A method for node access management and authentication in a mobile environment
A technology of access management and environment, applied in the direction of electrical digital data processing, encryption device with shift register/memory, instrument, etc., can solve problems such as synchronization and interference, and achieve the effect of ensuring reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
[0021] The method for node access management and authentication under the mobile environment of the present invention comprises the following steps:
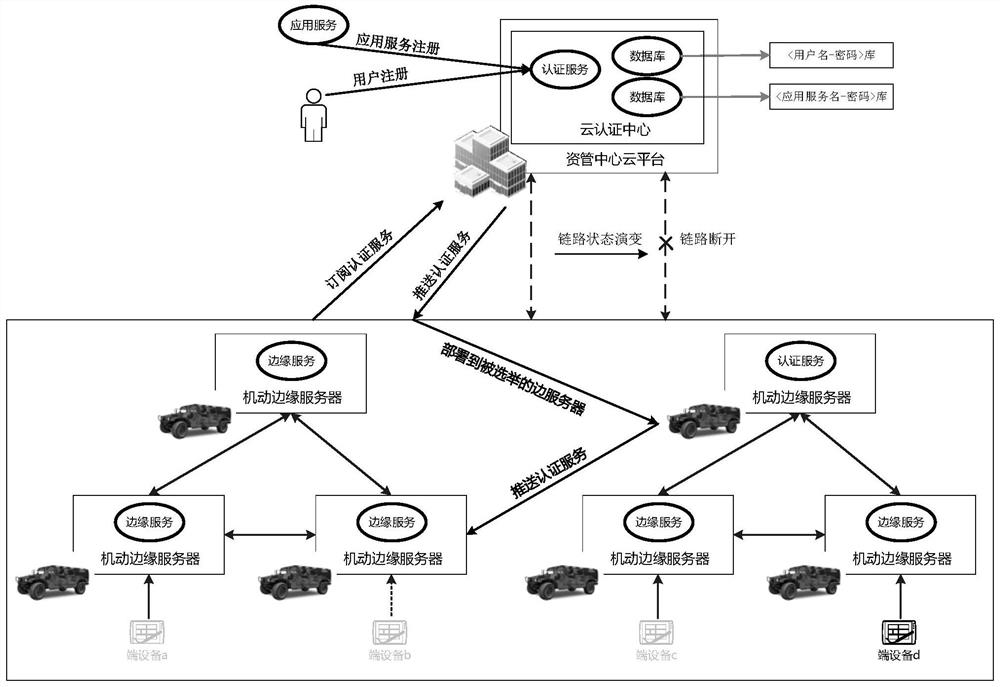
[0022] (a) Create an authentication service based on the serverless architecture in the cloud authentication center (ie, the cloud), push and update the authentication service to the edge service node set according to the event trigger policy, and make the edge service node set subscribe to the cloud authentication center for authentication services.
[0023] In the cloud-edge fusion information service system, in order to deal with the risk that the set of edge service nodes may be disconnected from the cloud at any time and cannot provide authentication services, an efficient and available event-triggered edge authentication service creation and destruction architecture can be designed, such...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com