A confidence-based network security alarm processing method
A processing method and network security technology, applied in the field of network security, can solve problems such as uselessness, and achieve the effect of reducing data volume and speeding up
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
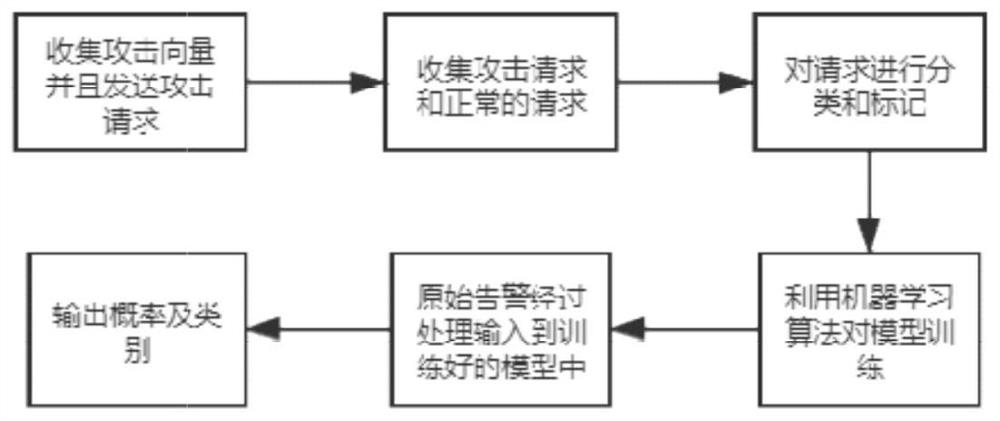
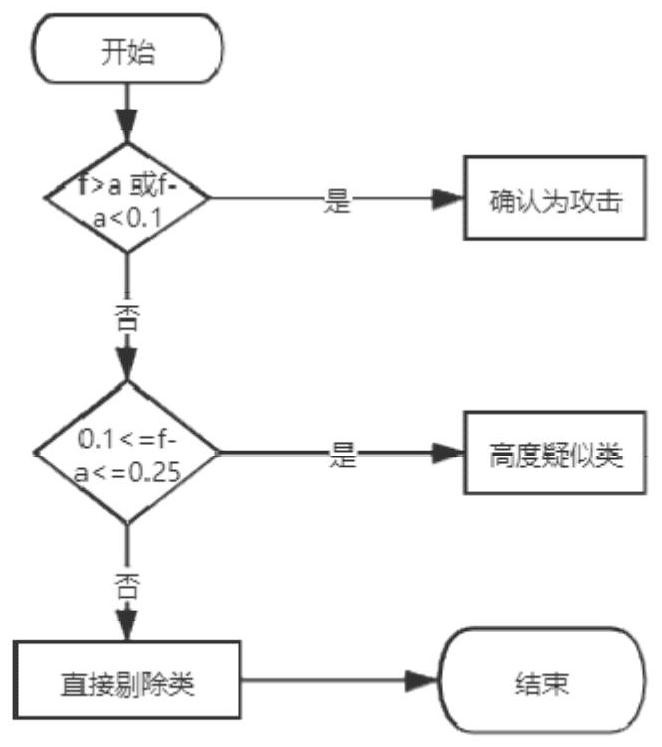
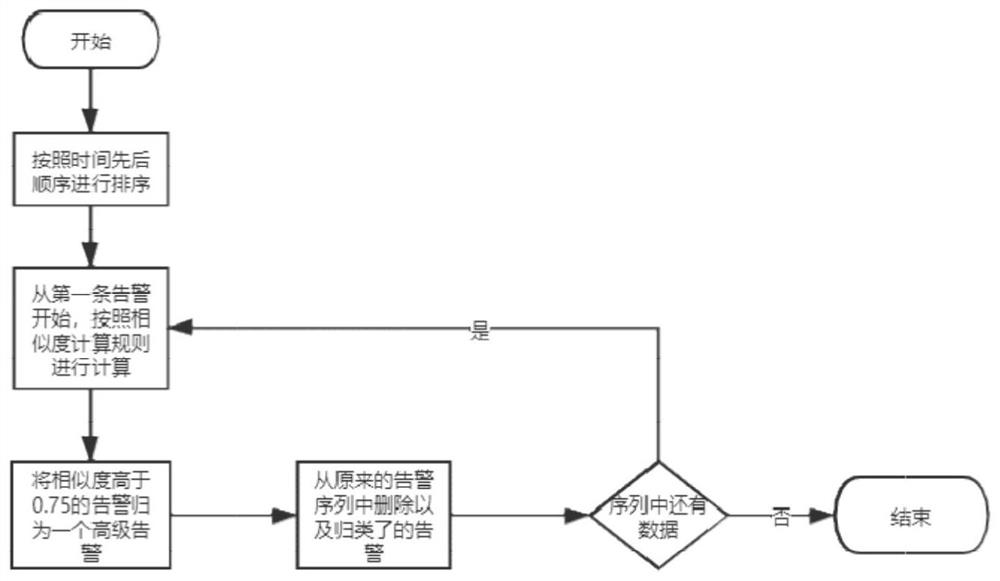
[0042] A confidence-based network security alarm processing method. It is characterized in that the alarm confidence level of network security alarms is obtained through machine learning. First, machine learning algorithms are used to build machine learning models. The algorithms used include but are not limited to LSTM, CNN and other algorithms, and then attack requests collected from the network are used to With normal requests, the training model obtains a model with better classification effect, and the built models are all regression models. Input the original request that triggered the alarm into the machine learning model for model recognition and evaluation. The model scores the raw data of a single alarm to determine whether it is an attack, the type of attack, and the probability of an attack. The probability score output by the model is the confidence level of the alarm. According to the accuracy of the model, the alarms are graded, and the alarms are divided into ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com