Malicious code homology analysis method based on graph convolution network and topic model
A homology analysis, malicious code technology, applied in the field of deep learning and information security, to achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
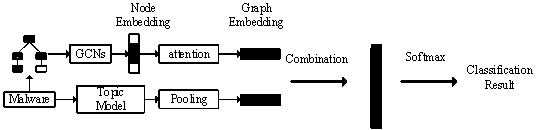
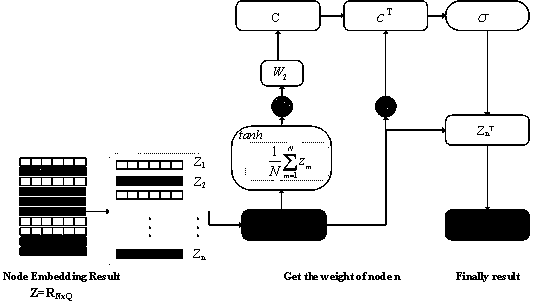
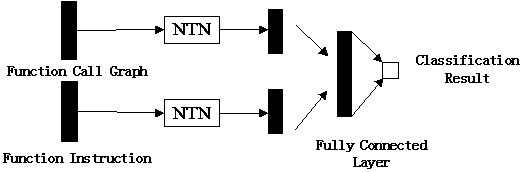
[0015] The invention is based on the homology analysis of the malicious code of the graph convolutional network and the theme model, and is mainly aimed at the binary PE malicious code under Windows. First extract the function call graph and function instruction distribution features of the malware, and then input the features processed by the topic model and attention mechanism into the Neural Tensor Network (NTN) to obtain the combined mixed features, and finally use the graph convolutional network to perform family Classification. In order to further illustrate the specific implementation of the present invention, it will be described in detail in conjunction with the accompanying drawings. The present invention proposes a malicious code homology analysis method based on a graph convolutional network and a topic model, which can effectively classify existing malicious codes into families and determine the family category of newly added malicious codes.
[0016] Extract the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com