Cross-chain implementation method, device and equipment for associated transaction requests, and medium
An implementation method and transaction technology, applied in the field of blockchain technology, can solve the problem of not providing a decentralized operation plan, and achieve the effect of improving convenience and preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
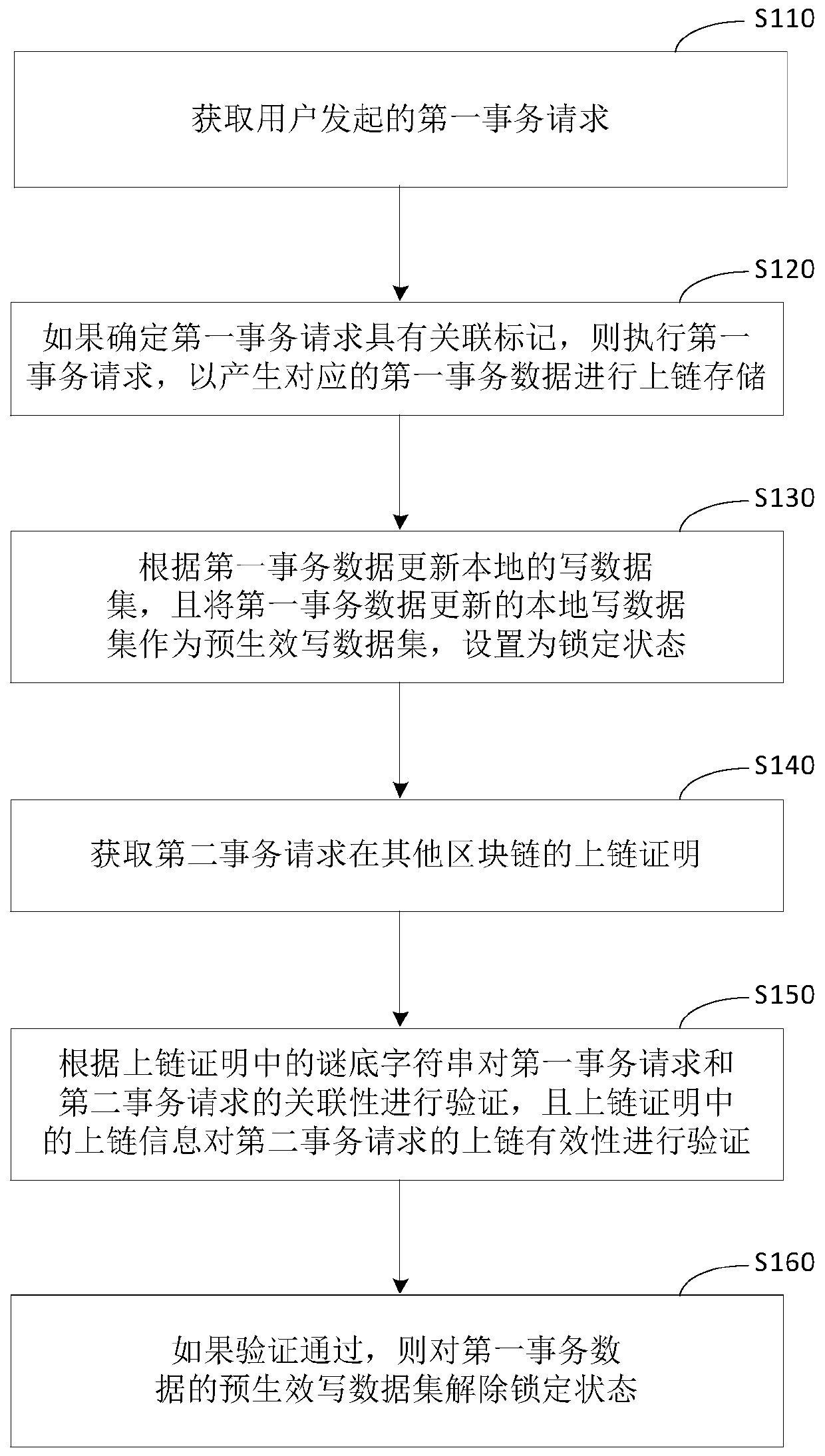
[0080] figure 1 It is a flow chart of the cross-chain implementation method for associated transaction requests provided by Embodiment 1 of this application. This embodiment is applicable to the cross-chain operation situation in which associated transaction requests are respectively initiated in multiple blockchains to jointly realize a certain requirement. This embodiment can be executed by the cross-chain implementation device of the associated transaction request configured in the blockchain node, the device can be realized by software and / or hardware, and integrated in the electronic device as the blockchain node.
[0081] Such as figure 1 As shown, the method includes:
[0082] S110. Acquire a first transaction request initiated by a user.
[0083] Wherein, the first transaction request is initiated by the user in the current blockchain network based on a certain business requirement. It can be in the form of UTXO (unspent transaction output) or a transaction request...
Embodiment 2
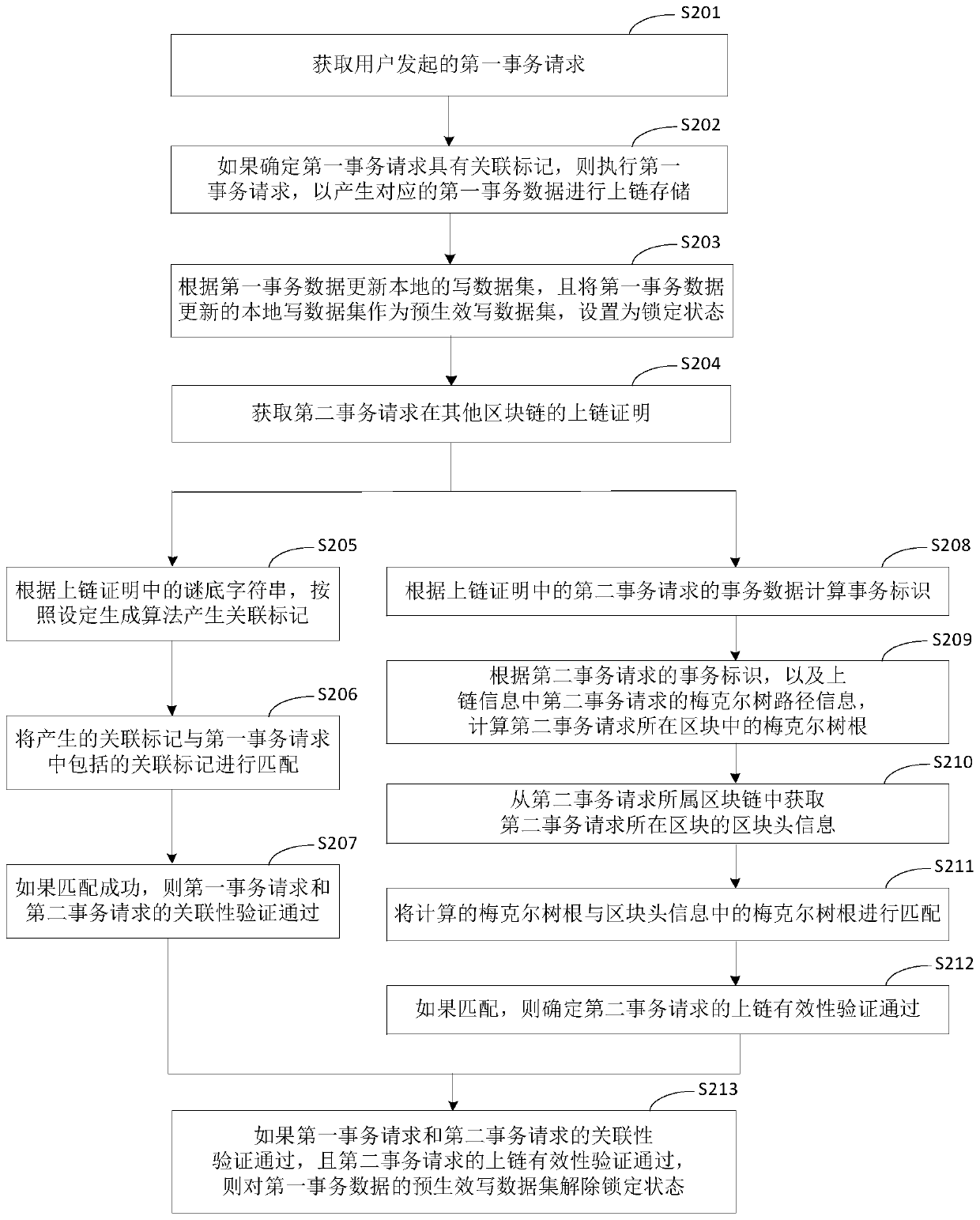
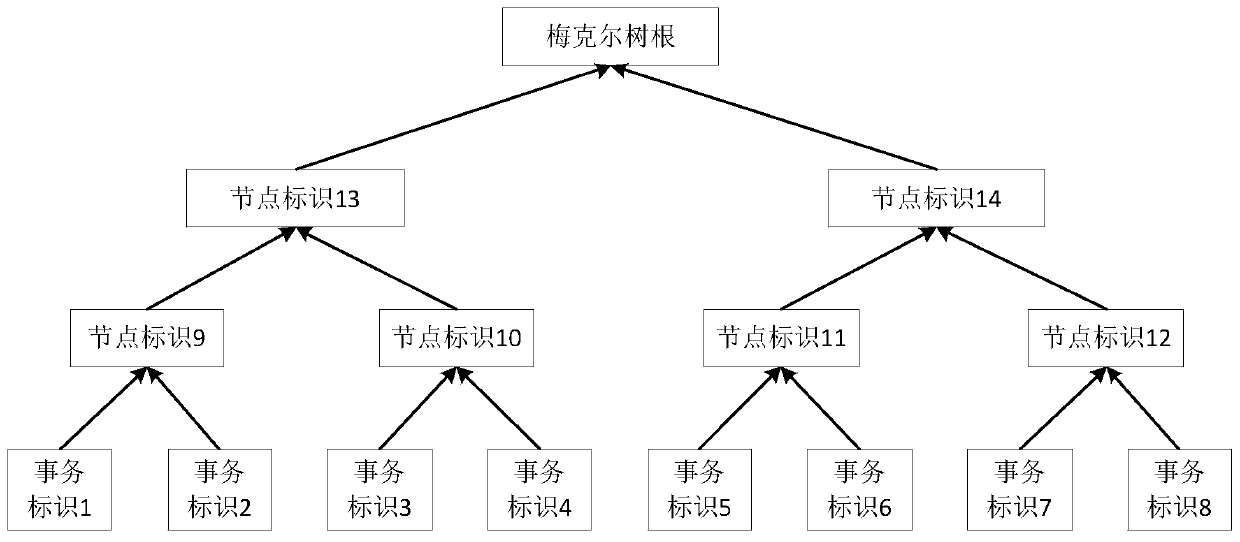
[0112] Figure 2A A flow chart of the cross-chain implementation method for associated transaction requests provided in Embodiment 2 of this application; Figure 2B It is a schematic diagram of the calculation principle of the Merkle tree root provided in the second embodiment of the present application. This embodiment is further optimized on the basis of the above-mentioned embodiments, and provides that the correlation between the first transaction request and the second transaction request is verified according to the answer string in the chain-up certificate, and The specific situation of verifying the validity of the chain-up of the second transaction request according to the chain-up information in the chain-up certificate is introduced. Such as Figure 2A-2B As shown, the method may specifically include:
[0113] S201. Obtain a first transaction request initiated by a user.
[0114] S202. If it is determined that the first transaction request has an associated flag...
Embodiment 3
[0139] Figure 3A-3B It is a flow chart of the cross-chain implementation method of the associated transaction request provided by Embodiment 3 of this application. This embodiment is further optimized on the basis of the above-mentioned embodiments, and introduces two situations in which the pre-validation data set becomes invalid after the pre-validation write data set is set to a locked state.
[0140] Optionally, as shown in 3A, it is determined whether the pre-validation data set is invalid according to the set expiration threshold. This situation may specifically include:
[0141] S301. Obtain a first transaction request initiated by a user.
[0142] S302. If it is determined that the first transaction request has an associated flag, execute the first transaction request to generate corresponding first transaction data for uplink storage.
[0143] Wherein, the association mark is generated based on the answer string set by the user.
[0144] S303. Update the local wr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com