Authority control method and system under micro-service architecture, and access token
An access token and permission control technology, applied in the field of microservices, can solve problems such as low efficiency, achieve the effect of reducing time cost, improving overall efficiency, and reducing request processing delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
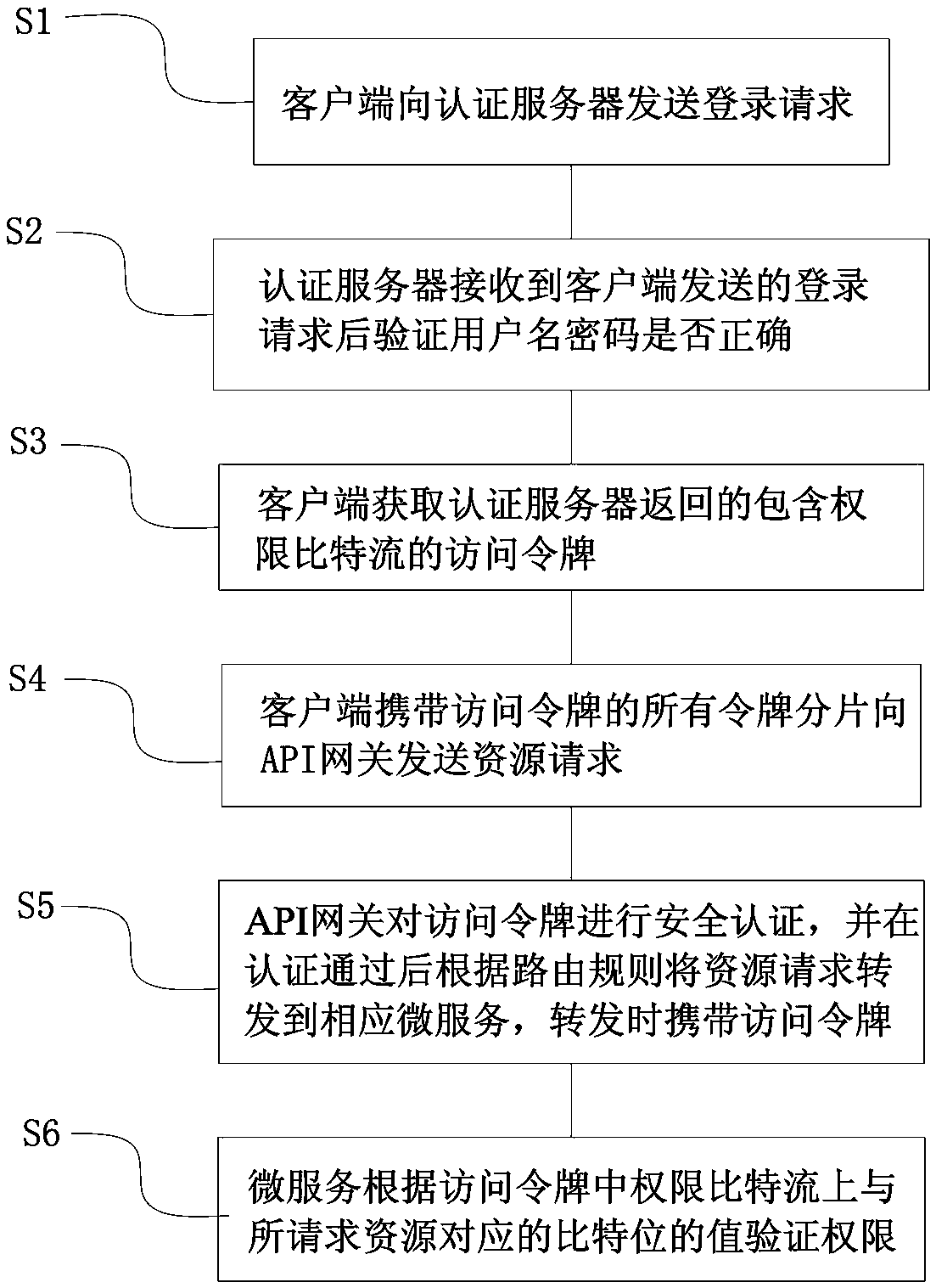
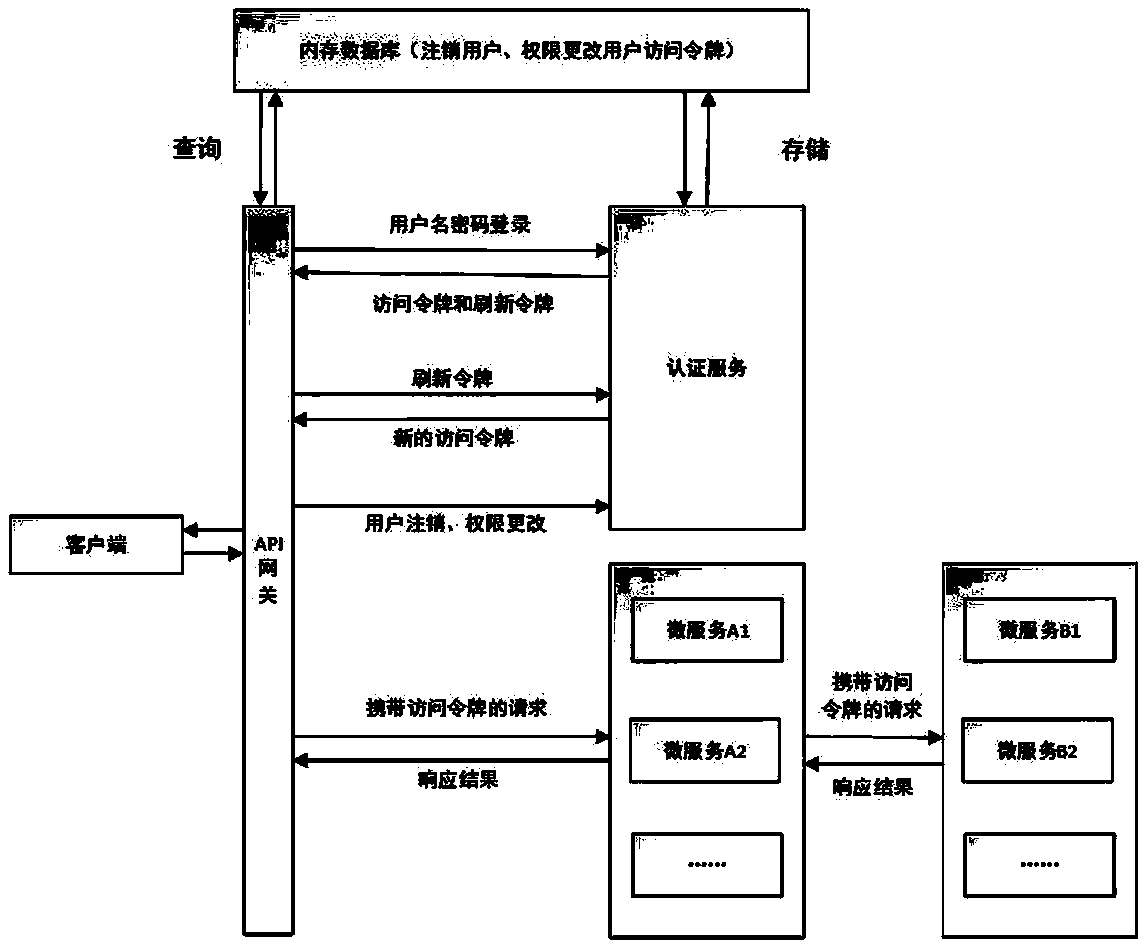
[0066] like figure 1 , figure 2 As shown, this embodiment is a permission control method under the microservice architecture, and the specific steps are as follows:
[0067] S1. The client sends a login request to the authentication server.
[0068] S2. After receiving the login request sent by the client, the authentication server verifies whether the username and password are correct, and if so, generates an access token including the permission bit stream and returns it to the client, otherwise returns an incorrect username or password.
[0069] In this example, the permission bit stream is a binary string with a fixed number of digits. The number of digits in the binary string is determined according to the number of system permissions. Each bit in the binary string corresponds to the permission in the system, and the value of the bit represents the status of the corresponding permission. .
[0070] In this embodiment, the access token has N pieces of token fragments, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com