A Dynamic Allocation Request Verification Method
A verification method and dynamic allocation technology, applied in the fields of data encryption, storage and privacy protection, security and privacy protection, can solve the problems of low security performance, singleness, and easy capture of request packets, so as to save resources and increase security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
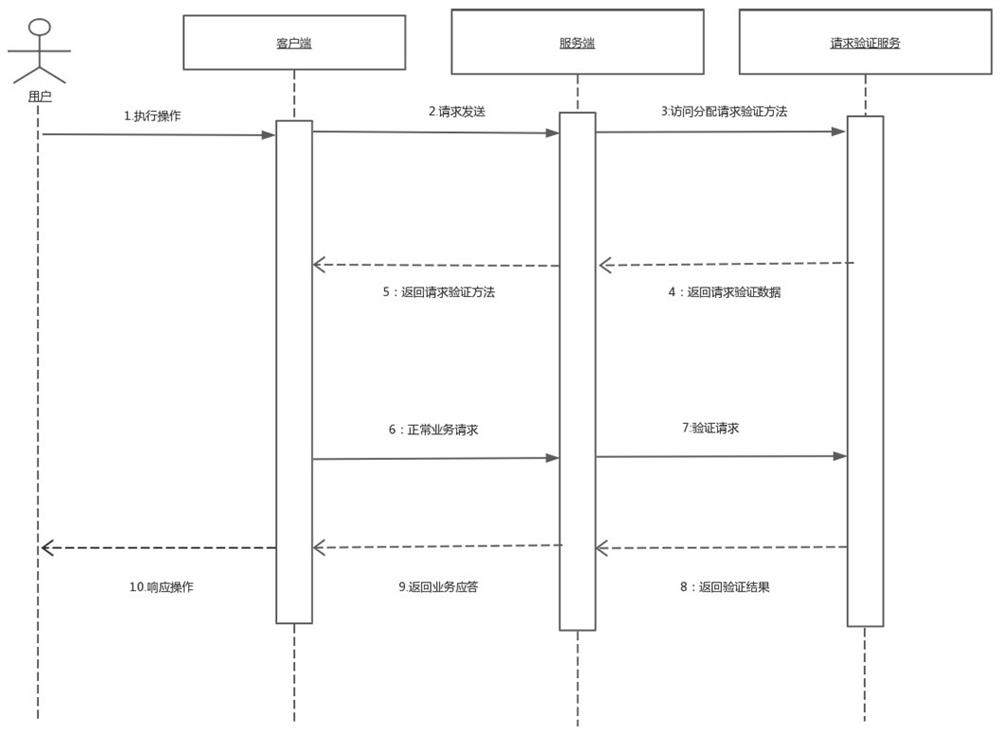
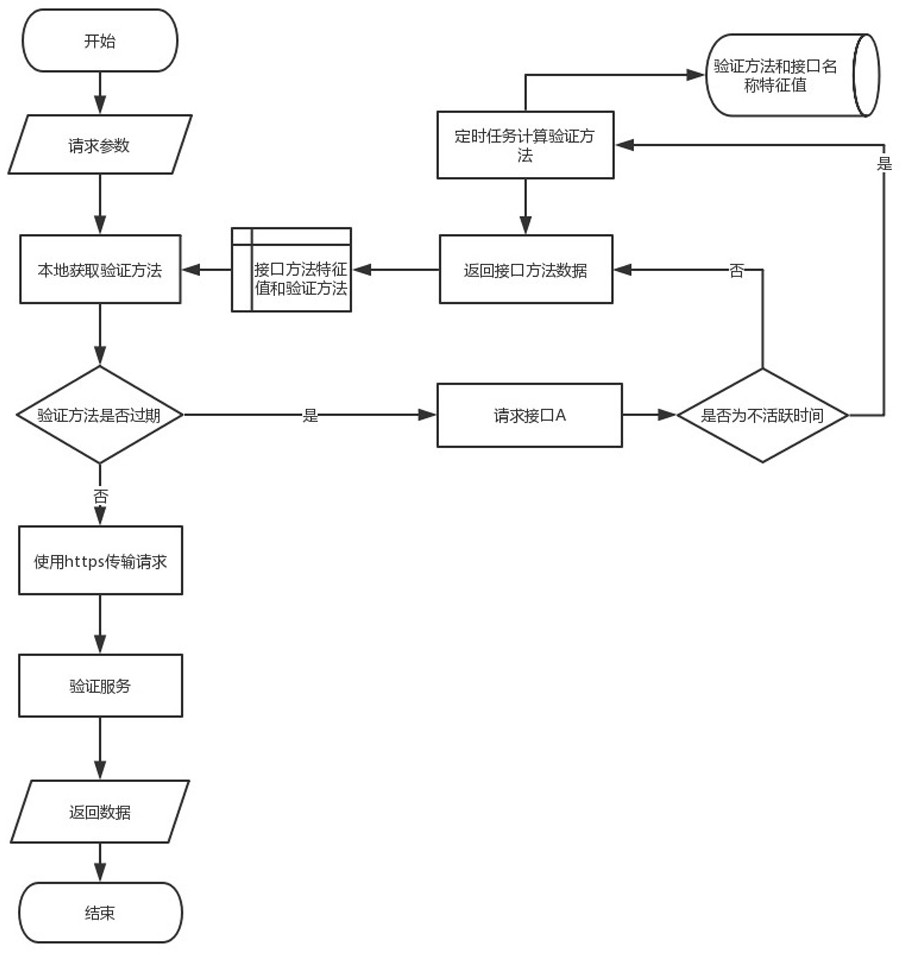
[0021] Referring to the accompanying drawings, a dynamic allocation request verification method is described in detail in this embodiment in conjunction with a mobile terminal social software of a certain offline social network, including the following steps:
[0022] Step 1: The business server of the social software performs scheduled tasks when the system activity is the lowest every day. According to the number of visits to all interfaces of the previous day, the type of interface, and the data fields involved in the interface stored in the database of the business server. The quantification parameter of importance, according to the weight corresponding to the three interface types set in the background, calculate the weight value according to the weight value calculation formula. In this project, the parameter of the interface access times is 0.1, the parameter of the interface type is 100, and the The parameter of sensitivity is 200, the value of the data acquisition inte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com