High-speed privacy amplification method for supporting large-scale input blocks in quantum key distribution system
A technology of quantum key distribution and security enhancement, which is applied to key distribution, can solve the problems of large-scale input processing, reduction of calculation speed and calculation accuracy, and inability to meet the quantum key distribution system, so as to improve system security and reduce limited The code length effect and the effect of improving the throughput rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
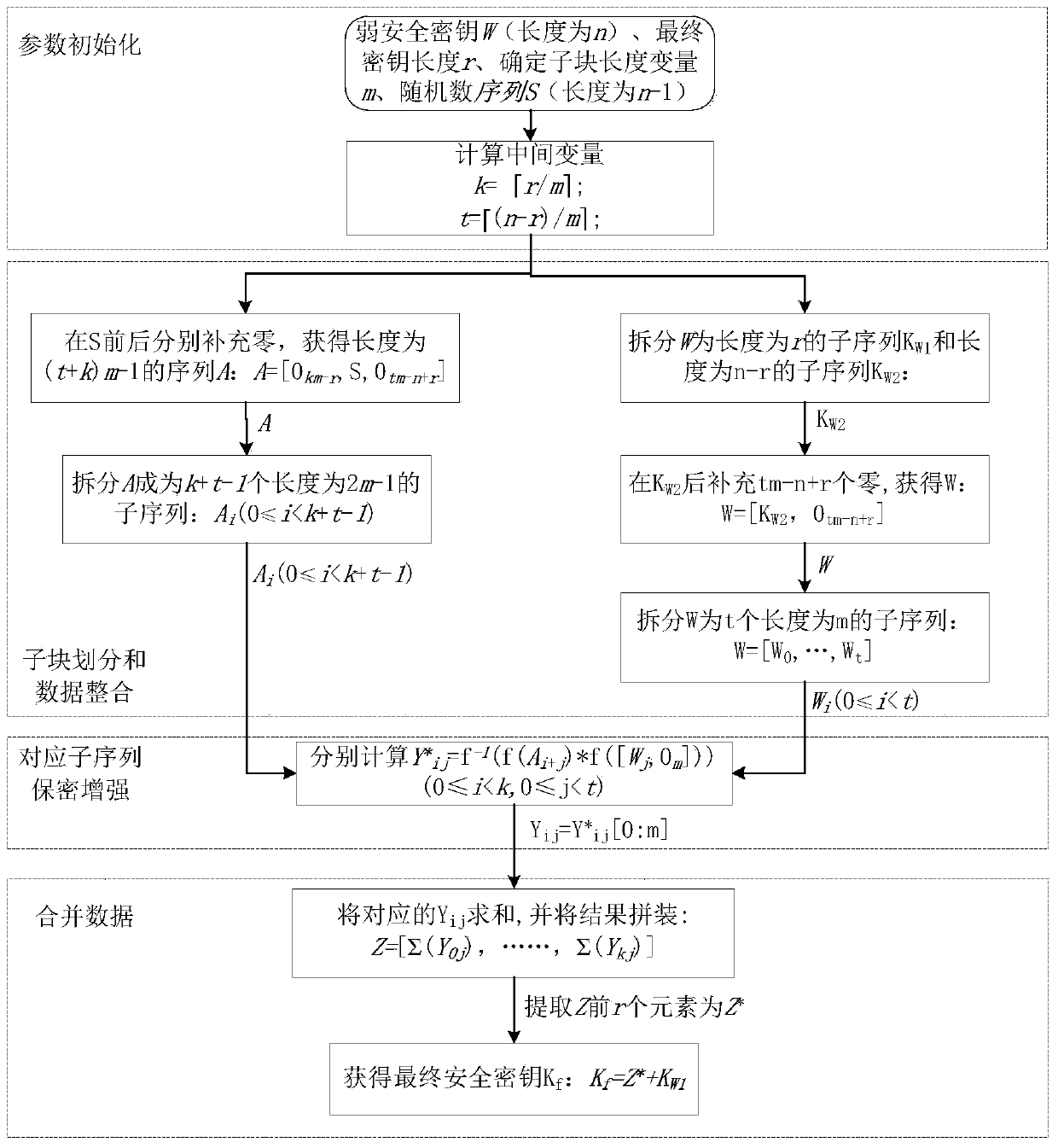
[0029] The present invention uses a simplified Toeplitz matrix as a general hash function family, and on this basis, splits the Toeplitz matrix into a plurality of sub-blocks of the same size, and uses fast Fourier transform to accelerate the corresponding Toeplitz matrix blocks respectively. product. That is, by splitting the Toeplitz matrix and using FFT for each sub-block to accelerate, the input scale of FFT is reduced from n to 2m-1. After the operation is divided into multiple sub-parts, the calculations among the multiple sub-parts are independent of each other, so further acceleration can be achieved in a parallel manner.
[0030] In specific application examples, such as figure 1 As shown, the present invention is used in a quantum key distribution system to support a high-speed security enhancement method for large-scale i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com