Key distribution method and system based on multi-key combined quantum key relaying
A quantum key and key distribution technology, applied in the field of key distribution method and system based on multi-key combination quantum key relay, can solve the problems of limited security, high cost, insufficient anti-attack ability and the like
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
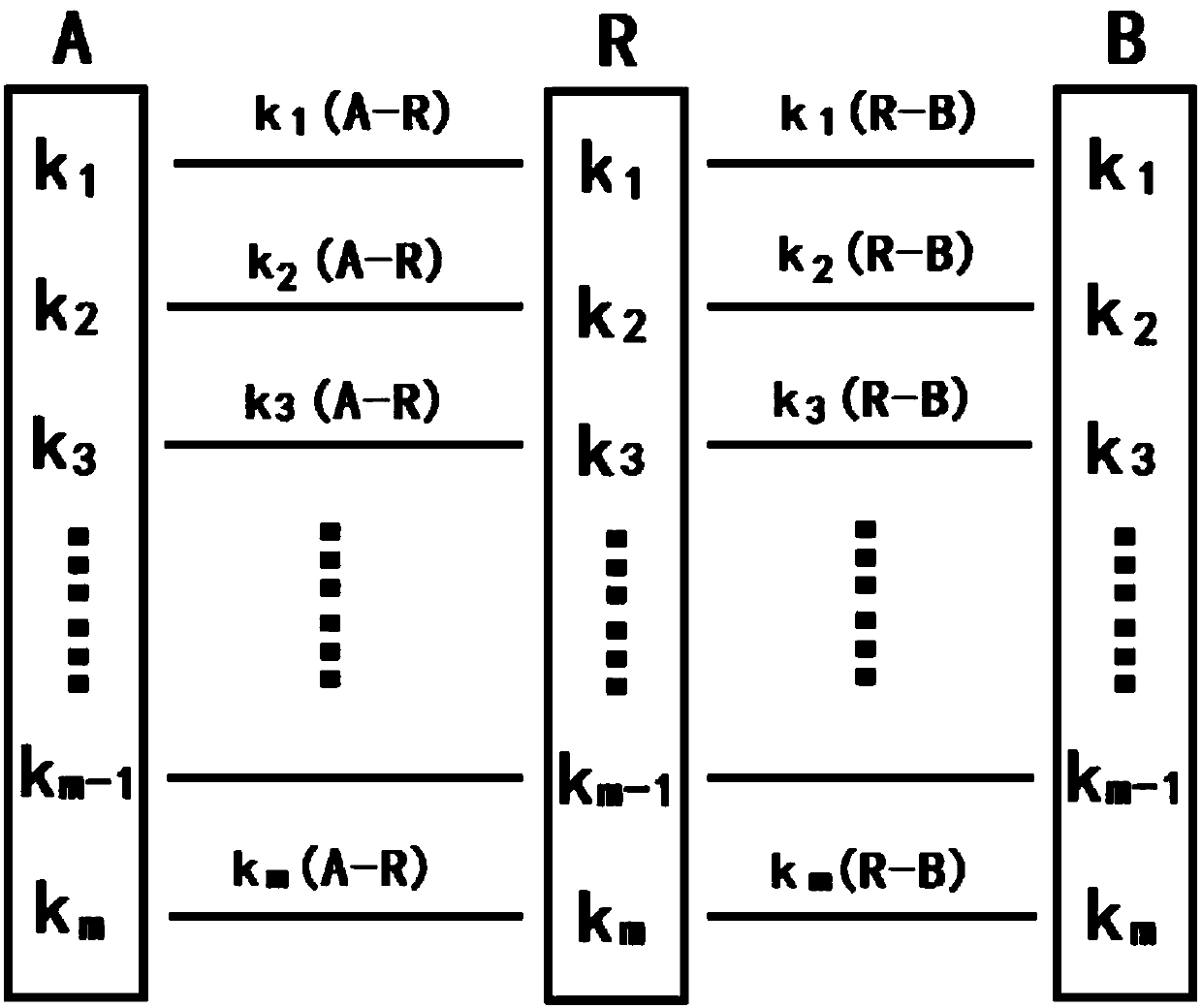
[0066] figure 1 It is a flow chart of a key distribution method based on multi-key combined quantum key relay provided in Embodiment 1 of the present invention. In this embodiment, there is a layer of intermediate keys, such as figure 1 shown, including the following steps:
[0067] S1: The quantum terminal node A as the source node and the quantum terminal node B as the destination node exchange the quantum key k through the relay node R 1 sharing of
[0068] In this embodiment, the step S1 specifically includes the following steps:
[0069] S11: The quantum terminal node A as the source node transfers the quantum key k 1 Encrypt with the shared key between quantum terminal node A and relay node R to get k 1 (A-R), and sent to the relay node R;
[0070] S12: The relay node R receives the encrypted key k sent by the quantum terminal node A as the source node 1 (A-R), decrypt it to get k 1 , the quantum key k 1 Encrypt with the shared key between the relay node R and th...
Embodiment 2
[0107] Embodiment 1 The calculation of the intermediate key and the final key requires the quantum terminal node A as the source node and the quantum terminal node B as the destination node to respectively store the shared quantum key k 1 to k m-1 and the calculated intermediate key k 1 ' to k m-1 ', in order to save the storage space of the quantum terminal, the present invention makes a further improvement on the basis of Embodiment 1.
[0108] On the basis of embodiment 1, it is modified as follows:
[0109] 1. Intermediate key k m 'The calculation method is changed to k m '=H 1 (k m +k m-1 ');
[0110] 2. Final key k m "The calculation method is changed to k m "=H 2 (k m '+k m-1 ").
[0111] In this embodiment, if only from the calculation point of view, in order to calculate the new intermediate key k m ', the quantum terminal only needs to store k m-1 ' can be shared with the new k m Calculate the result together without necessarily storing the previousl...
Embodiment 3
[0146] Make further improvement on the basis of embodiment 1 or embodiment 2:
[0147] In the formula for calculating the intermediate key or the final key, the combination of two or more keys can not only be realized by splicing, but also can be changed to other combinations, such as XOR operation, misplaced X Or operation, dislocation splicing operation, etc.
[0148] It should be noted that when the combination is a linear operation, the hash function should preferably choose a hash function with nonlinear properties.
[0149] For example, in this embodiment, step S8 in Embodiment 1 is improved as follows:
[0150] S8: According to step S2 or S4, the quantum terminal node A as the source node and the quantum terminal node B as the destination node each share a quantum key k m , the quantum terminal node A as the source node calculates the intermediate key k sequentially m ' and the final key k m ";
[0151] The intermediate key k m 'According to the shared quantum key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com