Teaching information safety protection system based on cloud platform
An information security and protection system technology, applied in the field of teaching information security protection system based on cloud platform, can solve the problems of malicious data theft, intentional leakage, and insufficient security of teaching information storage, so as to improve security and prevent malicious data The effect of stealing and not easily leaking information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
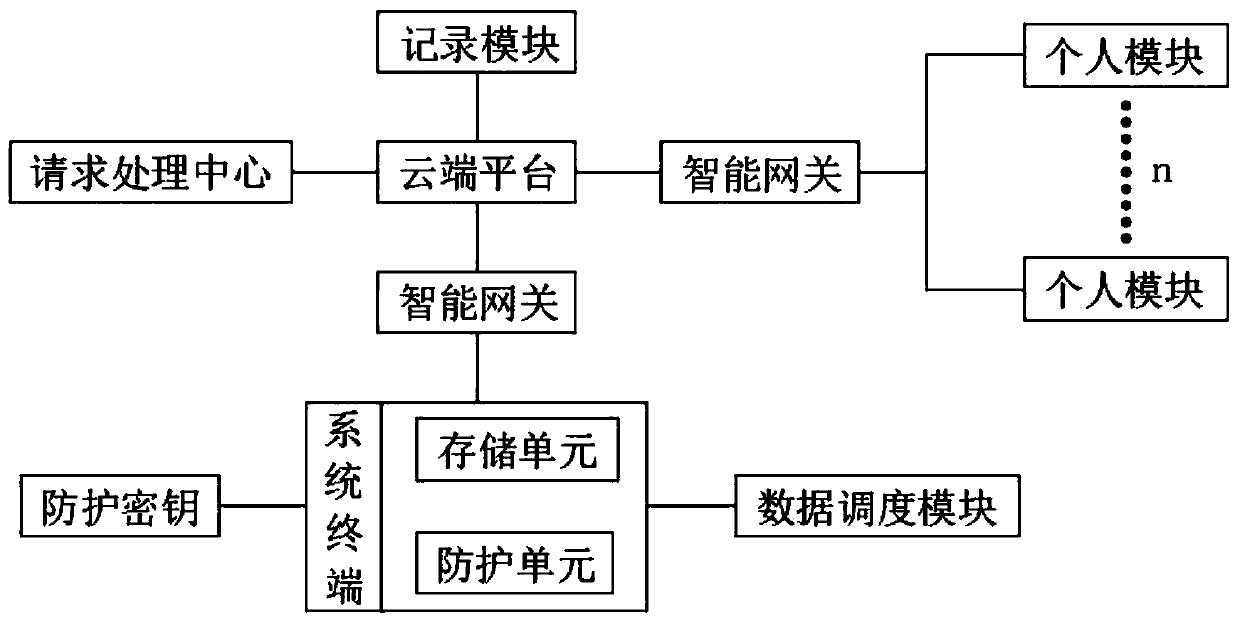
[0019] Such as figure 1 A teaching information security protection system based on a cloud platform is shown, including a cloud platform, a system terminal and multiple personal modules;
[0020] An intelligent gateway is connected between the cloud platform, the system terminal and the personal module, and the intelligent gateway is used to connect the cloud platform, the system terminal and the personal module for data exchange and transmission, and to control the connection between the cloud platform and the system terminal. On and off of the connection;
[0021] The personal module is used to log into the cloud platform, and is configured with login authentication, including ID verification, fingerprint verification and face verification, and sends data requests and transmits data instructions to the cloud platform;
[0022] The system terminal includes a storage unit and a protection unit, the storage unit is used to store teaching information in the system, the protecti...
Embodiment 2
[0031] Including a cloud platform, a system terminal, a plurality of personal modules and a recording module, the cloud platform is specifically a computing cloud platform focusing on data processing, and the system terminal is specifically a storage cloud platform mainly focusing on data storage;
[0032] An intelligent gateway is connected between the cloud platform, the system terminal and the personal module, and the intelligent gateway is used to connect the cloud platform, the system terminal and the personal module for data exchange and transmission, and to control the connection between the cloud platform and the system terminal. On and off of the connection;
[0033] The personal module is used to log into the cloud platform, and is configured with login authentication, including ID verification, fingerprint verification and face verification, and sends data requests and transmits data instructions to the cloud platform;
[0034] The system terminal includes a storage...
Embodiment 3
[0039] On the basis of Embodiment 1, the system terminal is also connected with a protection key, and the protection key is used to encrypt the entire system terminal. The encrypted key is multi-segment, and the specific number is the number of the personal modules. The key is uniformly input by the holder of the personal module, and the protection key is used for security verification of data modification in the storage unit;
[0040] When the data in the storage unit is modified, the protection key needs to be verified, and the protection key is uniformly generated for all personal modules in the system, which is different from the randomly generated key when downloading. It remains unchanged before the system is modified;
[0041] When modifying data, all personal modules in the system need to be online at the same time, and the keys of all personal modules must be obtained. After the cloud platform obtains all the keys, it will summarize the keys according to the order of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com