Authentication method based on port forwarding hypertext transfer protocol
A hypertext transmission and port technology, applied in the field of authentication and authentication based on port forwarding hypertext transmission protocol, can solve the problems of network fluctuation, high deployment cost and development cost, affecting normal network use, etc., and achieve the effect of low system consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
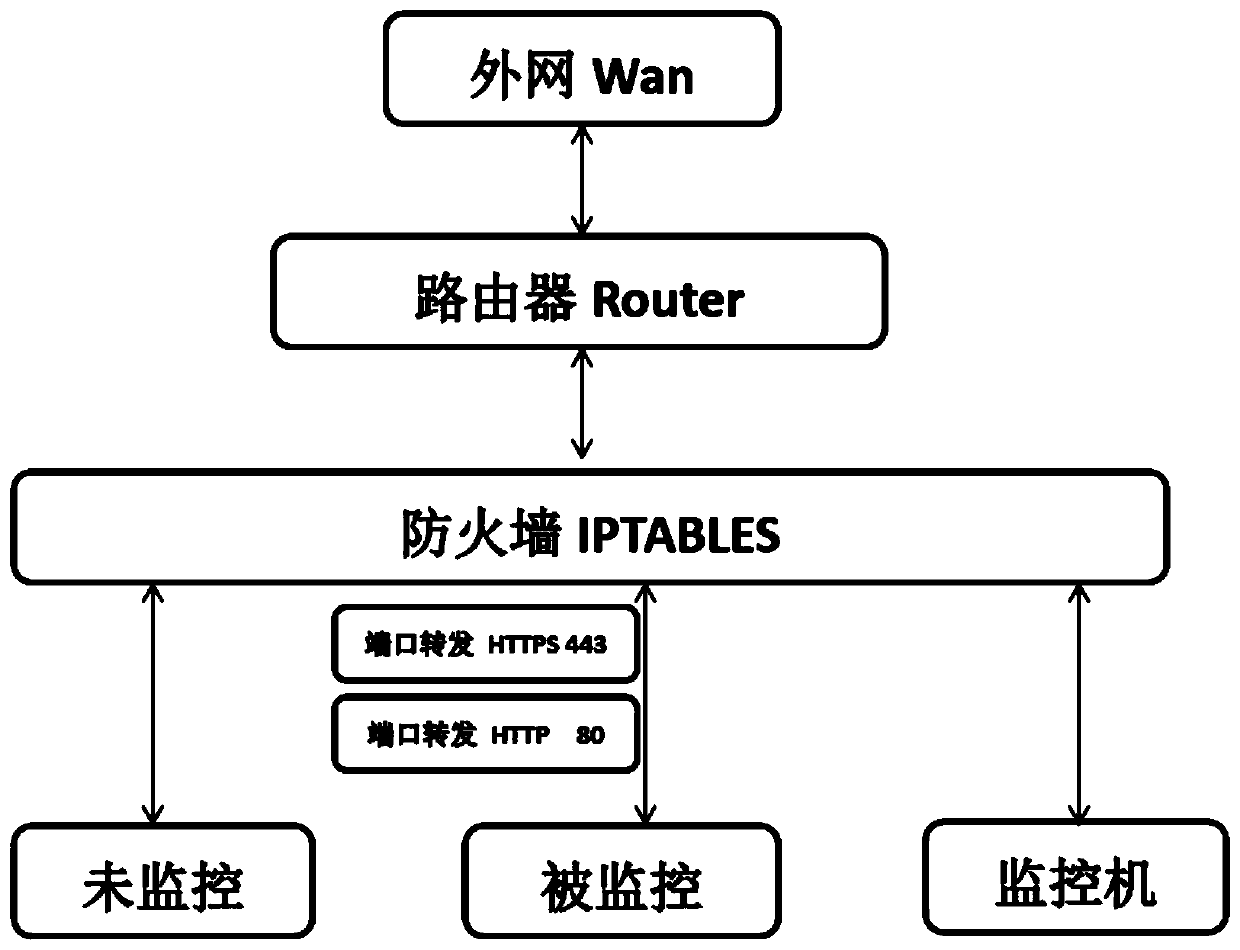
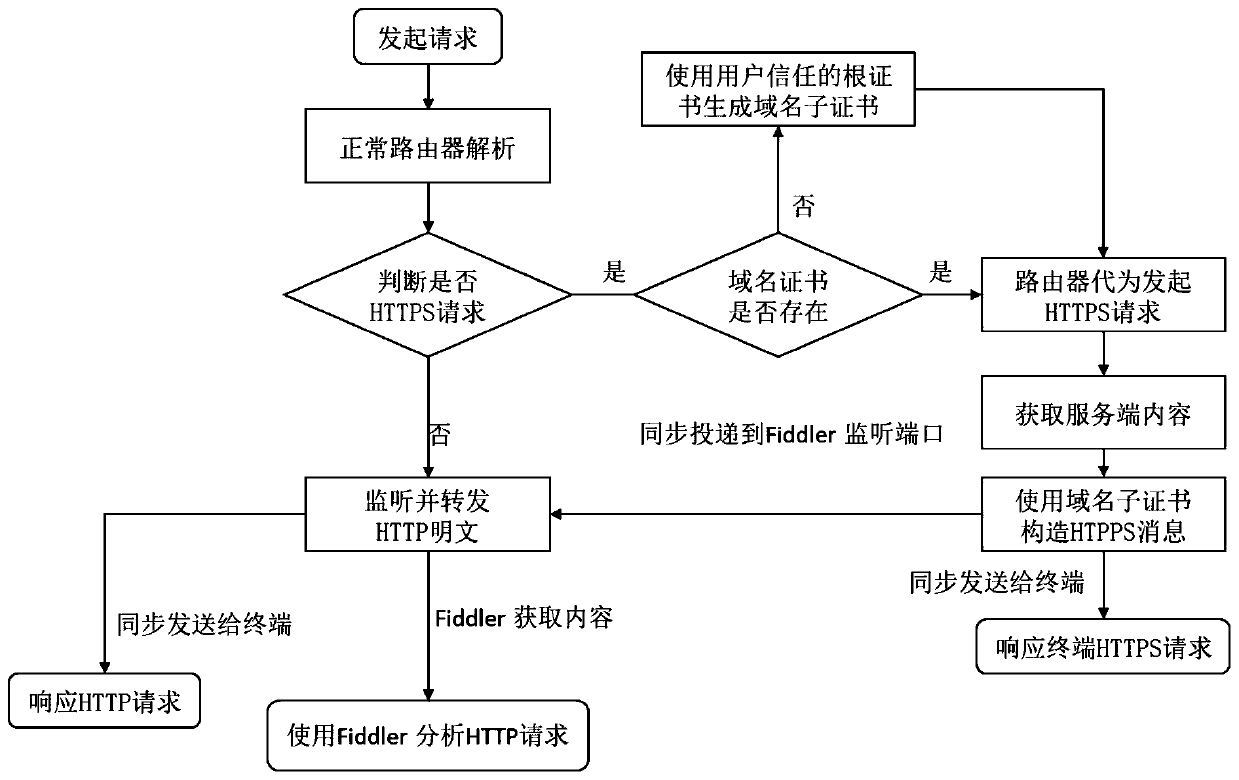
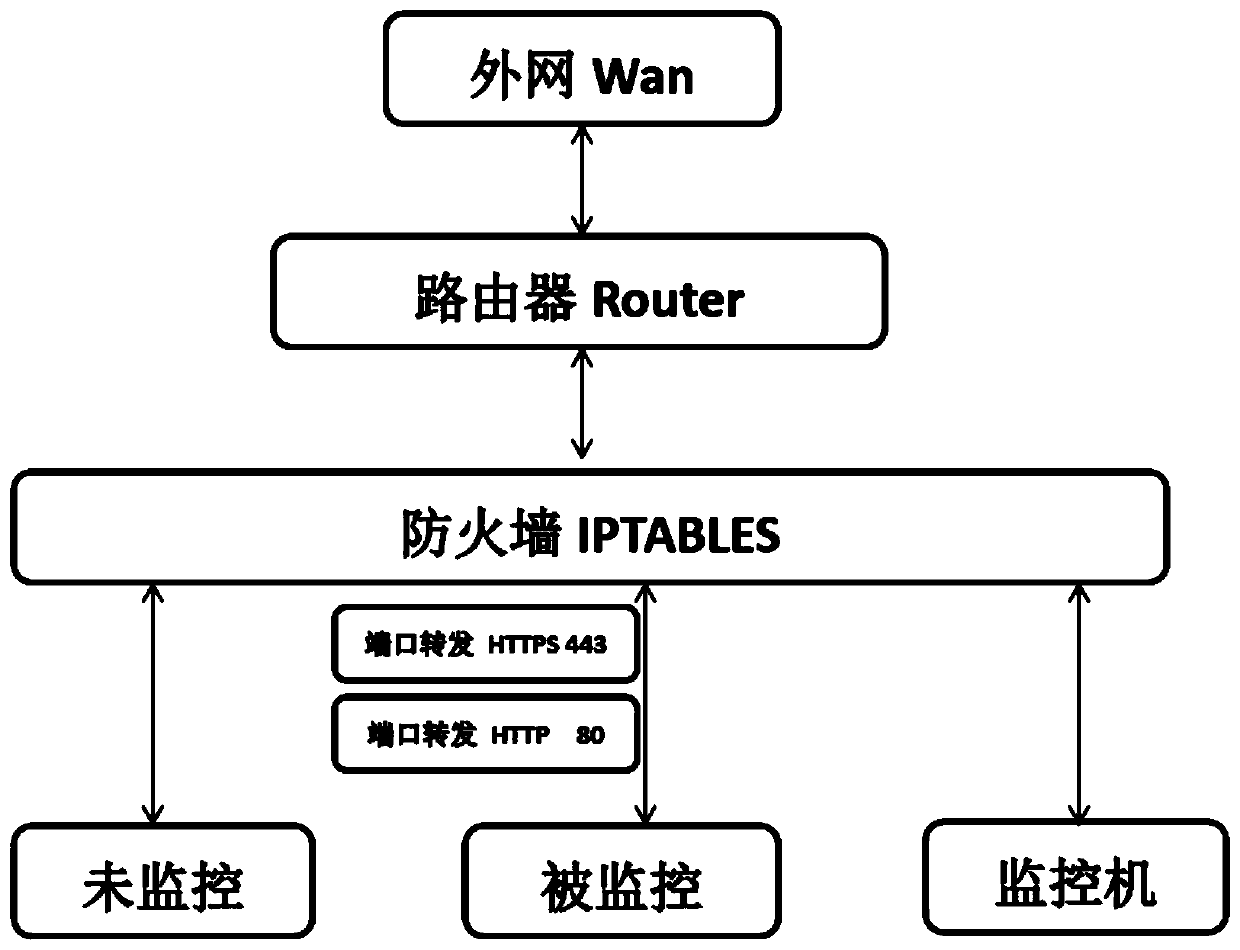
[0022] Such as figure 1 As shown, the authentication authentication method based on the port forwarding hypertext transfer protocol, the specific steps are as follows:
[0023] 101) Preprocessing step: establish a dynamic certificate issuing center, forward the designated IP / Mac address through iptables, and send all 80 / 443 requests of the current domain name to the router;
[0024] 102) HTTPS request judgment step: the router performs analysis and judgment after receiving the request. If the request is an HTTP request, the router will continue to monitor and decrypt the plaintext through the HTTP packet analysis tool, and send it to the end user and the server synchronously, and then enter the response step;
[0025] If the request is an HTTPS request, the certificate is generated by the dynamic certificate issuing center as needed; the rout...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com