Threat monitoring method of swarm intelligence system suitable for small unmanned aerial vehicle cluster
A small unmanned aerial vehicle and swarm intelligence technology, applied in the field of network security, which can solve the problems of high load, few detection means, and low precision.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further described below in conjunction with the accompanying drawings.
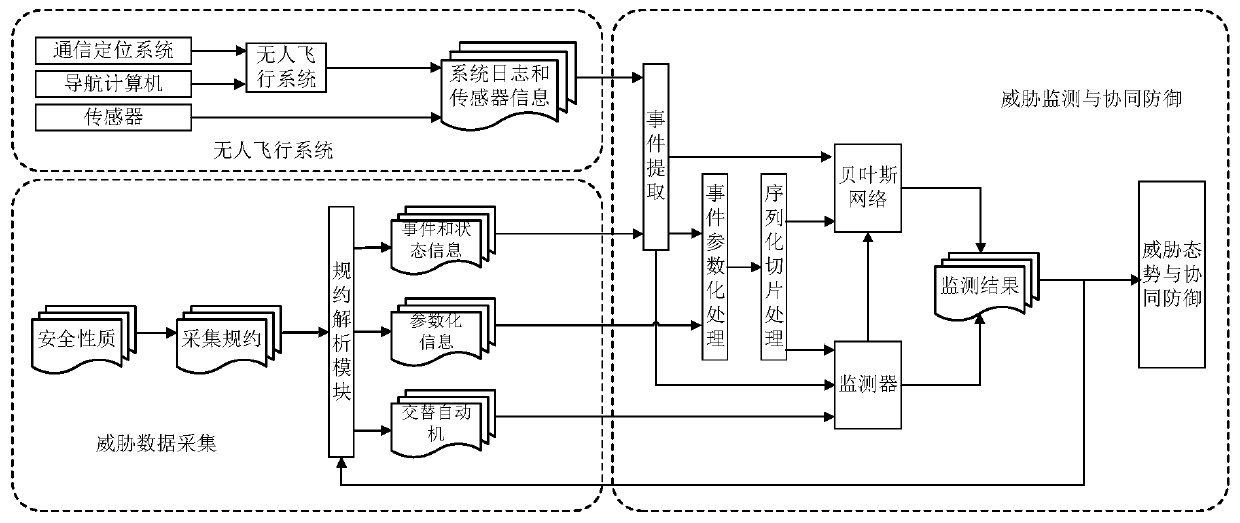
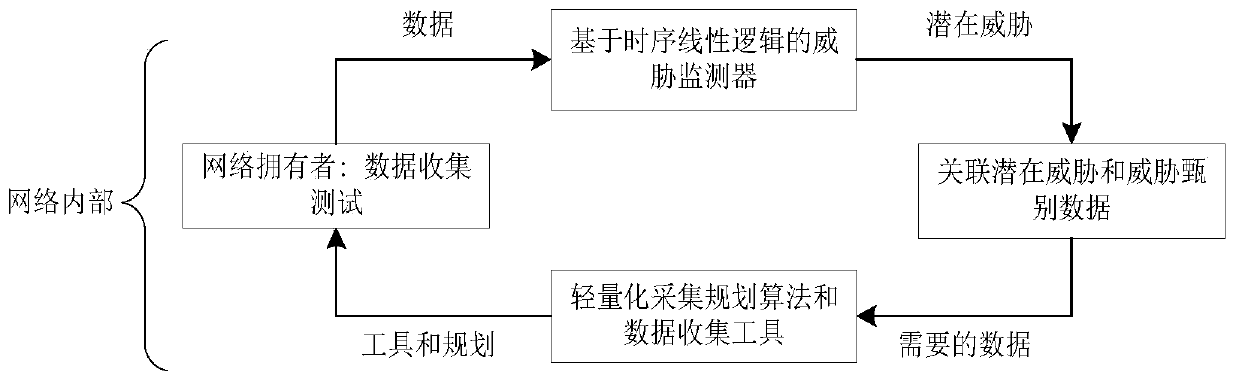
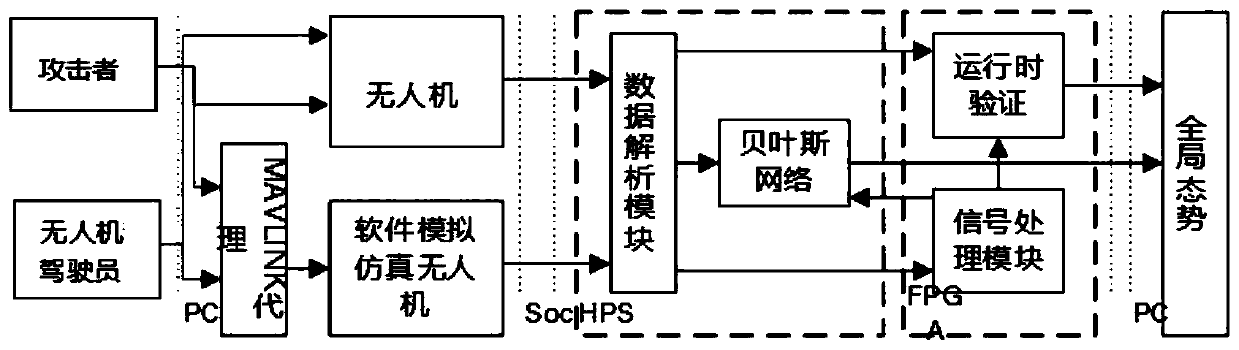
[0028] A swarm intelligence system threat monitoring method suitable for small UAV clusters. Since security events have timing and real-time characteristics, and are closely related to physical components, communication and other information, there is a causal relationship between events and states , the present invention adopts the method of run-time verification to monitor the security threat of the flight system of the UAV cluster by automatically generating a run-time monitor. The threat monitoring framework is as follows: figure 1 , monitoring methods include:
[0029] Lightweight threat data collection: This process mainly defines the security properties of the unmanned aerial system, and uses discrete time-based metric temporal logic to abstract the security properties of the unmanned aerial vehicle system. In the framework of threat data collection The light-w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com