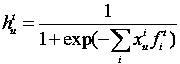Risk user identification method and system, storage medium and equipment
A user identification and user technology, applied in the field of webcasting, can solve the problem of low risk user identification accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
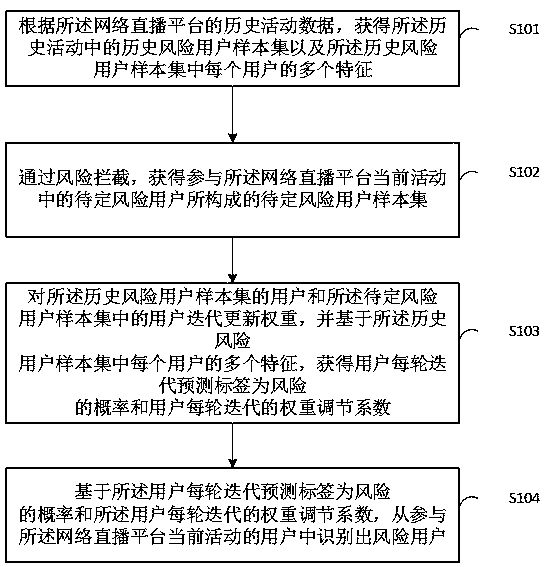
[0057] This implementation provides a method for identifying risky users, which is used on the webcast platform, see figure 1 , the method of this embodiment includes the following steps:
[0058] S101. According to the historical activity data of the webcast platform, obtain a historical risk user sample set in the historical activity and multiple characteristics of each user in the historical risk user sample set;
[0059] S102. Through risk interception, obtain a sample set of undetermined risk users composed of undetermined risk users participating in the current activities of the webcast platform;
[0060] S103. Iteratively update the weights of the users in the historical risk user sample set and the users in the undetermined risk user sample set, and based on the multiple characteristics of each user in the historical risk user sample set, obtain the user's iteration prediction label for each round Adjust the coefficient for the probability of risk and the weight of ea...
Embodiment 2
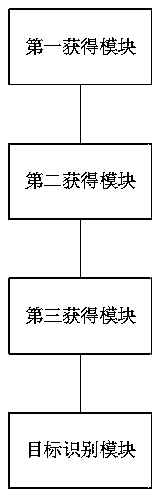
[0145] Based on the same inventive concept as in Embodiment 1, this embodiment provides a system for identifying risky users, which is used on a webcast platform, see figure 2 , the system includes:
[0146] The first obtaining module is used to obtain the historical risk user sample set in the historical activity and multiple characteristics of each user in the historical risk user sample set according to the historical activity data of the webcast platform;
[0147] The second acquisition module is used to obtain a sample set of undetermined risk users who participate in the current activities of the webcast platform through risk interception and constitute undetermined risk users;
[0148] The third obtaining module is configured to iteratively update the weights of the users in the historical risk user sample set and the users in the pending risk user sample set, and obtain users based on multiple characteristics of each user in the historical risk user sample set The pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com