Covert communication method based on constructive adversarial sample
A technology against samples and covert communication, which is applied in the field of secret data transmission to achieve the effect of improving concealment and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0035] First, suppose the sender and receiver want to transmit a secret message b i ∈{0,1}, i=1,2,...,N.
[0036] Such as figure 1 with figure 2 As shown, a covert communication method based on constructive adversarial examples, the specific operation steps are as follows:
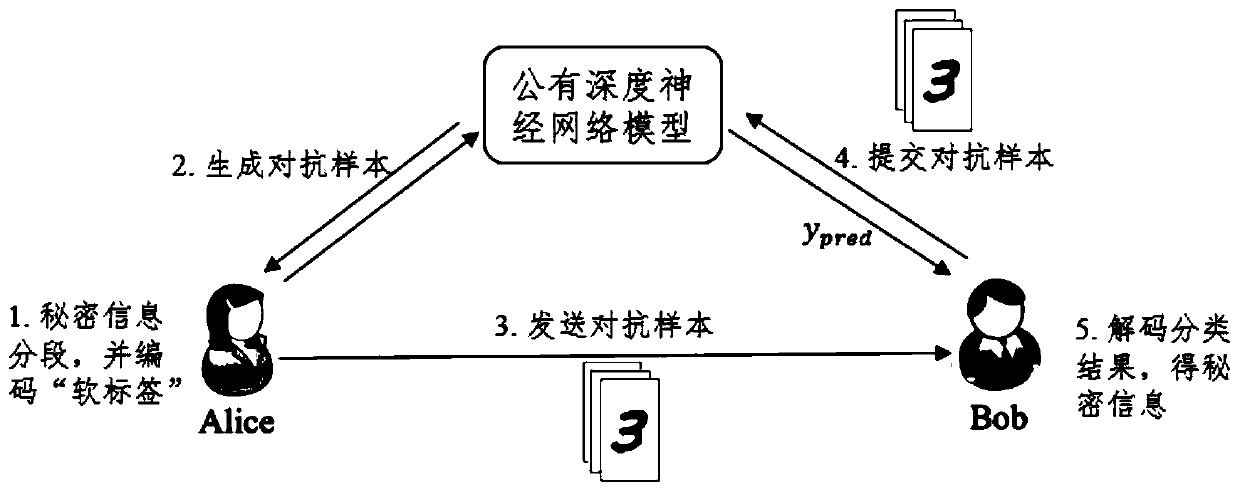
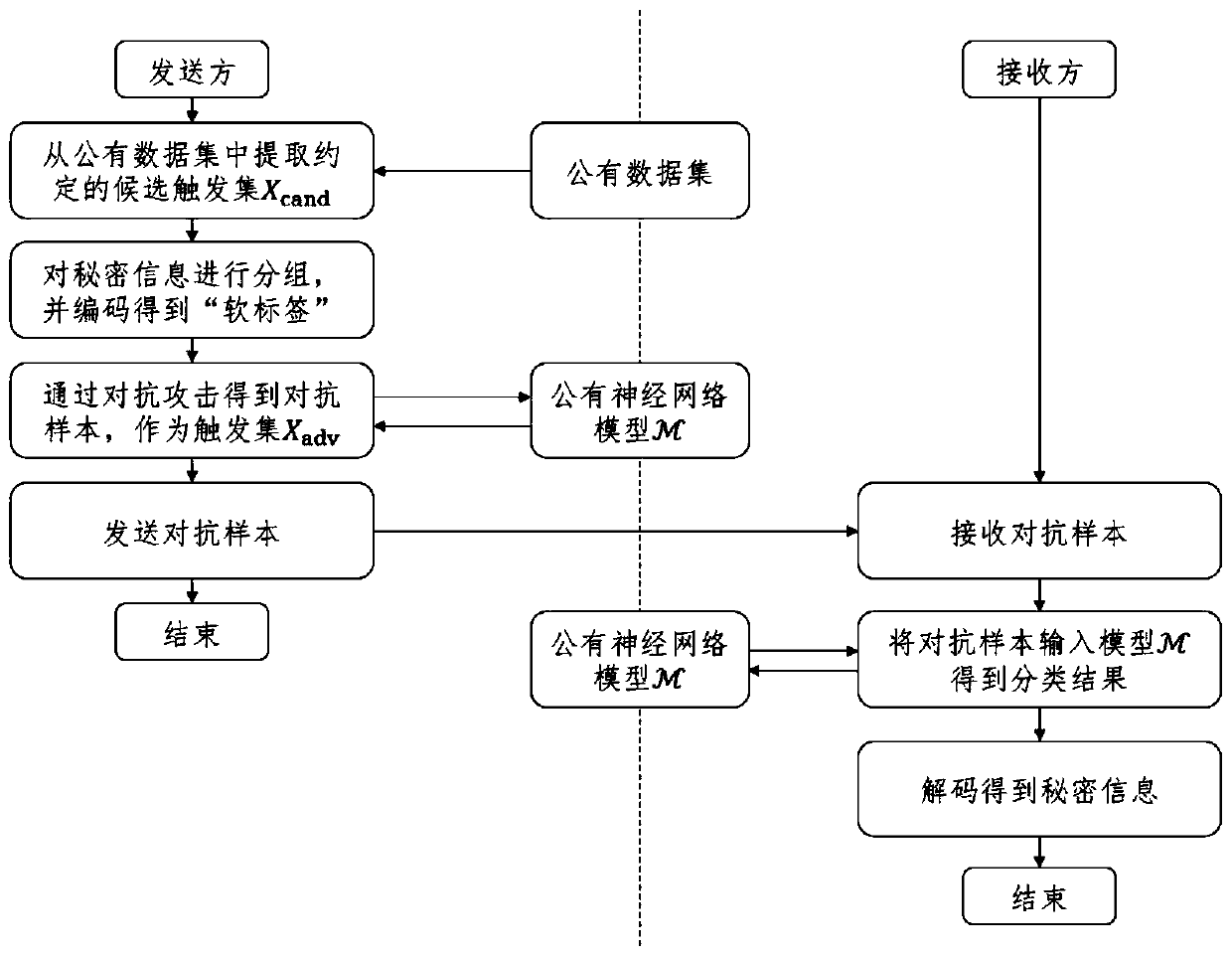
[0037] Step 1: The sender and the receiver agree in advance to choose a deep neural network As a secret information extraction tool, and from the model Randomly select a set of images from the public dataset of X as the candidate trigger set X cand .
[0038] Step 2: The sender sends the secret information b i Grouping, with k bits as a group, and from the candidate trigger set X cand Assign a sample image x to each set of secret information.
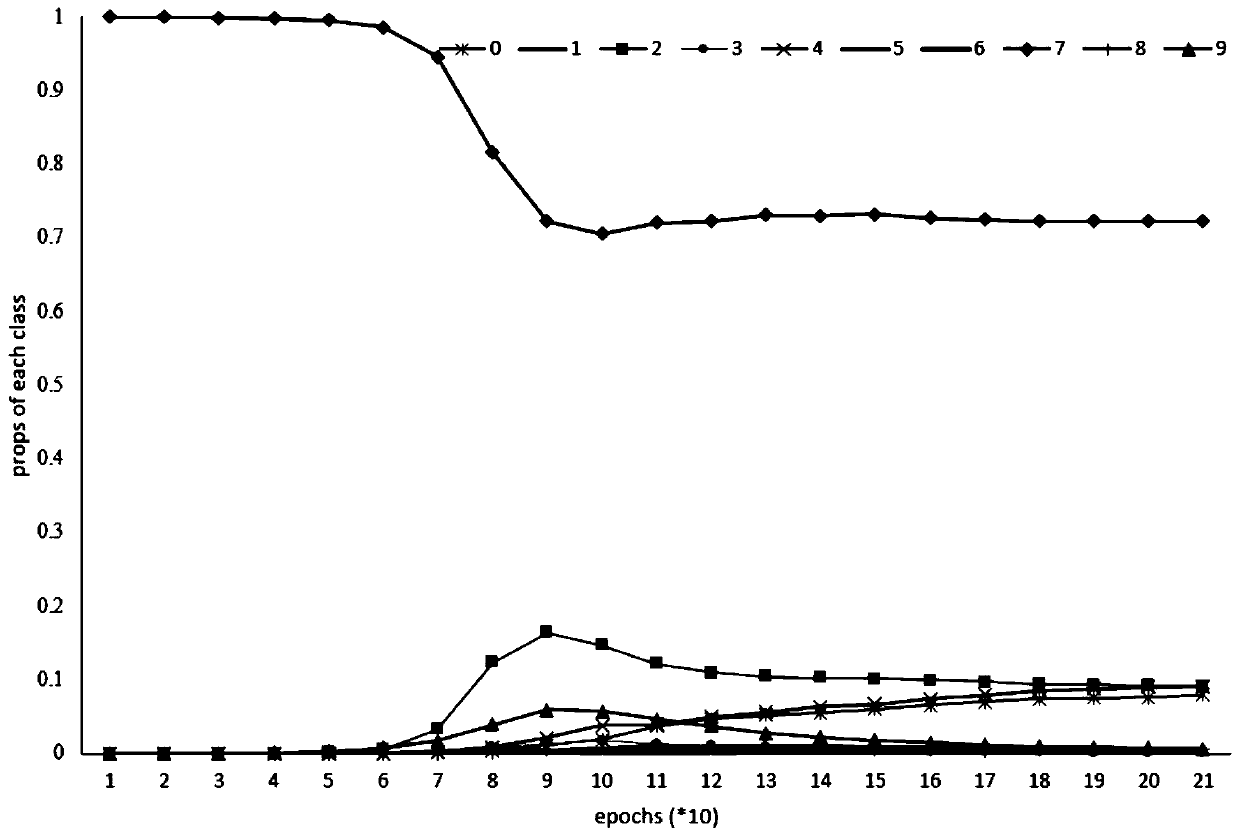
[0039] Step 3: The sender according to each set of secret information b i ∈{0,1},i=1,2,…,k, where k must not be great...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com