Remote monitoring method and system based on embedded Linux system and storage medium
A remote monitoring and embedded technology, applied in the field of Linux systems, can solve the problems of low security performance of automated terminal equipment, and achieve the effect of protecting data and program security and saving costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
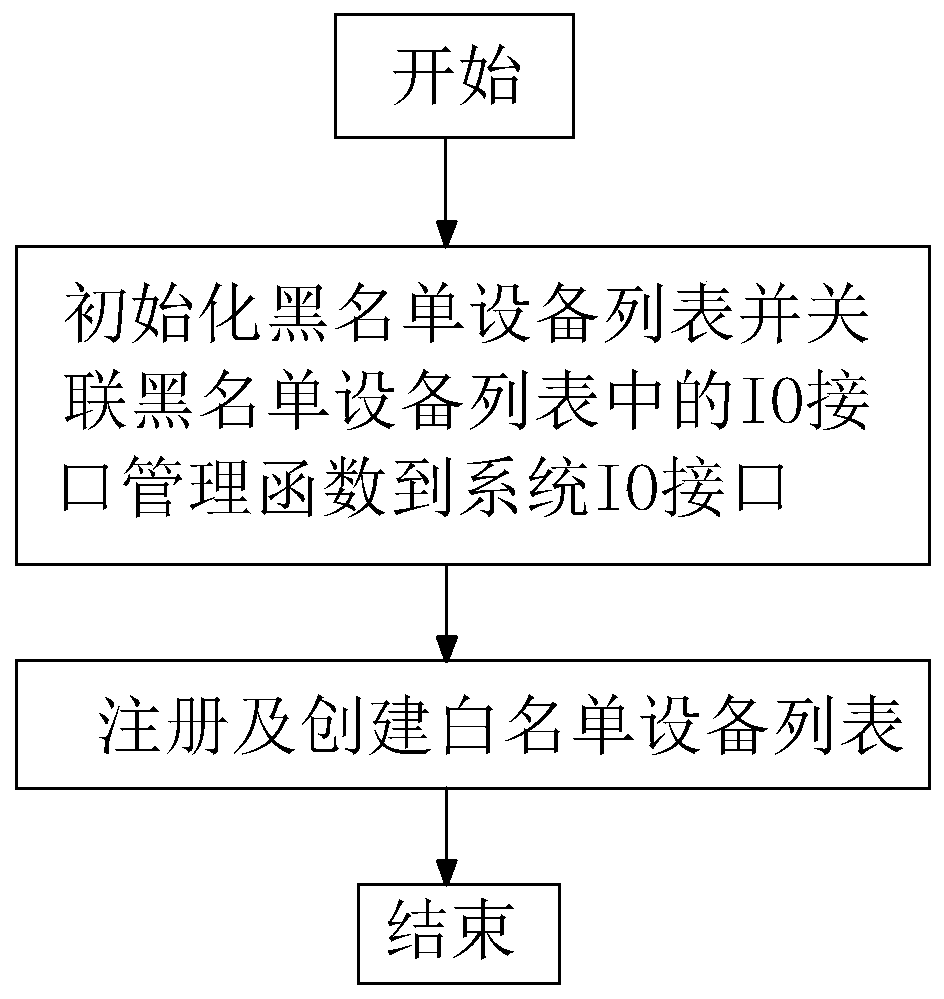
[0076] Embodiment two: refer to image 3 , step S2 is specifically:
[0077] S21. Initialize the blacklist device list and associate the IO interface management function of the blacklist device list to the system IO interface;
[0078] S22. Register and create a whitelist device list.
[0079] After the blacklist module is started, first initialize the blacklist device list to initialize the devices in the blacklist, and then associate the IO interface management function of the blacklist device list to the system IO interface according to the blacklist device list. Associate the IO interface management function to the system IO interface to register and create a whitelist device list, and then end the process of loading and initializing the blacklist module. Create a blacklist device list and a whitelist device list to prevent others from tampering with product data and applications by executing illegal codes using other devices.
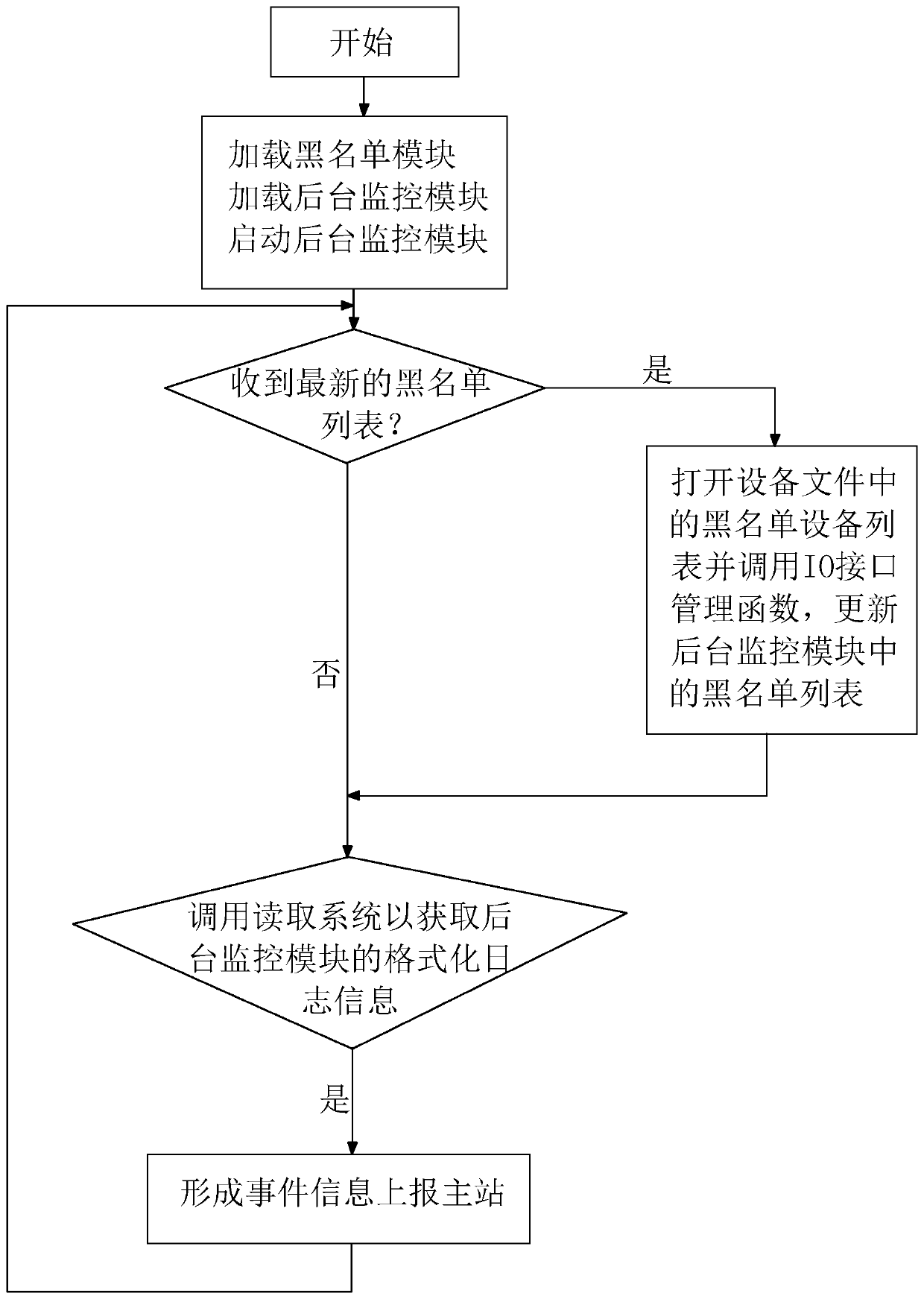
[0080] refer to Figure 4 , after the bl...
Embodiment 3
[0104] Embodiment three: refer to Figure 7 , the embodiment of the present invention discloses a remote monitoring system based on an embedded Linux system, comprising: a blacklist module 100, a background monitoring module 200 and a main control module 300;
[0105] The main control module 300 loads the blacklist module 100 and the background monitoring module 200 to start the background monitoring module 200; the blacklist module 100 is used to initialize and register to create a whitelist device list or a blacklist device list, and associate IO according to the blacklist device list Interface management function to system IO interface; Blacklist module 100 is also used to judge the order type of described IO interface management function to update the blacklist in the blacklist device list or control the opening and closing of background monitoring module 200; Background monitoring module 200, used to save the system default call interface list, and replace the system call...
Embodiment 4
[0107] Embodiment 4: The embodiment of the present invention discloses a computer-readable storage medium, the computer-readable storage medium stores computer-executable instructions, and the computer-executable instructions are used to make the computer execute the embedded-based Remote monitoring method of Linux system.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com