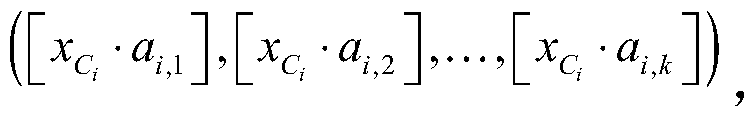Facility site selection method and system based on encrypted position data
A facility and data technology, applied in data processing applications, digital data protection, electronic digital data processing, etc., can solve problems such as the inability of site selection to meet requirements, enterprises have no right to obtain them, etc., to protect privacy, improve accuracy, guarantee The effect of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
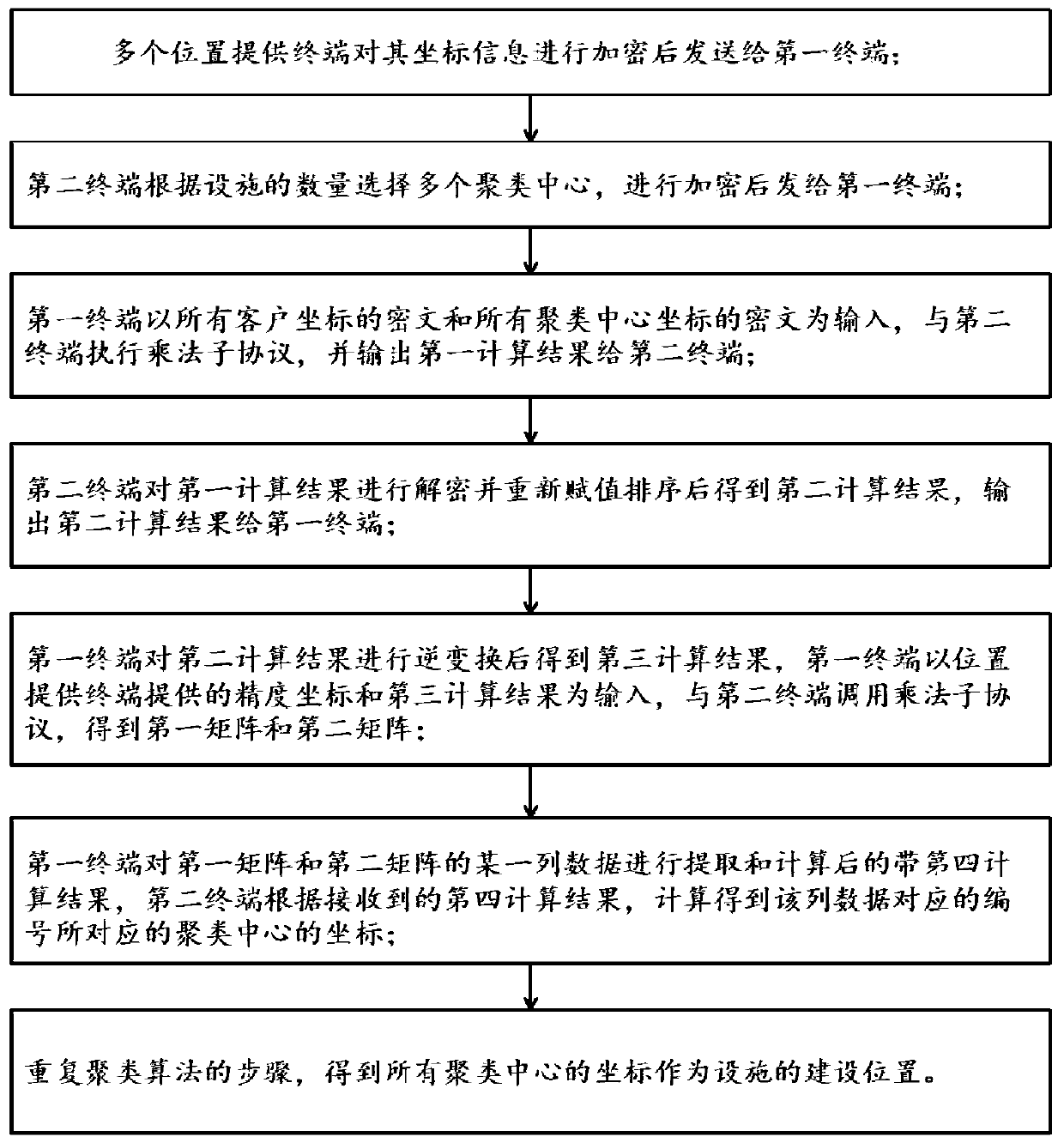
[0054] like figure 1As shown, Embodiment 1 of the present disclosure provides a location selection method for facilities based on encrypted location data. The Paillier homomorphic encryption scheme is used to encrypt the location data, and any encryption scheme with additive homomorphic properties can also be used instead.
[0055] The Paillier homomorphic encryption scheme is an additive homomorphic encryption scheme, which only supports the addition operation of ciphertext. However, in clustering calculations, multiplication and comparison operations are required, which are not supported by the Paillier homomorphic encryption scheme. This embodiment solves the above problems by introducing an independent auxiliary computing party and designing a corresponding secure computing protocol.
[0056] In this embodiment, the entities involved include: several location providers (clients), a cluster computing party (enterprises with equipment site selection requirements), and an au...
Embodiment 2
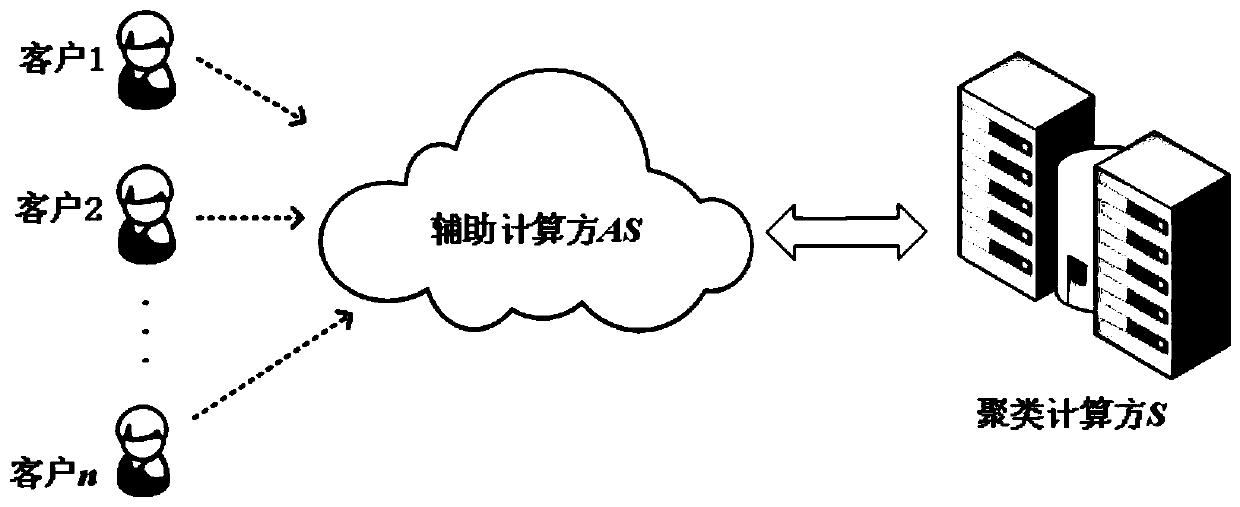
[0112] like figure 2 As shown, Embodiment 2 of the present disclosure provides a facility location selection system based on encrypted location data, multiple customers (location providing terminals), auxiliary computing party AS (first terminal) and cluster computing side S (second terminal ), the location providing terminal communicates with the first terminal, the first terminal communicates with the second terminal, and the location providing terminal, the first terminal and the second terminal execute the encryption-based location data described in Embodiment 1 of the present disclosure. Facility site selection method for facility site selection.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com