Intelligent learning type self-response industrial internet honeypot induction method and system
An industrial Internet and intelligent learning technology, which is applied in the field of intelligent learning self-response industrial Internet honeypot induction, can solve the problems that there is no clear and public self-learning method, and the attacker cannot be captured, so as to achieve real-time update and good simulation effect Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] like figure 1 As shown, an intelligent learning self-response industrial Internet honeypot induction method,
[0041] S01. Sample data processing
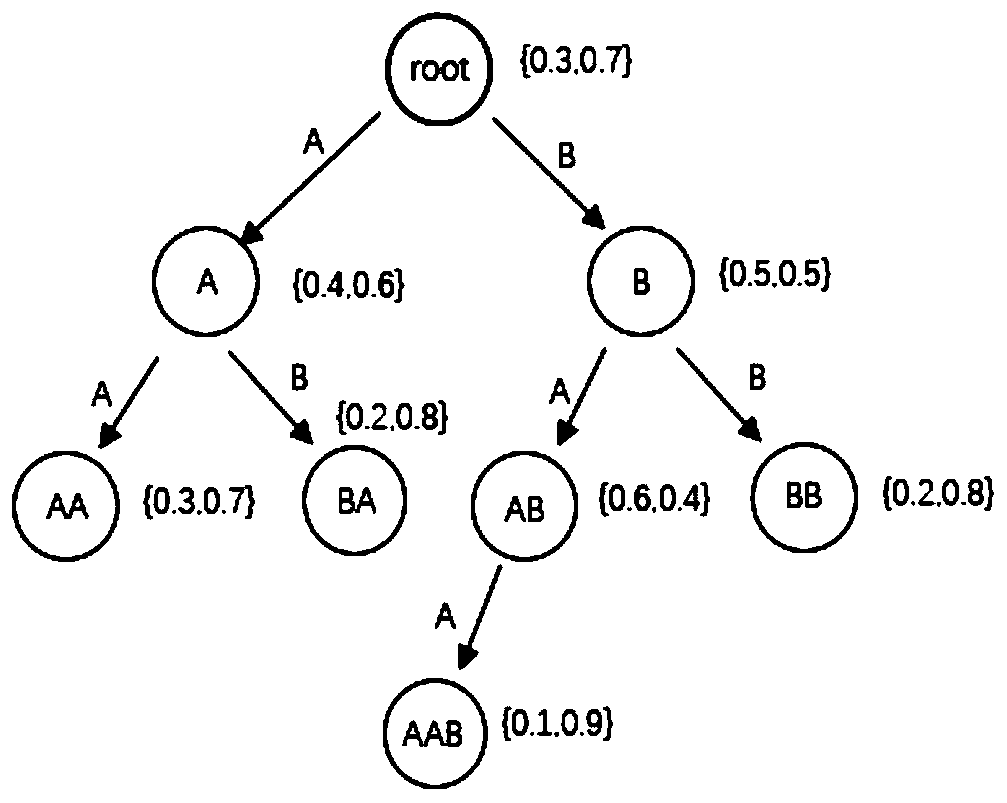
[0042]The traffic engine unit regularly collects the request sequence of the attacker in the honeypot for a period of time (such as 3 months), and the business request sequence of the industrial environment under normal circumstances for a period of time, and then encodes different request commands through the encoding unit, such as Use the character "A" to represent the "open" command, etc., so as to generate the code sequence corresponding to the request. According to the request sequence of these attackers and the business request sequence in the industrial environment, select to detect the devices in the industrial Internet one by one under supervision, and record the devices that respond to these requests and the response content to the "Original Response" table. The response behavior in the "Original Response" table ...
Embodiment 2
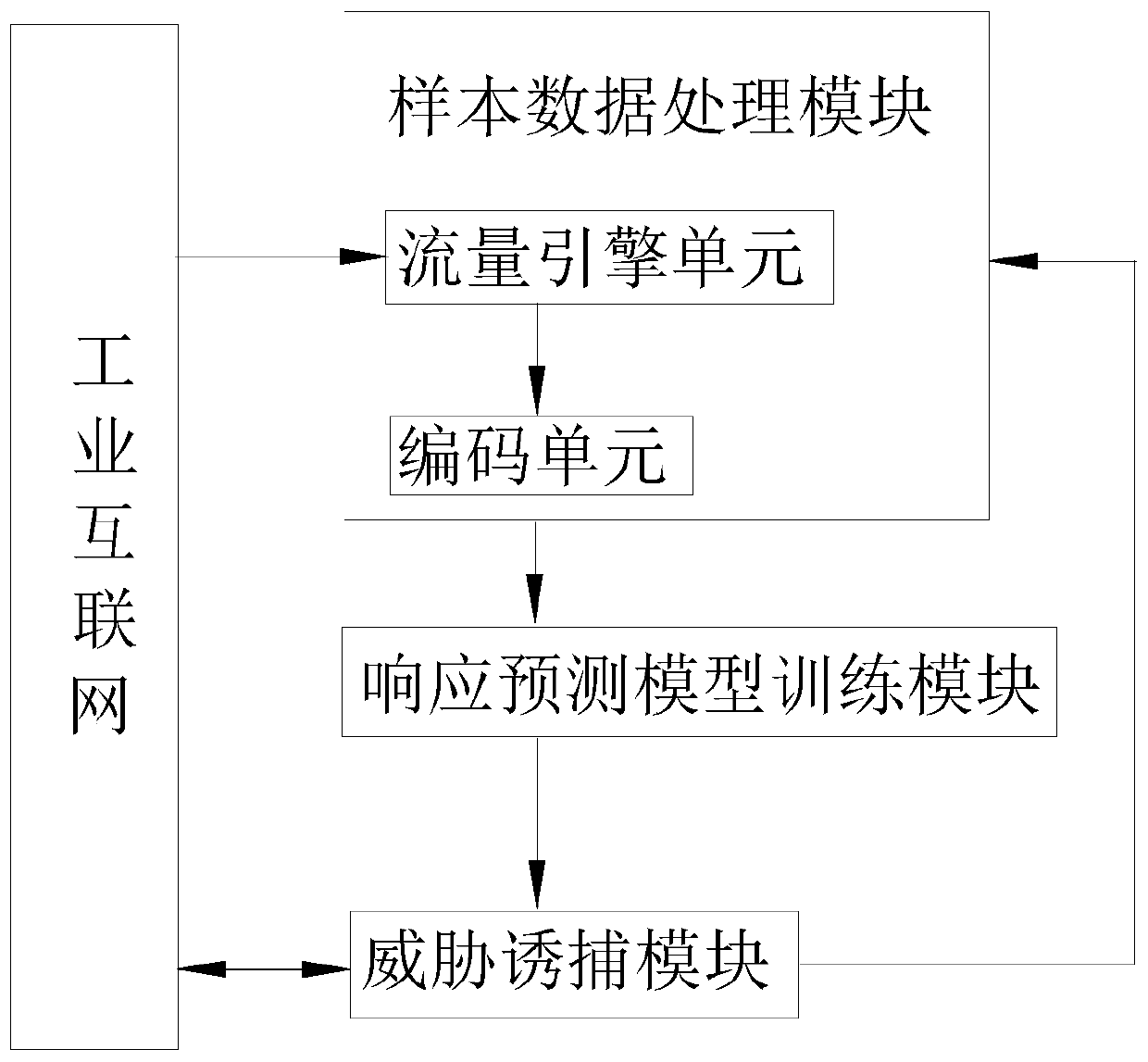
[0055] Corresponding to Embodiment 1, this embodiment provides an intelligent learning type self-response industrial Internet honeypot induction system, including
[0056] Sample data processing module
[0057] The traffic engine unit regularly collects the request sequence of the attacker in the honeypot for a period of time (such as 3 months), and the business request sequence of the industrial environment under normal circumstances within a period of time, and encodes different request commands such as using the character "A "Represents the "open" command, etc., so as to generate the encoding sequence corresponding to the request. According to the request sequence of these attackers and the business request sequence in the industrial environment, select to detect the devices in the industrial Internet one by one under supervision, and record the devices that respond to these requests and the response content to the "Original Response" table. The response behavior in the "O...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap