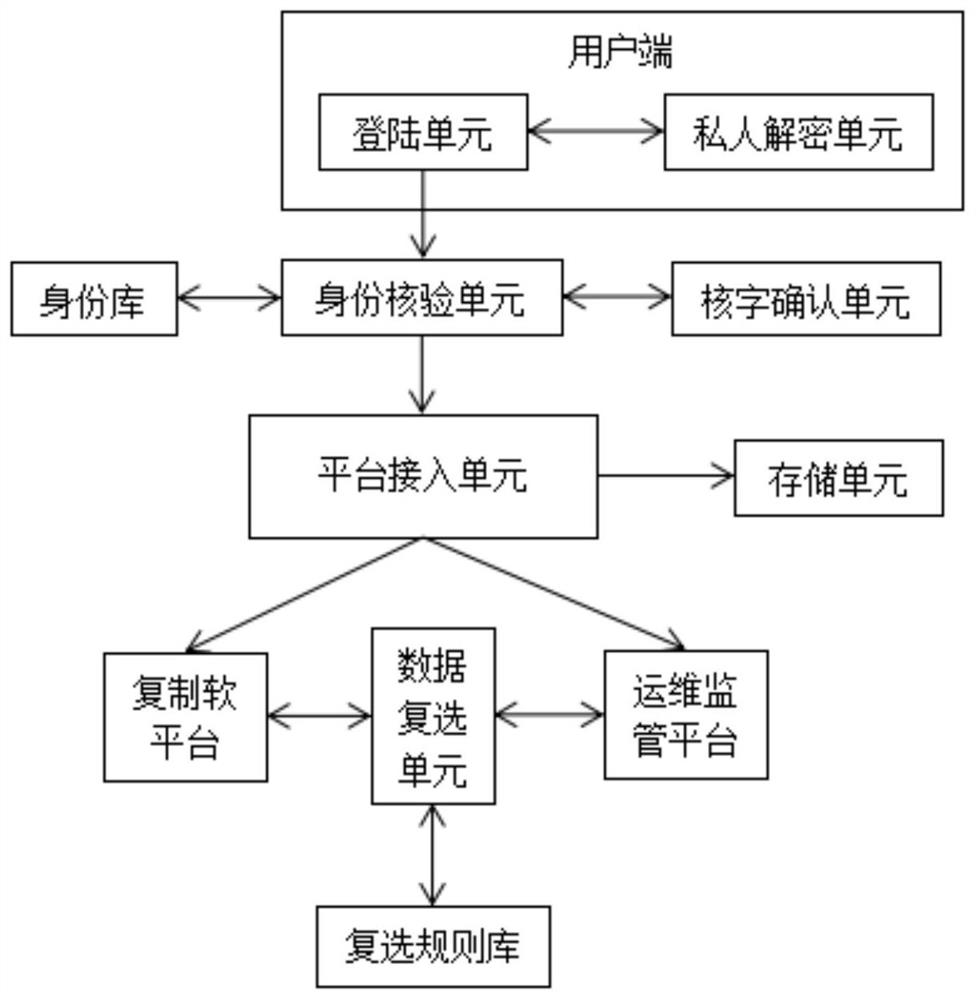
[0047] Such as figure 1 As shown, the power secondary system information security operation and maintenance supervision platform includes a client terminal, an identity database, an identity verification unit, a verification unit, a platform access unit, an operation and maintenance supervision platform, a data check unit, a check rule base and copy soft platform;
[0048] Wherein, the client includes a login unit and a private decryption unit; the login unit is used for the user to input login information, and the login information includes identity information, user password and corresponding login time, the identity information is the user name, and the login time adopts Month, day, hour, minute format;
[0049] Approval information is stored in the identity database, and the approval information is the approved identity information with access rights and the corresponding approved user password;
[0050] The private decryption unit is also used to perform exclusive secre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com