Sensitive word recognition method and device and electronic device
A recognition method and sensitive word technology, applied in the computer field, can solve problems such as high cost, slow response speed, and complicated implementation process, and achieve the effect of improving speed, fast response speed, and simplifying the operation process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
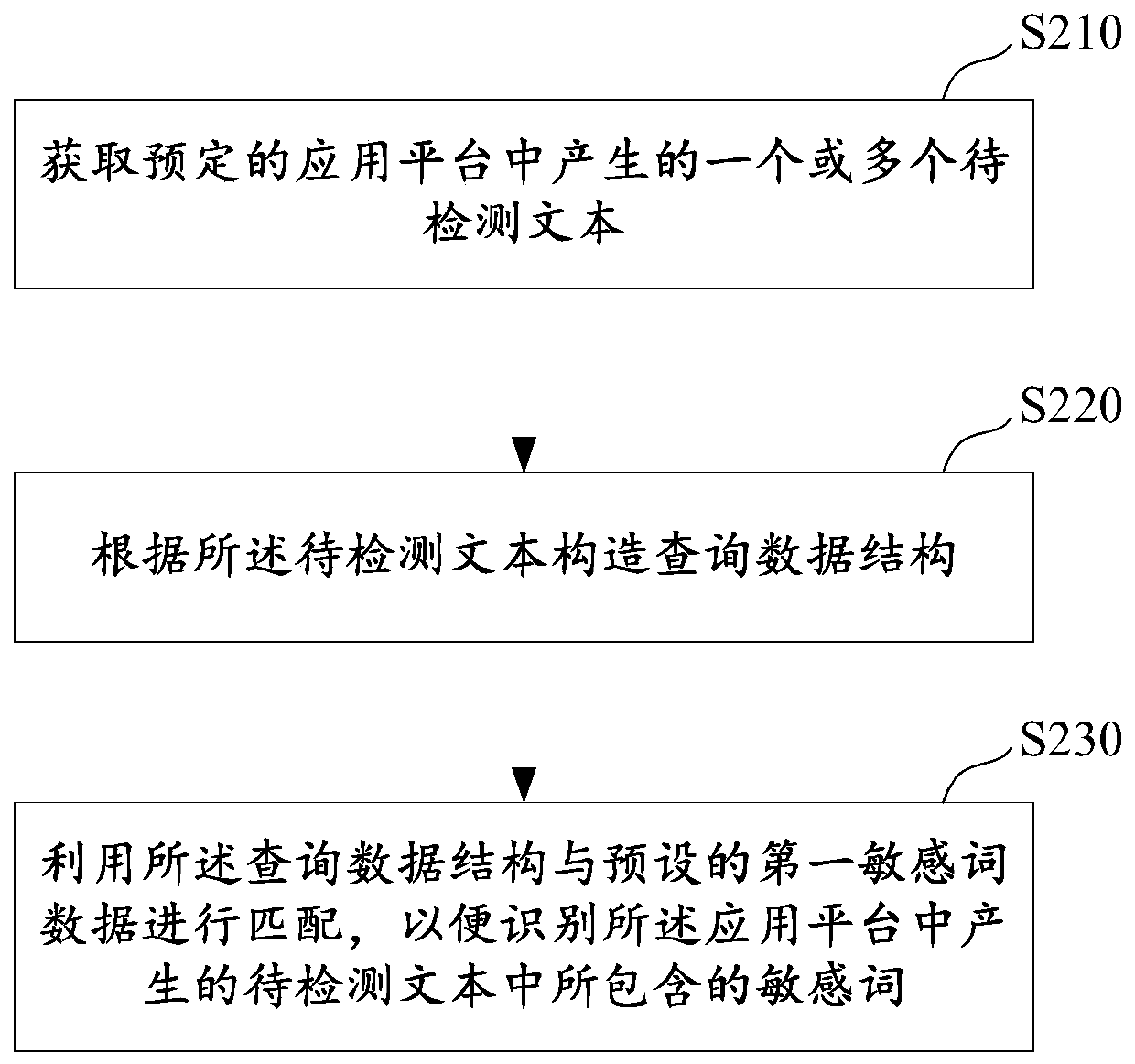
[0034] figure 2 A schematic flowchart of a method for identifying sensitive words provided in Embodiment 1 of this specification, the method may specifically include the following steps:
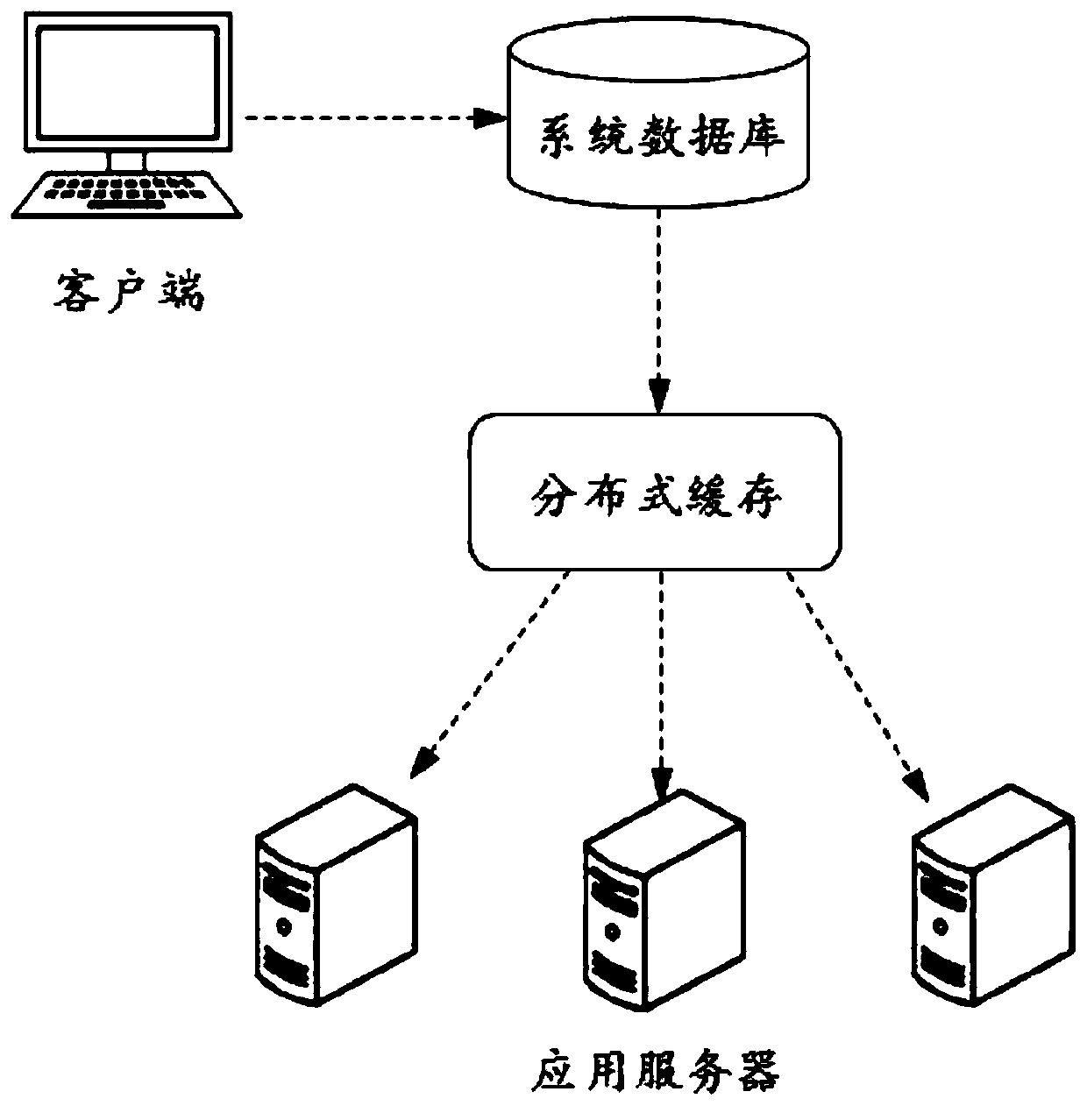
[0035] In step S210, one or more texts to be detected generated in a predetermined application platform are acquired.
[0036] In one or more embodiments of this specification, since the scene of sensitive word recognition includes sensitive word recognition on the text content published in the application platform, it is necessary to extract the text to be detected from the application platform before formal detection; , when the user (here refers to the user who publishes information on the application platform) edits the text content, he can first upload the text content to the server of the application platform, and the application server publishes the text content to the interface of the application platform for display , after the platform perceives the text generated by the user (su...
Embodiment 2
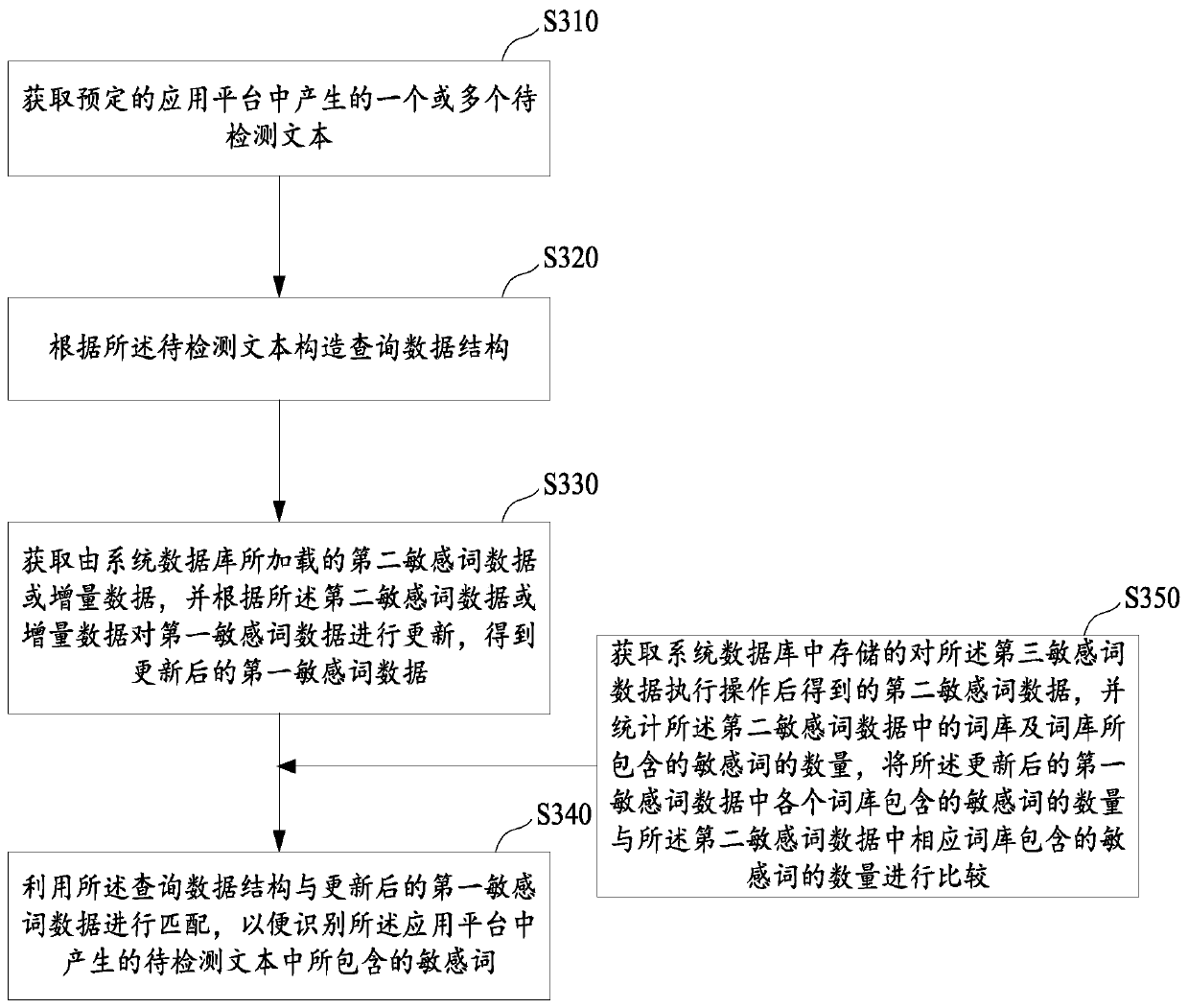
[0064] image 3 A schematic flowchart of a method for identifying sensitive words provided in Embodiment 2 of this specification, the method may specifically include the following steps:
[0065] Step S310, acquiring one or more texts to be detected generated in a predetermined application platform.
[0066] Step S320, constructing a query data structure according to the text to be detected.
[0067] Step S330, obtain the second sensitive word data or incremental data loaded by the system database, and update the first sensitive word data according to the second sensitive word data or incremental data, and obtain the updated first sensitive word data data;
[0068] Step S340, using the query data structure to match the updated first sensitive word data, so as to identify the sensitive words included in the text to be detected generated in the application platform.
[0069] Compared with Embodiment 1, Embodiment 2 adds an operation of updating the first sensitive word data b...
Embodiment 3
[0084] Figure 4 A schematic flowchart of a method for identifying sensitive words provided in Embodiment 3 of this specification, the method may specifically include the following steps:
[0085] Step S410, acquiring one or more texts to be detected generated in a predetermined application platform.
[0086] Step S420, constructing a query data structure according to the text to be detected.
[0087] Step S430, write the second sensitive word data or incremental data into the distributed cache through the system database, so that the distributed cache can update the sensitive word data stored by itself according to the second sensitive word data or incremental data The obtained fourth sensitive word data.
[0088] Step S440, obtain the fourth sensitive word data or incremental data loaded by the distributed cache, and update the first sensitive word data according to the fourth sensitive word data or incremental data, and obtain the updated first sensitive word data A sens...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com