HTTP vulnerability scanning host confirmation method and device, equipment and medium
A vulnerability scanning and host technology, applied in the field of system management, can solve problems such as difficulty in accurate identification, low efficiency, and waste of human resources, and achieve the effect of improving the efficiency of confirmation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
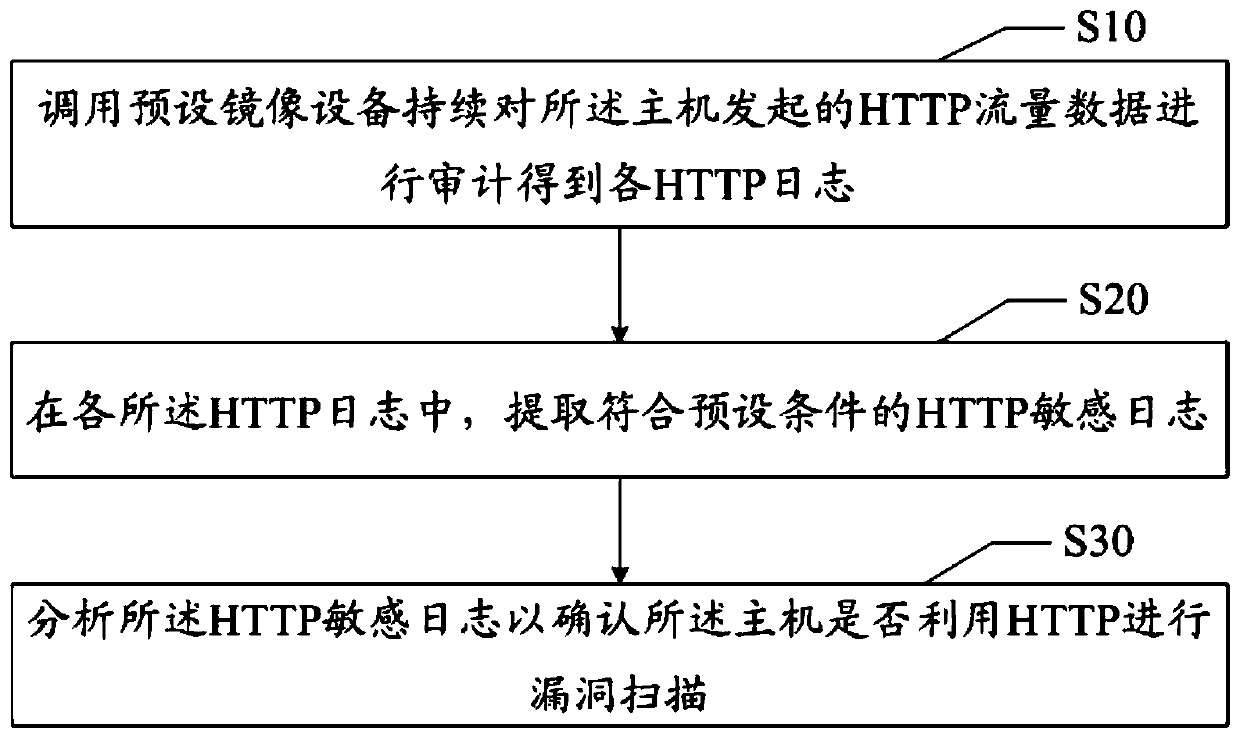
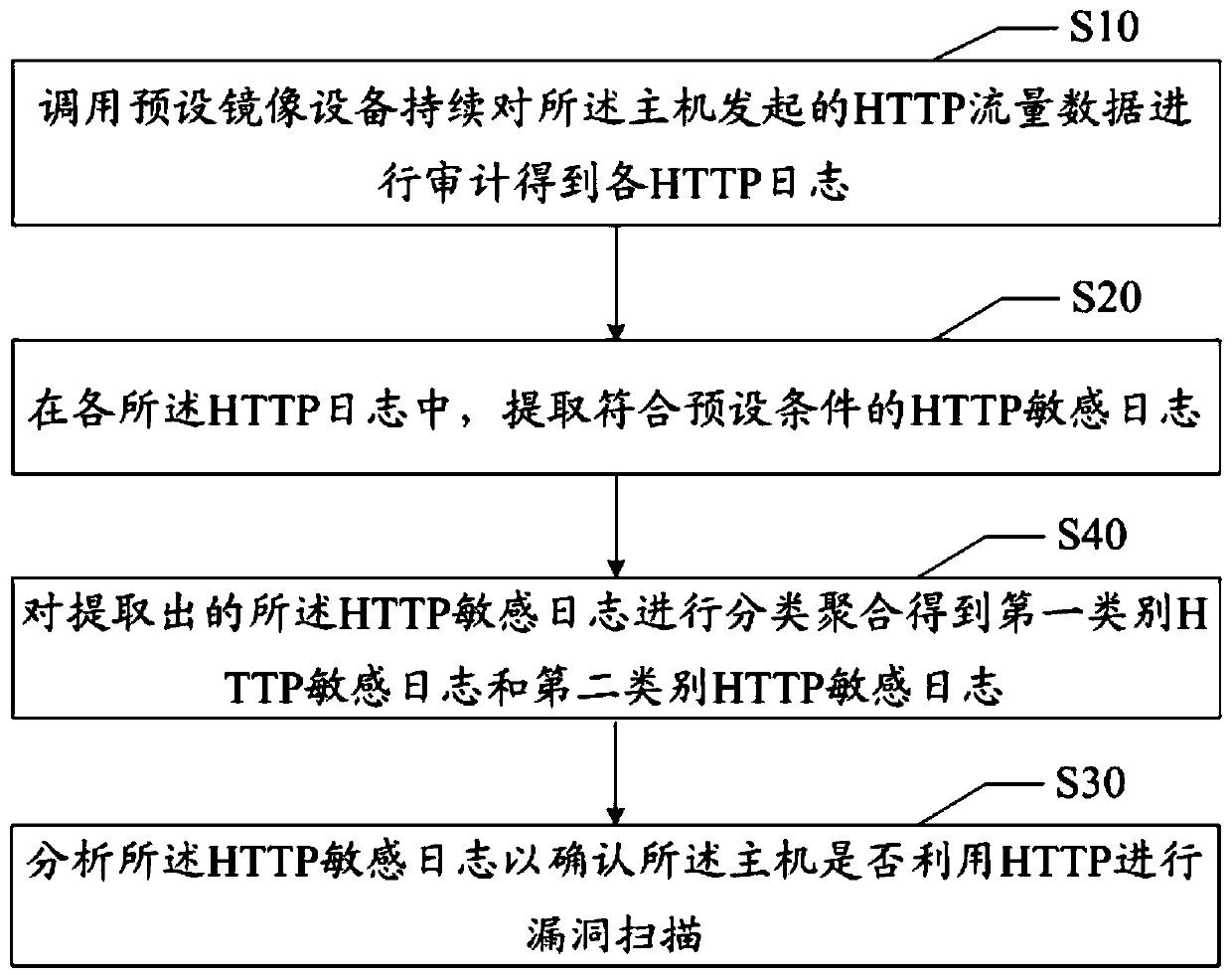
[0055] The main solution of the embodiment of the present invention is: calling the preset mirroring device to continuously audit the HTTP traffic data initiated by the host to obtain each HTTP log; in each of the HTTP logs, extracting HTTP sensitive logs that meet the preset conditions; Analyzing the HTTP sensitive log to confirm whether the host uses HTTP for vulnerability scanning.
[0056] At present, only known scanning tools can be identified through scanning dictionary matching, which requires a lot of manpower to analyze and extract the scanning dictionaries used by each tool, and the generalization ability is poor. In addition, matching based on sensitive paths can only identify known vulnerabilities. or backdoor-related access paths, and even normal access may trigger sensitive paths, which is very prone to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com