Method for detecting host infection caused by DGA malicious software
A technology of malware and detection methods, applied in electrical components, transmission systems, etc., can solve the problems of efficient detection effect of DGA domain names, feature selection, and difficulty in filtering out false positives in algorithm optimization, achieving low manual participation in discrimination and high recognition. The effect of high detection rate and high detection coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049]The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
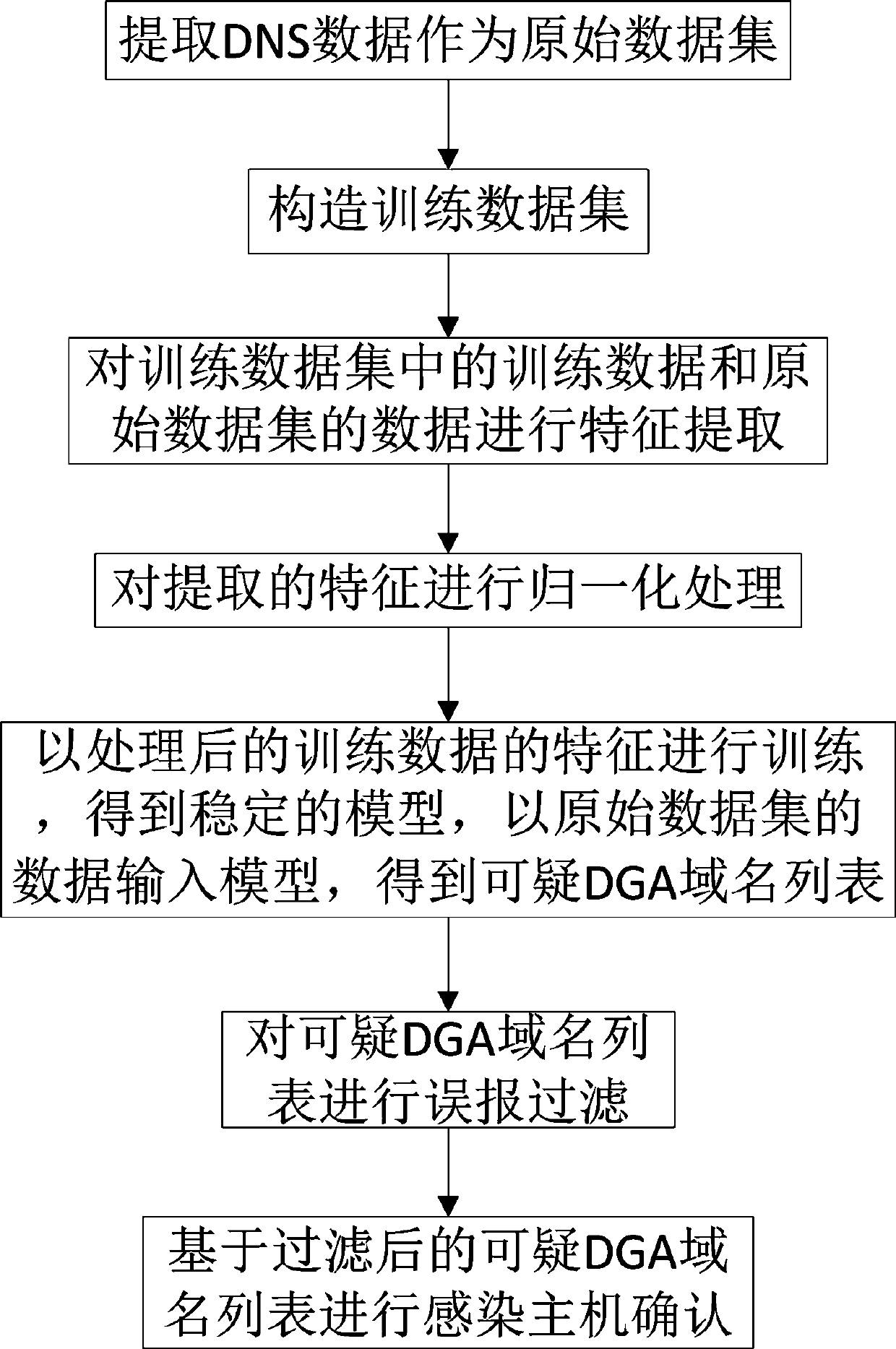
[0050] The invention relates to a method for detecting a DGA malware-infected host, and the method includes the following steps.
[0051] Step 1: Extract DNS data as raw dataset.
[0052] In the step 1, the DNS data is DNS query request data extracted from actual network traffic.
[0053] In the present invention, DNS query request data includes source address (IPv4 address of internal host), destination address (dns server IPv4 address), query domain name (dns rrname), query type (dns rrtype).
[0054] In the present invention, the query domain name with dns.rrtype=A is filtered out as the original data set.
[0055] Step 2: Construct the training data set.
[0056] In the step 2, the domain name of Alexa is used as the negative sample of the training data set, and the domain name of the public D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com