Network threat attack feature unified quantification method based on style migration
A technology of attack characteristics and quantification methods, applied in the field of network security technology and network security threats, can solve the problems of long model training time and low training efficiency, so as to improve the network threat perception ability, overcome the problem of dimensional disaster, and improve the detection rate. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
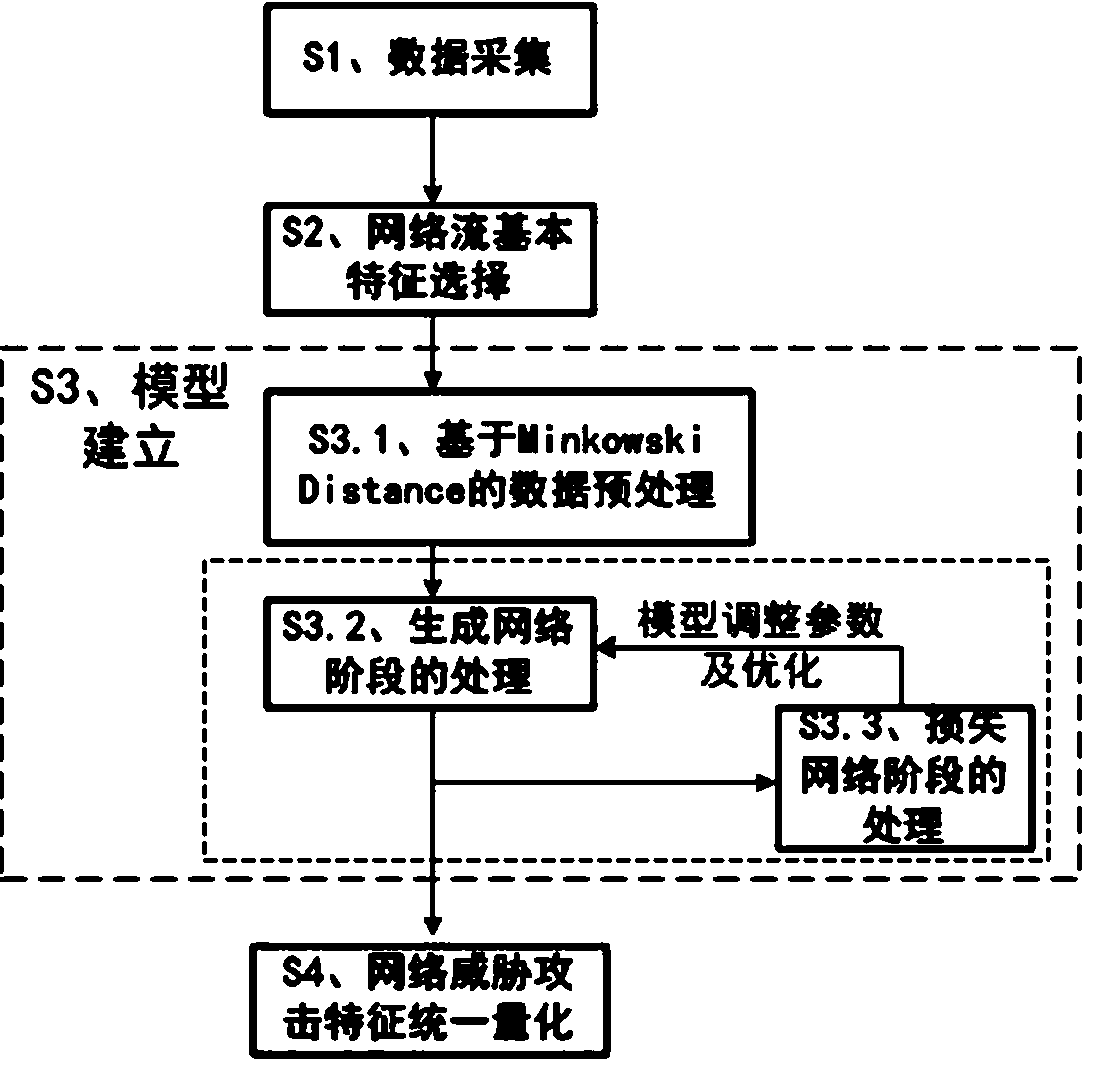
[0054] The present invention designs a unified quantification method of network threat attack features based on style migration, which can automatically extract high-level features of multi-dimensional network threat data, and can also realize unified quantitative processing of multiple threat sources at the same time. In particular, the following setting method is adopted: different The original feature map of the dimension is processed uniformly, including the following steps:
[0055] 1) Data collection: real-time collection of network flow data;
[0056] 2) Select the basic features of the network flow data;
[0057] 3) Use Minkowski Distance to convert the basic features of the selected network flow into native feature maps of different dimensions;
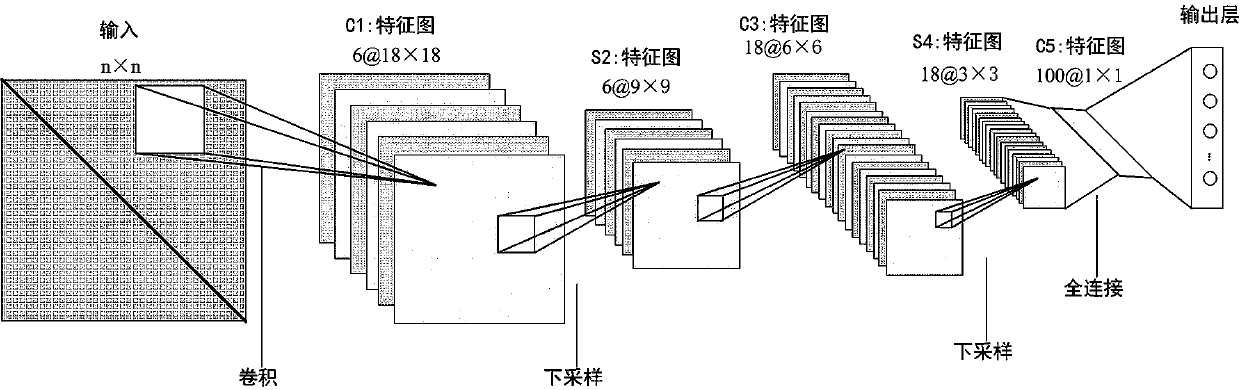
[0058] 4) Use CNN to build a generation network, and input the "native feature map" in the data set into the "generation network" to generate a "result map";
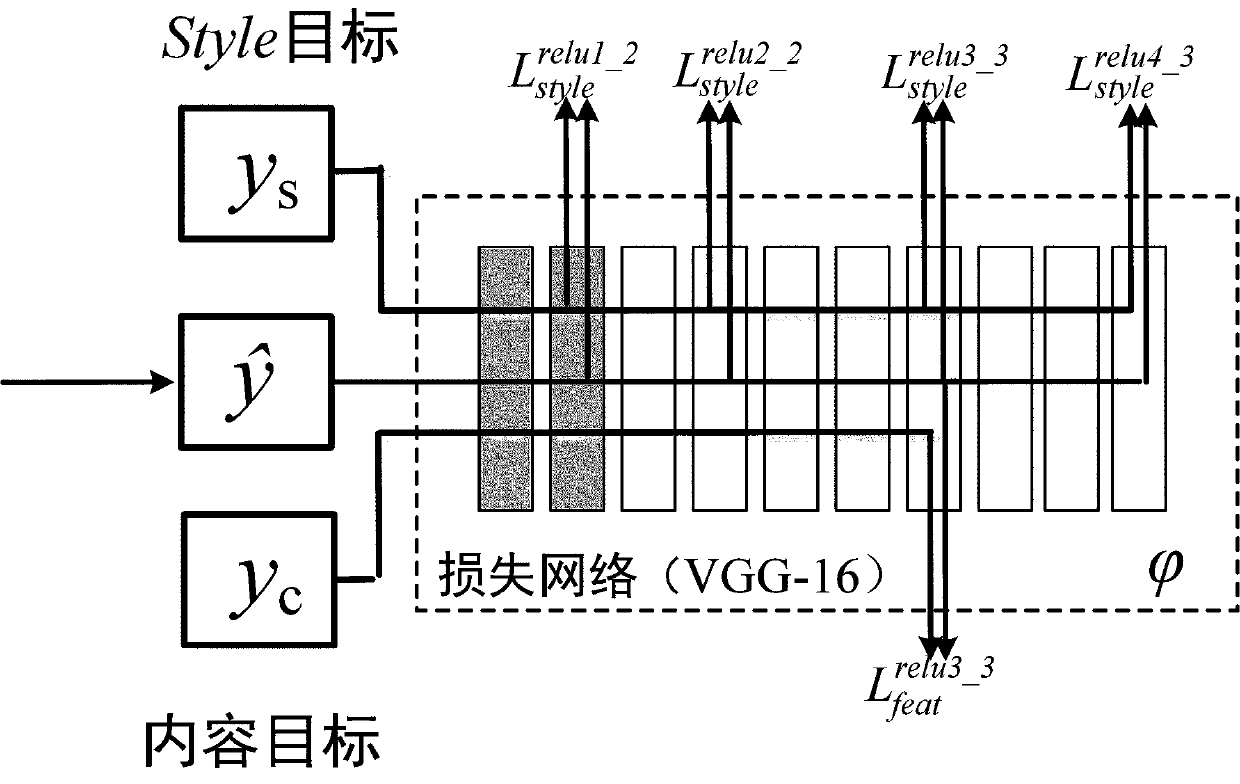
[0059] 5) Extract the high-level features of the original featu...
Embodiment 2
[0080] This embodiment is further optimized on the basis of the above embodiments, a unified quantification method for network threat attack characteristics based on style transfer, such as figure 1 , figure 2 , image 3 shown, including the following steps:
[0081] S1. Data collection:
[0082] Through real-time collection of network flow data, such as basic security detection units such as firewalls, intrusion detection systems, vulnerability scanning systems, anti-virus systems, and terminal security management systems, as well as comprehensive network flow data such as security management platforms and security operation centers, network flow During data collection, the collection content includes packet size, duration, data packet timing, flow duration, message arrival time interval, access domain name, port, IP, URL, DNS and other information.
[0083] S2. Basic feature selection of network flow:
[0084] Select such as source IP address, destination IP address, so...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com