Risk assessment method and device for private data leakage
A privacy data and data technology, which is applied in the field of risk assessment for privacy data leakage, can solve problems such as illegal calls, stealing users' personal privacy information, user privacy leakage, etc., and achieve the effect of improving credibility and usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
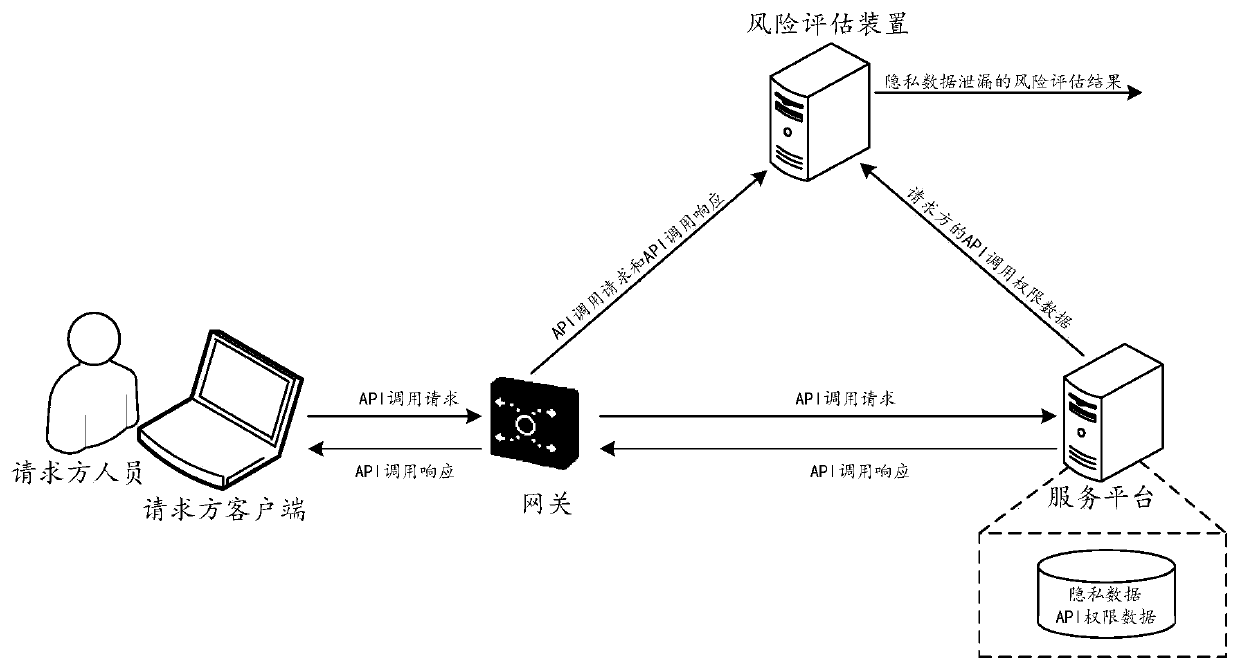
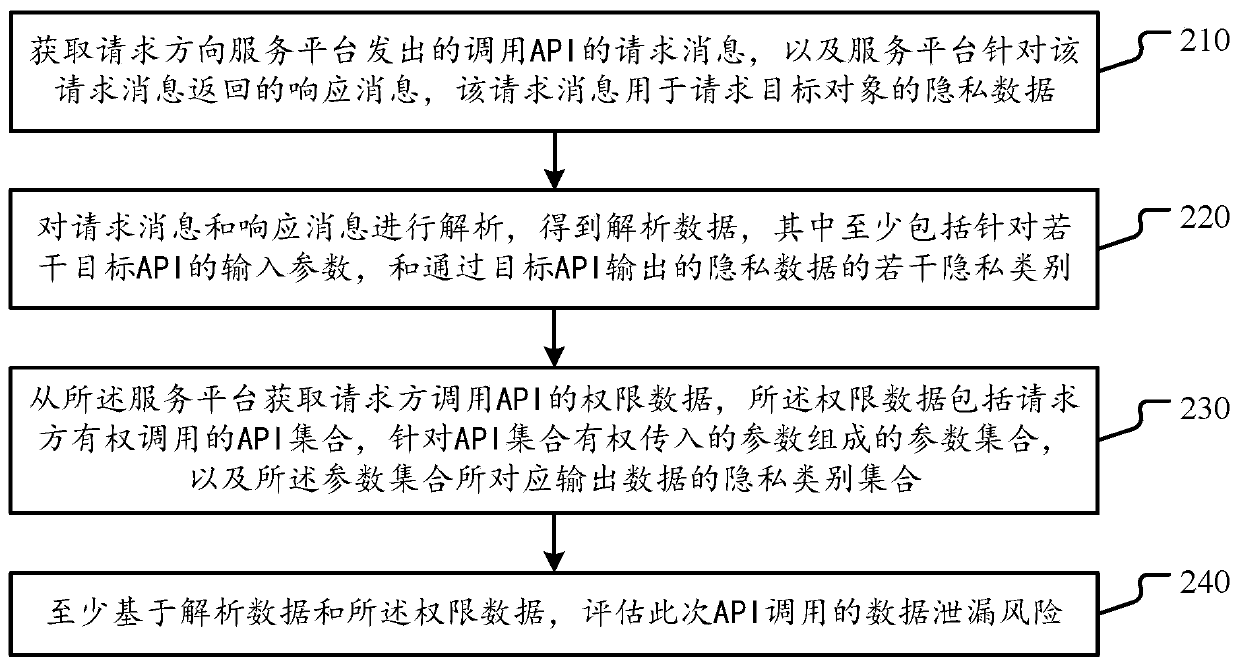
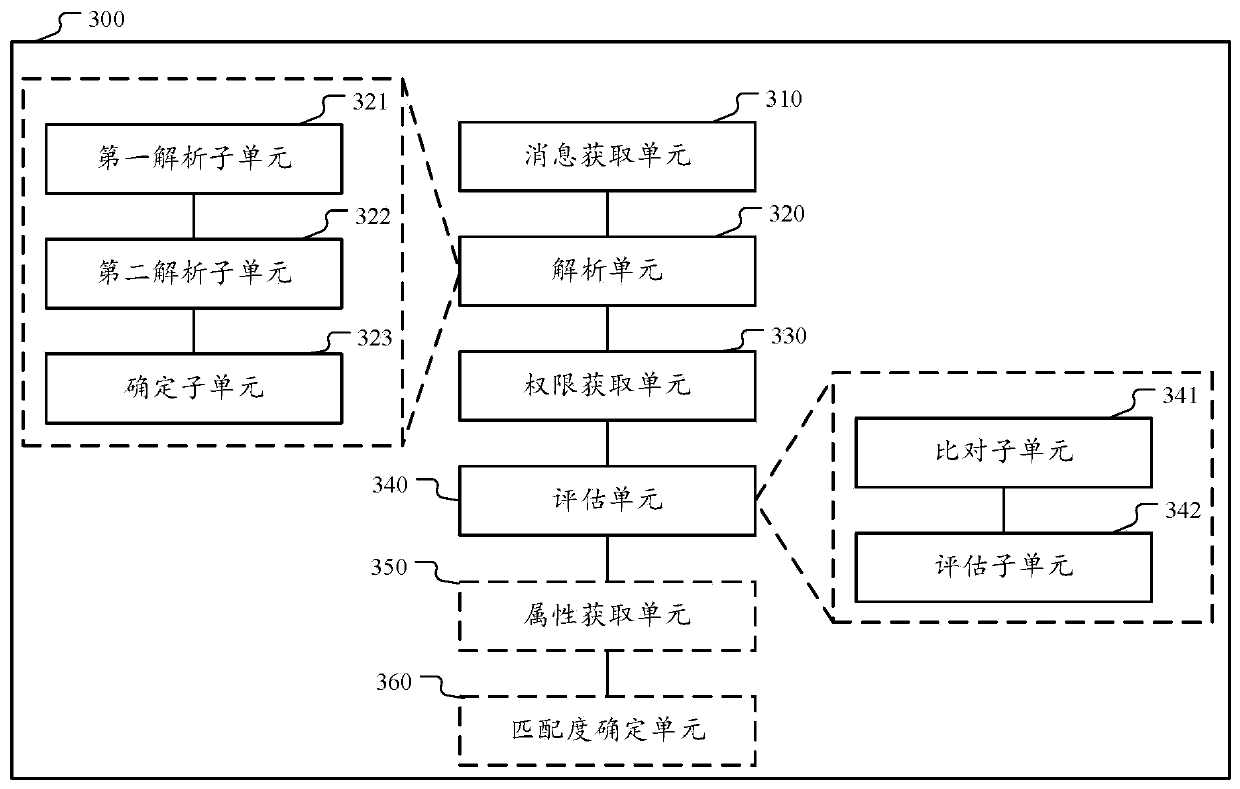
[0027] The following describes the solutions provided in this specification with reference to the drawings.
[0028] As mentioned earlier, there is a risk of data leakage in the current API call process. Specifically, because of the large number of APIs and the difficulty of avoiding API development and management vulnerabilities, the actual output data content of the API and the data actually requested by the requestor or the requester There may be differences in data with usage rights.
[0029] For example, an API that a certain requesting party has no right to call is illegally called by the certain requesting party due to omissions in API authority management, and outputs the user's sensitive personal information, resulting in leakage of user privacy.
[0030] For another example, a requesting party has the right to call a certain API, but its contract data with the service platform only includes part of the data that can be output by the certain API (such as user gender, user ad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com