Polar code security coding method in non-orthogonal multiple access system
A non-orthogonal multiple access and access system technology, which is applied in the field of physical layer security coding, can solve the problems of lack of security capacity, low security transmission rate, eavesdropping channel and main channel that do not satisfy the degeneracy relationship, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
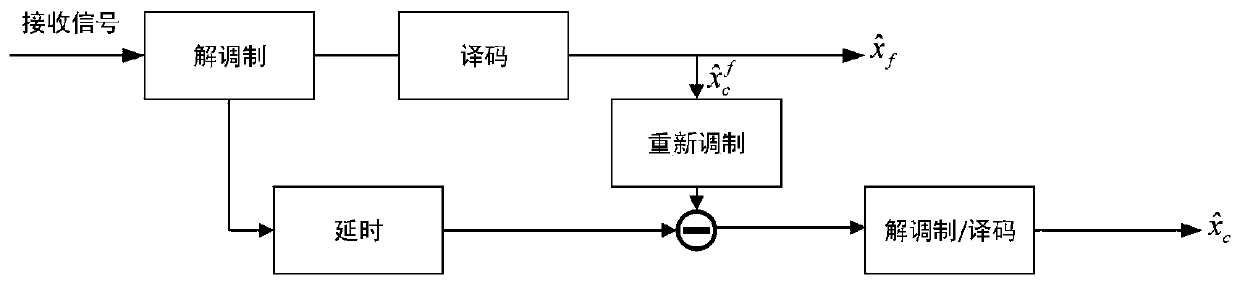
Method used
Image
Examples
Embodiment 1
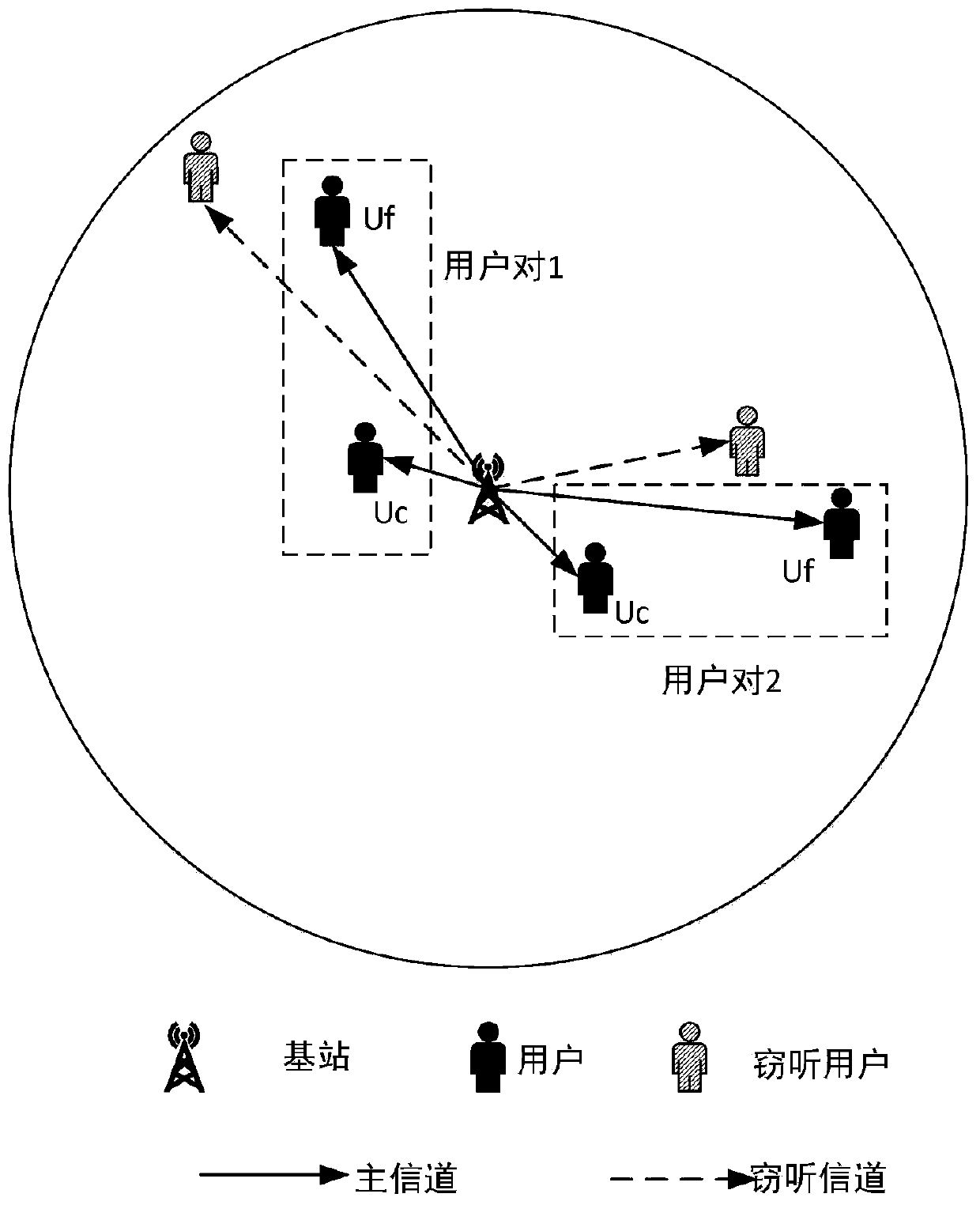
[0061] The system model figure that the present invention relies on is as attached figure 1 As shown, the base station sends messages to different users through the main channel pair, each user pair includes the near-end user uc and the far-end user uf, and each user pair has an eavesdropping user who eavesdrops on the message sent by the base station through the eavesdropping channel. This embodiment considers that in a 5G system, the base station is sending data to two legitimate users through the main channel, and the eavesdropping user eavesdrops on the information of the two legitimate users, where the base station is the sending end and the user is the receiving end.
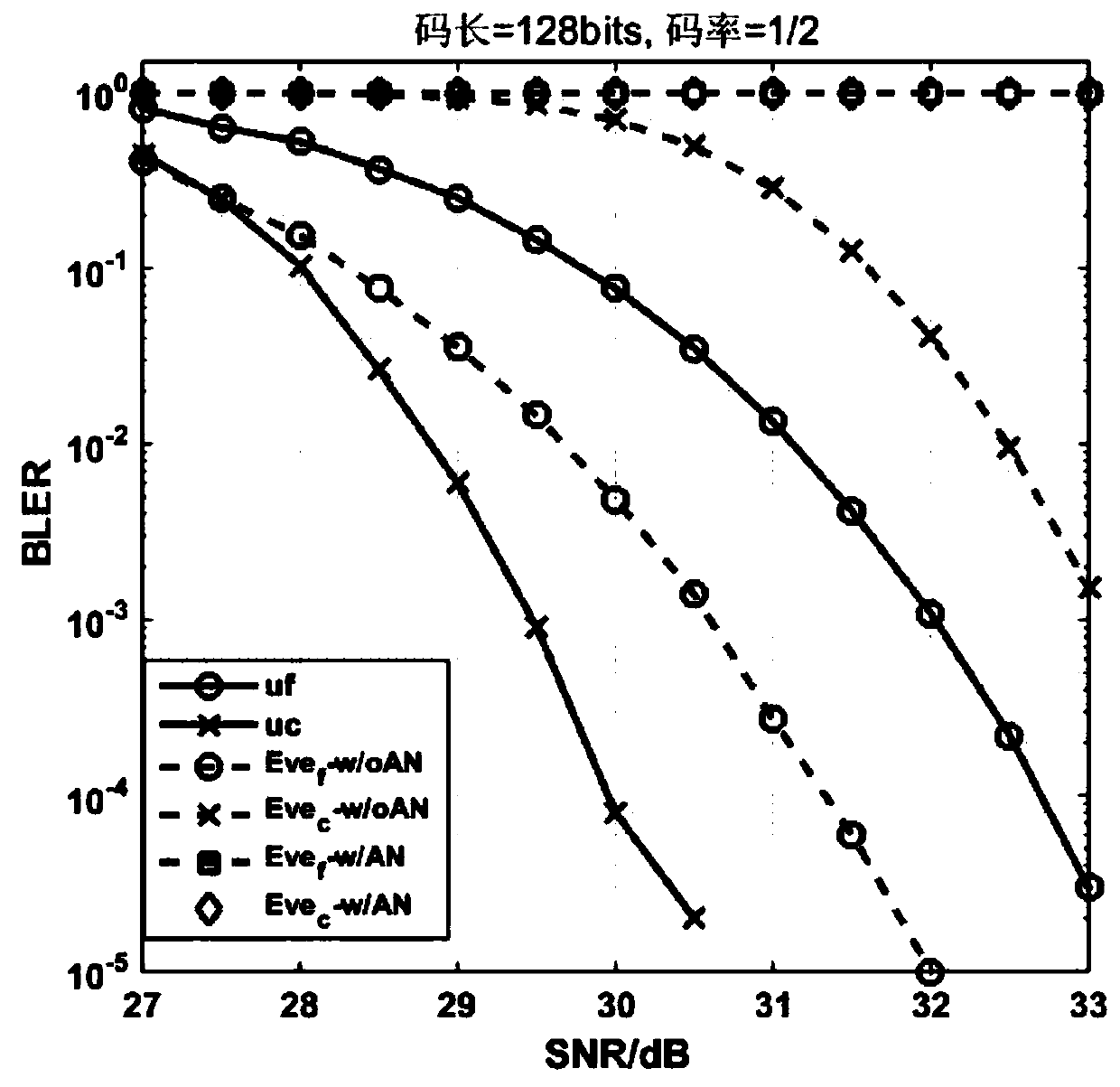
[0062] Suppose the code length is 128 bits, the information sequence length is 64 bits, the code rate is 0.5, the channel model is a fading channel model, the near-end user uc is 5 meters away from the base station, the far-end user is 12 meters away from accounting, and the eavesdropping user is 10 meters ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com