Data processing method and system based on power transaction
A data processing system and power transaction technology, applied in the field of information technology security, can solve problems such as leakage of trader account information privacy, and achieve the effect of improving security and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] A data processing method based on power trading, including cloud, the cloud processing method for data includes:
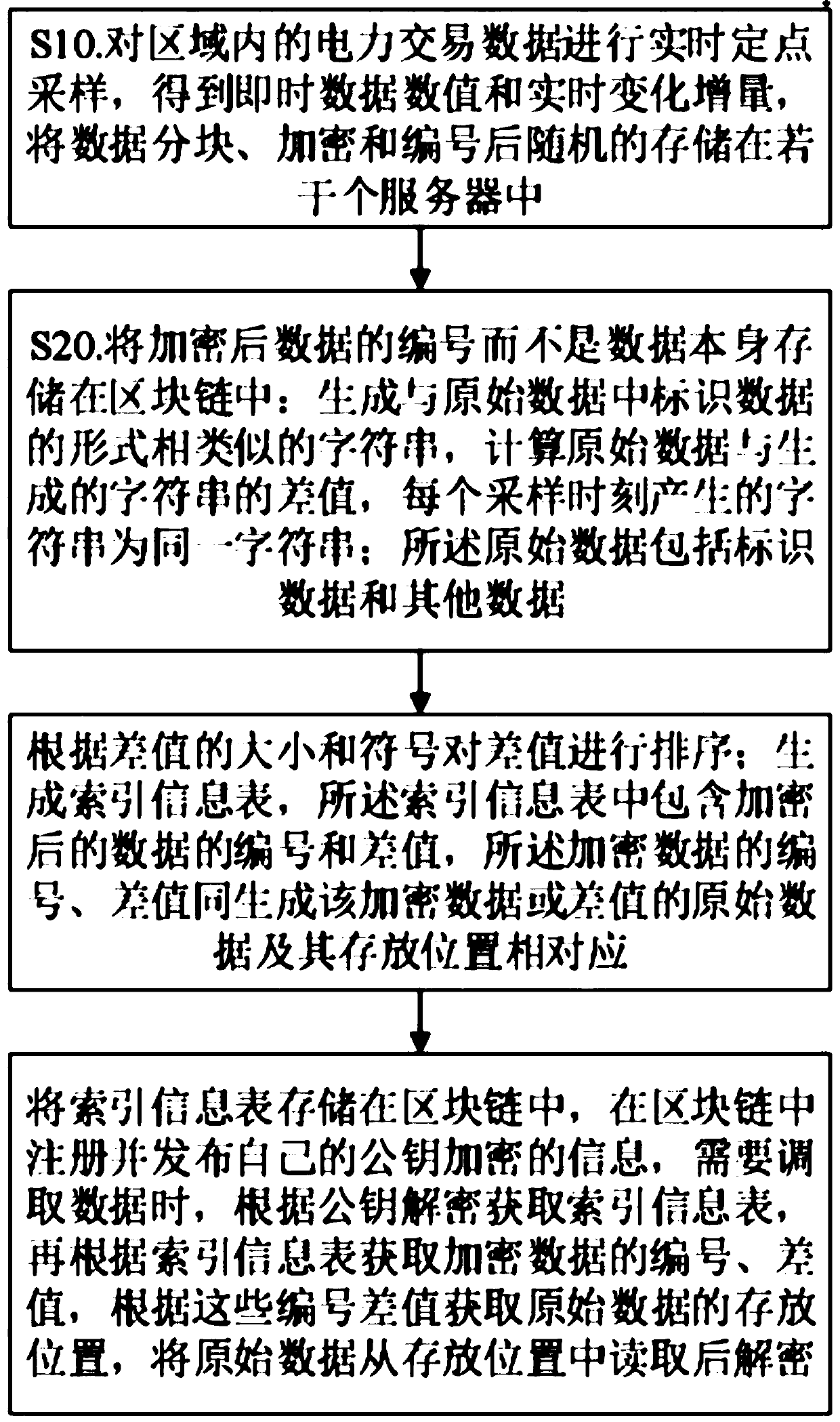
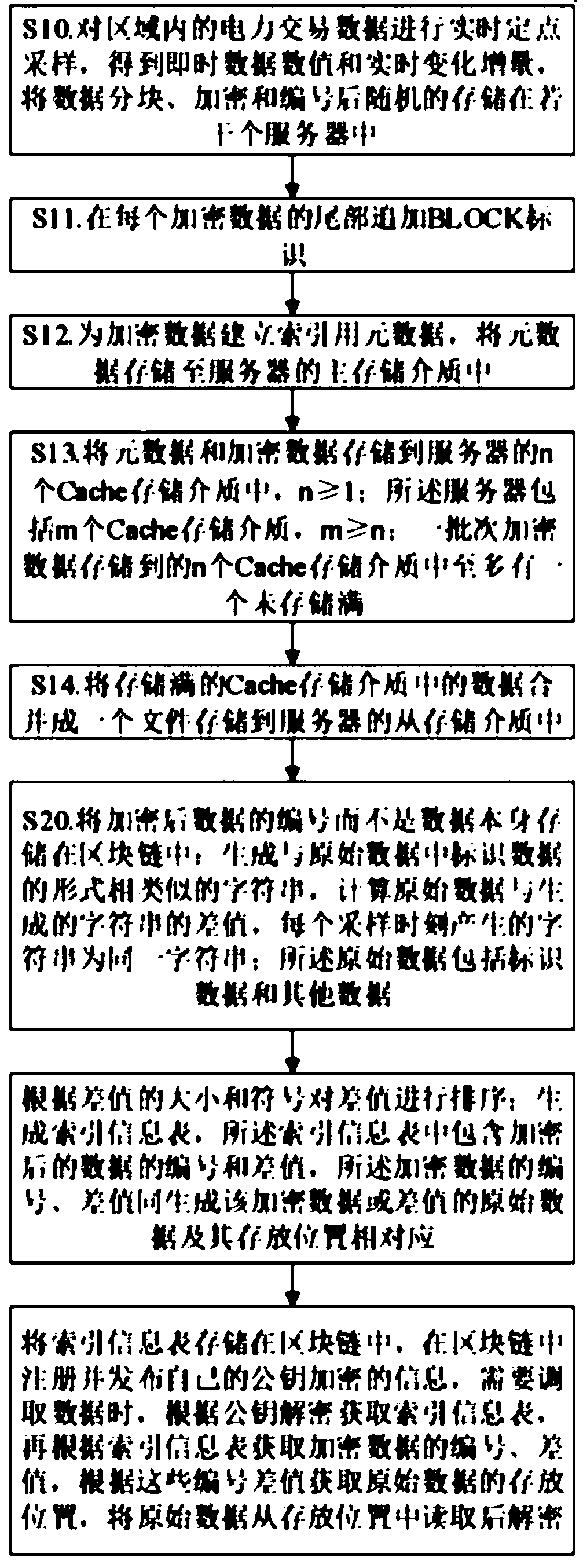
[0045] S10. Carry out real-time fixed-point sampling of the power transaction data in the region to obtain real-time data values and real-time change increments, and randomly store the data in several servers after being divided into blocks, encrypted and numbered; the method of storing the data to the servers is :
[0046] S11. Appending a BLOCK identifier at the end of each encrypted data;
[0047] S12. Create metadata for indexing encrypted data, and store the metadata in the main storage medium of the server;
[0048] S13. Store metadata and encrypted data in n Cache storage media of the server, n≥1; the server includes m Cache storage media, m≥n; n Cache storage media where a batch of encrypted data is stored At least one of them is not full;
[0049]S14. Merge the data in the full Cache storage medium into a file and store it in the slave storage...
Embodiment 2
[0058] A data processing method based on power trading, including cloud, the cloud processing method for data includes:
[0059] S10. Carry out real-time fixed-point sampling of the power transaction data in the region to obtain real-time data values and real-time change increments, and randomly store the data in several servers after being divided into blocks, encrypted and numbered; the method of storing the data to the servers is :
[0060] S11. Appending a BLOCK identifier at the end of each encrypted data;
[0061] S12. Create metadata for indexing encrypted data, and store the metadata in the main storage medium of the server;
[0062] S13. Store metadata and encrypted data in n Cache storage media of the server, n≥1; the server includes m Cache storage media, m≥n; n Cache storage media where a batch of encrypted data is stored At least one of them is not full;
[0063] S14. Merge the data in the full Cache storage medium into a file and store it in the slave storag...
Embodiment 3
[0076] A data processing system based on power trading, including a cloud, where the cloud includes a sampling module, a data processing module, and an index generation module;
[0077] The sampling module performs real-time fixed-point sampling of the power transaction data in the area to obtain real-time data values and real-time change increments, and the data processing module randomly stores the data in several servers after being divided into blocks, encrypted and numbered;
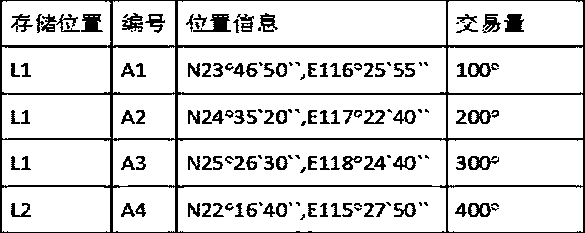
[0078] The index generation module stores the number of the encrypted data rather than the data itself in the block chain; the storage method is:
[0079] Generate a string similar to the form of the identification data in the original data, calculate the difference between the original data and the generated string, and the string generated at each sampling moment is the same string; the original data includes identification data and other data ;
[0080] The difference is sorted according to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com